Computer systems in schools. Shvidkodiya merezhі to deposit in the number of connected computers. The more computers are connected to the merezhі, the better it is to transfer information from the computer to another. Distinguish physical and logical topology. Logiches
Ivanov Arkady
Presentation about those who made the school merezha
Zavantage:
Front view:
To speed up the presentation ahead of time, create your own Google Post and see before: https://accounts.google.com
Captions before slides:
Vikonav: Lesson 10 "A" to the class Ivanov Arkadij COMPUTER OF THE MEREZHA AT THE SCHOOL
1. Understanding the computer of a network A computer of a network is a group of computers united by each other to provide shared access to resources and exchange of information. To the hardware storage computer system, there is also a communication facility that allows you to unite okre segments and networks and organize information flows. On this day, for the installation of computers, the most common lines of communication are available in the region: all cables (coaxial, twisted pair), telephone lines, fiber optic lines, radio communications zok, including satellite links.
Classification of computer networks Computer networks can be divided into local and global ones. Local computer of a fence - a computer of a border for a fenced stake of coristuvachs, which unites computers in one place or at the borders of one enterprise. To exit from the light information space, it is necessary to connect to the global computer network, found at home on the Internet. The Internet is an all-world information computer network.
The meaning of the world The local computer network allows you to effectively organize the exchange of information in the middle of the surrounding organization. Local companies give their employees such services as a collection of files for collective work, and a collection of resource resources (for example, printers). Internet can win in different areas: - Professional activity; - commercial activity; - Otrimannya osvіtnіh services; - vіdpochinok and roses.
2. The structure of the topology of a school network Whether a computer network is characterized by topology, protocols, interfaces, networking technical and software features. Topology is the only way to connect computers at the edge. There are impersonal methods for building framing outbuildings, from which you can see five basic topologies: bus, ring, star, porous topology and grati. Other methods are combinations of basic ones. In a wild way, such topologies are called mixed or hybrid (here, for hyperpossibility, you can go to theory, as if you would be in a movie)
Scheme of local borders at school - koristuvach; - WiFi point; - bezdrotovoe z'єdnannya (wifi); - modem; - provіdne z'єdnannya (twisted pair);
Laying out the mesh
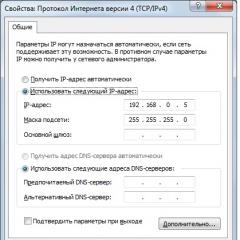
1) Set the Ethernet adapter of your computer to a static IP address in the 192.168.1.x subdivision (for Windows7: Control Panel\Merezha and Internet\Connection Merezhі, in the authorities of the local network in the authorities of the Internet protocol version 4 (TCP/IPv4) ) tweak the static settings: for example, the IP addresses are 192.168.1.100 and the mask is 255.255.255.0).
2) Launch a Web browser. Enter the IP address of your address string by default (192.168.1.20). At the field that appeared, enter your login and password, for the ubnt/ubnt upgrades.
Step 1: Configuring the base station 1) Under the Network tab, set the Network Mode item to Bridge mode 2) Under the Management IP Address item, select DHCP, so the parameters are automatically seen by the DHCP server. If you set it to static, choose Static and write it in the IP Address item, the address of our add-on. Gateway IP has a promotional gateway. Primary DNS has the IP address of the DNS server or the address of the gateway.
Go to the WIRELESS tab 1) At the Wireless Mode item, select Acess Point and check the WDS (Wireless Distribution Protocol) checkbox. 2) At the SSID item, enter the identifier of the wireless mesh. 3) At the Channel Width item, specify the width of the channel (mobile devices use only 20 MHz smoothies)
4) At the point Security, select the type of encryption, and enter the authentication password
Step 2: Configuring the repeater station 1) Under the Network tab, set the Network Mode item to Bridge mode 2) Under the Management IP Address option, select DHCP, which is automatically configured by the DHCP server. If you set it to static, choose Static and write it in the IP Address item, the address of our add-on. Gateway IP has a promotional gateway. Primary DNS has the IP address of the DNS server or the address of the gateway. 3) Pressing change, picking up the fix.
Go to the WIRELESS tab 1) At the Wireless Mode item, select Ap-Repeater and check the WDS checkbox. At the WDS Peers point, write the MAC - the address of the first station
Minuses of school local networks and Internet networks Width of the power server. Vіdsutnіst severnoї or hocha b laborantskoї іz severnoyu filthy signal bezdrotovogo z'єdnannya through tоstі stіni. There are no benefits for good fencing
Scheme of a possible local network 2 on top - access point (router); - Drotova z'ednannya (vita pair); - bezdrotove z'ednannya; - you can place server 2 or 3 on top; - Koristuvach; - modem (switch);
Development of the project in the future Camera, good server, FTP server, file exchanger
Nashtuvannya connection to the fence
Configuring the point How to get to the parameters of the point (typed in the address bar of the browser the ip-address of the point)
Set the IP address of the access point
Adjusting the power of the measure (choose the mode of the robotic point (type of distribution of the signal), select the mac-address of the attached devices (another point, modem, ...) to the tsієї point and the password for connecting to Wi-Fi).
Setting up 2-channel Wi-Fi
Resetting a password to enter the point
Command line swipe list Ping and in. (3-4 slides with screenshots, maybe a demonstration)
ping PING.EXE - the most common command line utility. It is used in all versions of all operating systems with a supportive measure and we will forgive that by hand, the node is supported by its name or by its IP address.
Ipconfig/all The IPCONFIG command is used to change the flow settings for the TCP/IP protocol and to update some of the parameters that are set during automatic configuration of the network interfaces at the time of the change to the Dynamic Host Configuration Protocol (DHCP).
TRACERT, like before, is the most widely used tool for lace diagnostics. The utility allows you to select a node node, through which it is possible to pass an IP packet addressing the terminal node. The basis of the routing is based on the method of analysis of replies during the last ICMP packets sent to the specified address with 1 TTL field, which is greater. Tracert
Netstat Quizzes for displaying TCP and UDP calls, listening ports, routing tables, statistics for various protocols.
Getmac Command The GETMAC command line utility is available on Windows XP versions and older. Vykorivuetsya for otrimannya hardware address merezhevyh adapters (MAC-address) both on the local and on the remote computer.
Select provider
Perspectives of the future Zavantazhuvati 30 films per second will be possible in 2020. A group of contributors from the British University of Surrey has achieved a record high speed of data transmission for dartless nets. Practicing over the standard 5G connection, we can reach a speed of 1 Tb / s, which allows us to capture, for example, 100 films in 3 seconds. © «Komersant-Online» The British University of Surrey Achievements Group has set a record for the speed of data transmission by wire ropes. Taking care of the new generation 5G communication standard, they could reach a speed of 1 Tb / s (or 125 GB / s). In such a rank, it was crossed in front of the reach, installed by the Pivden-Korean scribe Samsung at the same time of the past fate. The same Pivdenno-Korean company has perfected the Wi-Fi technology, which allowed transferring data on speed up to 575 MB/s. Therefore, the latest reach of British retailers has allowed to exceed the maximum data transmission speed of Samsung by more than 200 times, and the average speed of data transmission by 4G networks - by 65 thousand. razіv. READ ALSO Quantum streak preview 5G commercial launch predicted for 2020 Also, the University of Surrey wants to start testing in large areas in 2018. The introduction of a new standard allows, for example, to capture 100 films in 3 seconds. In addition, such a speed of data transfer will help significantly speed up the timing of the delay in the timing of financial operations, or to facilitate the improvement of sleeping cities with a high graphic distribution of buildings between short smartphones. Crimia is free of charge for transmitting data on 5G networks, it will operate at the lowest working frequencies, the range of which will be beyond 6 GHz. In addition, MIMO technology will be used in them, the essence of which is based on different types of antennas, both on the sides that receive and transmit the signal.
The design of the computer system of the school is an even more important task. Here you need a mother as a material resource and the presence of the necessary premises for the administration, and the knowledge of the administration itself and the cleverness of designing for the improvement of this situation. It is also necessary to keep abreast of new products from the owner of the land.
Administration Administration of a system of servers and a complex of calls to ensure normal operation of software and hardware components in a local area and server pressures, assisting in the identified faults and organizing an effective defense against possible threats . Administrative tools - software and hardware tools that ensure the security policy. A system administrator (also known as an IT administrator) is a specialist who maintains the correct operation of computer technology and software security, as well as vouches for the information security of the organization. In connection with active technology and computerization of all commercial companies and state institutions, the profession of a system administrator is required at once.
Bus topology Bus topology (div. Fig. 1) supports the connection of all tether nodes in a peer-to-peer network behind a single open-ended cable. The cable is to blame for the termination of resistive voltages - the so-called termination resistors (terminating resistors). A single cable can only trim one channel. In this topology, the cable is called a bus. Buduєtsya on the basis of coaxial cable. Qiu topology is more likely to zastosovuvat less for small local meshes.
Figure 1. - An example of a bus topology Since the addresses are not being picked up, the signal has gone.
Kiltsev topology Previously, it was implemented in simple peer-to-peer local networks. The secret scheme of the confinement predicted a closed circle. Data were passed on to only one directly. The skin working station acted as a repeater, receiving and retransmitting packets to the address of the packet and transmitting the solution of the packets to the advancing working station, spread out “below the flow”. In the cob variant of the ring topology of local networks, the peer-to-peer network between the working stations was established. Shards of this type of confinement had a small ring shape, the stench was called closed.
Figure 2. – Kiltseva topology The transfer of local networks of the first transferring the hour of transmission to the packet to the addressee. The more extensions are connected to the ring, the more the interval of the trim. Nedolіk kіl'tsevoї topology і ї tsomu, scho z vyhodі z fret odnієї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї ї stannya pripinyaє funktsionuvat yom mezhu.
Topology of the «zirka» type On vіdmіnu vіd kіltsevyh topologies, physical chi virtual leather edging outbuilding is given the right of independent access to the middle of transmission. Whether any attachment can be obtained from a request for access to the middle of the transmission independently from other attachments.
Malyunok 3. – Topology of the type of star Star-like topology is widely found in contemporary local fringes. The reason for such popularity is flexibility, feasibility of expansion, and a perceptibly low variability of throatiness, combined with collapsible topologies of local borders and suvorimi methods of access to the middle of data transmission.
Figure 4. - Porous topology Porous topology - the basic topology of the computer network, in which the skin working stations of the network are connected with other working stations in the network. It is characterized by high durability up to widm, foldability of lashing and overhead wired cable. A leather computer can have a lot of possibilities to connect with other computers. Shaving the cable will not be done until the connection between two computers is spent.
Lattice - understanding of the theory of organization of computer networks. The topology, in which universities are established, are regular rich gratifications. With any skin, the rib of the lattice is parallel to the її axis and to the rear two summіzhnі vuzli vzdovzh tsієї osі. The one-world "lattice" is a whole lanciug, which connects two zvnіshnі vuzli (mayut only one susіda) through a deak of a number of internal ones (they have two suіdіs - levoruch and right-hander). When both call nodes are connected, the “ring” topology emerges. Two trivi- mers are victorious in the architecture of supercomputers.
Diploma
Computer science, cybernetics and programming
Creation of a local security system and the installation of a system for access to the Internet security system, a billing system for control; Vіlne podklyuchennya quiet, hto navchaєtsya to the resources of the Internet, only in primary purposes; The choice of possession is to blame for the foundations on the technical characteristics, the building satisfaction, and the speed of data transmission.
Entry
For the task of the graduation project, it is necessary to design a local calculation for the school office of informatics with the improvement of standards and encourage a measure of the design features of life.
The local enumeration measure (LAN) represents communication system, which connects computers and setup, which connects to them in the surrounding area, call no more than one enterprise or a dekilkoh budivel. In the present hour, LOM has become an invisible attribute in any numbering systems that can have more than one computer.
Perevagi local merezhi - tse, persh for everything, centralized data savings, the possibility of joint work and exchange of data, access to joint resources, such as printers, Internet and other.
Another important function of the local border is the creation of airborne systems, which continue to function when certain elements go out of tune, which enter before them. At LOM, the viability is protected by the way of duplication, supremacy and flexibility of robots and personal computers.
The greatness of the ability of computers from the processing of information to make them adjuncts for a variety of applications in the field of education. The stench can make it easier to learn that reading material on all equals in preschoolers, as a way of reading, to learn the senior classes and the highest primary mortgages. Computers are used for voicing in such areas as history and natural sciences, professional training, Russian language and mathematics, music and figurative art, reading and writing. Computers open up new ways for the development of new skills and solve problems, give new opportunities for learning. For the help of computers, it is possible to carry out lessons, right, control work, and also the appearance of success is more simple and demonic. Tse help teachers and allow them to deprive them of more than an hour to occupy. Computers can generate a lot of lessons in clicks and knowledge, and all the flow of information is easily accessible.
At the moment, the theme of the project is up to date, the fragments of the development of local structures are not at the stage when designing whether there will be any buildings in the form of offices and initial mortgages to shopping centers, as they will be at any time.
Zgіdno z vihіdnimi dannymi, svoryuvana іnformatsiyno-calculating system budіvlі not recognized for the transmission of secret information. Therefore, the cable system is structured on a more cheap and less foldable practical implementation of an unprotected element base.
The revision of all the tasks set in the beginning will be celebrated with the improvement of the current standards of the cabling systems on the basis of the initial office plan.
As a result of the completion of the graduation project, a local calculation of the main office can be designed, as well as hand-made at the fitting, installed and vikoristanny. Also, the wiring of the cables was carried out, which connected the information sockets, and that the switching equipment was installed for the functioning of the entire system.
1 Development of a technical project
1.1 External data
For the purpose of working on the creation of local networks and the establishment of access for students to the Internet, the following is approved:
- Creation of a local security system and the installation of a system for access to the Internet security system, a billing system for control;
- Vіlne podklyuchennya quiet, hto navchaєtsya to the resources of the Internet, only in primary purposes;
- Vybіr obladnannya may be based on the technical characteristics, building satisfaction, and the security of data transmission;
- We are guilty of being safe, stealing from people with an electric jet, not guilty of creating electrical faults at the fence. The rіven elektromagnіtnіh vipromіnіuvan mає perevischuvati vstanovіnі sanitary norms;
- The smallest number of working stations at the office may be more than ten;
- The skin working station is connected to a mother socket with an RJ-45 socket and the skin station can be a mother wired adapter, which is connected to the system board;
- At the skin working station for connecting to the wire, a wire cable with RJ45 roses on the ends is to be blamed;
- A working station, like a robotic space, can be a full-time computer or a laptop;
- Availability of wi-fi in the whole office;
- Raztashuvannya robochih mіsts may vіdpovіdat vymogami standіv v zmіschennya obladnannya v navchalnyh mortgages;
- The local area may have both stationary and portable computers;
- Vitrati creation of local networks may be minimized;
- Superficiality of the local dimension.
1.2 Follow-up of the main decisions for future measures
Whether it be a merezhny attachment, a switch, a router, a merezhna card of a computer, you can create an OSI model for your work, which is made up of seven equals. Rivets are rolled up from the bottom uphill, on the first, the lowest one, the physical row is rolled, on the other, higher equal, the applied rope is rolled.
Merezhev's OSI model is an abstract model for communication and creation of mesh protocols. In the structure of the skin, the part of the process interacts with each other. Zavdyaki її vykoristannya vzaєmodіya zaєmodіya software zabezpechennya ta merezhovogo obladnannya staє richly simple and clear.
Table 1 describes the OSI mesh model for the assigned functions of the skin layer. Rivnі roztashovuyutsya beast to the bottom, starting from somgo to first.
Table 1 | Merezheva OSI model
|
OSI Model |
||
|
data type |
Riven (layer) |
|
|
7. Application |
Access to merged services |
|
|
6. Presentation |
Giving and coding data |
|
|
5. Session |
Call session management |
|
|
Segmenti |
4. Transport |
Direct connection between terminal points and superiority |
|
3. Merezheviy (network) |
Route assignment and logical addressing |
|
|
2. Duct (data link) |
Physical addressing |
|
|
1. Physical (physical) |
Robot with transmission medium, signals and dual data |
|
1.3 Principles of SCS administration
The principles of administration of the SCM are largely determined by the structure. There are two types of single-point administration and a multi-point administration.
Under rich-dot administrators, it is necessary to understand the management of a structured cable system, inspired by the architecture of an archi- cal view, so that it turns on the main subsystem even if it is the same. The main sign of this option is the need to switch at least two cords (or elements that replace them), so that you can change the configuration. With the victorious principle, the greatest flexibility of management is ensured, as well as the ability of SCS to be increased when adapting to new programs.
The architecture of a single-point administration is victorious only, if it is necessary to simplify the management of the SCS as much as possible. The main sign of the installation of all information outlets of working areas with possession in one technical area. Principally similar architecture can be vikoristovuvatisya less than cable systems, like a backbone subsystem. One-point architecture is better to vikoristovuvat in merezh with a small number of ports.
In this project, the backbone subsystem is not transferred, all computers of the local network and commutation are not located in one office, and also, the architecture of a single-point administration is stagnant.
1.4 Inspection and choice of topology
The term "topology", or "topology of the mesh", characterizes the physical distribution of computers, cables and other components in the mesh. Topology is a standard term, which is used by professionals when describing the main layout of a mesh.
The topology of the mesh is zoomed in by showcases. Zokrema vibіr tієї chi іnshої topologiiї vplivaє:
- warehouse of the necessary merezhnogo statkuvannya;
- characteristics of the merezhny installation;
- the possibility of expanding the measure;
- a way to care for the mesh.
In order to split resources or to build other resources, the computers are connected one to one. For tsієї meti zastosovuvatimetya cable.
However, simply connecting the computer to the cable connecting other computers is not enough. Different types of cables in combination with different fencing boards, fencing operating systems and other components require different interfacing of computers.
The skin topology of the mesh imposes low minds. For example, you can dictate the type of cable, and the method of laying it.
Topology can also determine how computers interact with each other. To different types of topology, different methods of interdependence should be given, and these methods should also be added to the mesh.
The measures will be based on three basic topologies:
- tire;
- zirka;
- ring.
When a computer is connected to a single cable (segment), the topology is called a bus. In that case, if the computers are connected to the cable segments that go from one point or the hub, the topology is called a star. If the cable, to which computer is connected, is closed in the ring, such a topology is called the ring.
Wanting to use the power of the basic topology to be clumsy, it is true that they often try to achieve foldable combinations that will increase the power of many topologies.
1.4.1 Bus topology
The "bus" topology is often called the "line bus". Tsya topology goes to the simplest and widest topologies. It has one cable, which is called the backbone or a segment, which connects all the computers of the network (Fig. 1).
Figure 1 Simple mesh with bus topology
In a network with a topology, the "bus" of the computer addresses the data of a particular computer, transmitting them over the cable as electrical signals.
Data like electrical signals are transmitted to all computers of the merezhi; however, the information is received only if the address of the owner is encrypted in these signals. Moreover, at the moment of the skin, only one computer can transmit.
The amount of data in the measure is transmitted by only one computer, and the productivity of the deposit is the number of computers connected to the bus. The more, the more computers, the more the transmissions, the more we work.
However, it is not possible to conduct a direct fallow between the throughput capacity of the city and the number of computers. Bo, krіm number of computers, on swidkodіyu merezhі vplyvaє impersonal factors, zokrema:
- characteristics of the hardware security of the computers in the merezhi;
- the frequency with which computer is transmitting data;
- type of practical merging accessories;
- type of merezhe cable;
- stand between computers at the merezhі.
The bus is a passive topology. This means that the computers are less likely to “listen” to the data that are transmitted by the measure, but not to move them to the right of control. To that, if one of the computers is in harmony, it is not possible to appear on steel robots. In active topologies, computers regenerate signals and transmit them over and over.
In case of failures, if there are malfunctions in the measure, the computers themselves become overused in practice, and the docks are broken, the stench cannot interact one by one.
Features of bus topology:
- ease of installation;
- noteworthy is the ease of installation and the low cost, as all the working stations are re-stashed;
- Went out of the fret of one or the other few working stations in any way do not fit on all robots.
Shortcomings of the "bus" topology:
- bus failures in any place (shaving the cable, breaking the fret of the tethered connector) lead to the impracticality of the tether;
- skladnіst look for faults;
- low productivity at the same time, only one computer can transmit data in a measure, with an increase in the number of working stations, the productivity of a measure falls;
- bad scalability for adding new working stations, it is necessary to replace the old busbars.
If you look at this topology, that manifestation is short, it is clear that for the implementation of the project it is not the best option through those that are not suitable for it to upgrade computers to standards, as well as low reliability and scale ist not satisfied with the help of the project.
1.4.2 Ring topology
With the "loop" topology, the computers are connected to the cable closed in the loop. Therefore, the cable simply cannot be used for a long time, until you need to connect a terminator (Figure 2). The signals are transmitted in a circle in one straight line and pass through the skin computer. On the view of the passive topology of the "bus", here the skin computer acts as a repeater, forcibly transmitting signals to the attacking computer. To that, one computer is in harmony, pripinyaє to function all the mesh.

Figure 2 Simple mesh with "ring" topology
Advantages of ring topology:
- ease of installation;
- Practically, there is a total presence of the supplementary possession;
- feasibility of stable operation without an accidental drop in the speed of transmission in case of intensive entanglement.
However, the "kiltse" may and there are shortcomings:
- skin working station can take an active part in the transmission of information; at the time of the exit, I want to use one of them, or I will cut the cable of the robot all the way;
- connection of a new working station with a short-line mic, shards for the hour of installing a new PC ring may be rozimknene;
- folding configuration and customization;
- skladnіst look for inaccuracies.
Having looked at this topology, it is clear that it is not suitable for the implementation of the project of the head office.
First of all, there can be a low stamina to the top.
In another way, if she worked out, all the computers in the office may be turned on, but do not need to be turned on.
1.4.3 Topology of the star
With a "mirror" topology, all computers behind an auxiliary cable segment are connected to the central component, which is called a hub (Figure 3). The signals from the computer that are being transmitted must go through the hub to all others. Tsya vinyl topology at the dawn of computational technology, if the computers were connected to the central, head computer.

Malyunok 3 Simple mesh with topology "zirka"
At the wires with the “star” topology, the cable is connected to the configuration control of the centralized wire. Ale є і nedolіk: oskolki all kom'pyuteri connected to the central point, for large meshes significantly more wire cable. Until then, as the central component of the viide of the fret, the robot of all things will collapse.
And if you see more than one computer (or the cable that connects with the hub), the next computer cannot transmit or receive data as needed. There is no vpline on the edge of computers at the merezhі.
The topology of "zirka" on this day has become the main one in case of budding local merezhs. Tse became zavdyaki її numerical advantages:
- exit from the fret of one working station that the cable does not fit on all robots;
- external scalability: to connect a new working station, it is sufficient to lay an amine cable in front of the switch;
- light poshuk and the elimination of inaccuracies and shaving at the fence;
- high productivity;
- simplicity of nalashtuvannya and administration;
- at the merezh it is easy to get into dodatkove possession.
However, like topology, "star" is not spared shortcomings:
- departure from the fret of the central commutator will turn out to be unproductive in all measures;
- addendums on the treadmill are equipped - attachments, until all the computers of the tether (switch) will be connected;
- The number of working stations is surrounded by a number of ports at the central switch.
Having looked at the main topologies of the cabling system, their advantages and disadvantages, it was decided to choose the “star” topology. With the choice of a double-wire and a single switch, the topology will be the best solutions for encouraging a small office of informatics.
1.4.4 Topology combinations
In this hour, topologies are often victorious, like combining the layout of the mesh according to the principle of a bus, a star and a ring.
1.4.4.1 Mirror bus topology
Zirka-bus - the combination of topologies "tire" and "zirka". Most often, it looks like this: a sprat line from the “star” topology is connected behind an additional backbone line bus (Figure 4).
In this way, the way out of the fret of one computer does not flow into the mesh, other computers, like before, interact one by one. And if the fret of the concentrator is out of order, cause a zipper on the connections to the new computers and concentrators.

Malyunok 4 | Merezha with the topology "zirka-tire"
1.4.4.2 Topology
The zirka-kіltse is built something similar to the zirka-tire. In this, and in the other topology, the computers are connected to a hub, which actually forms a ring or a bus. It is important to note that the concentrators in the round bus are connected to the main line bus, and in the round bus, on the basis of the head concentrator, the stench is reduced (Figure 5).

Malyunok 5 | Merezha with topology "zirka-kiltse"
Take a look at the combinations of topology at the project, there is nothing to appreciate, shards of stink are more suitable for great merezha, and victoria in small ones is respected by undersized and dear ones.
2 Choice
For a complete work with files, an okremy computer is needed, which is a kind of binding to a file server. Documents are saved on the new one, access to which will be secured by a computer. Why, you need a commutator, so that you can combine computers into one segment. They gave a varto sign that one thing could help the presence of Wi-Fi before the LOM. To secure it, it is necessary to win a Wi-Fi router. In addition, for laying the wire, you will need the cable itself and sockets, as well as boxes to protect the darts from the dust. For merezhnoy obladnannya need a wardrobe.
Also, you can make visnovoks, which for the creation of local chains, it is necessary to have the following:
- file server;
- commutator;
- Wi-Fi router;
- mesh cable;
- boxes;
- information sockets;
- switching cabinet;
- kіtsev merezhev obladnannya - computers and laptops.
2.1 Router selection
Router (router) mesh attachments, which are victorious in computer data transmission meshes, which on the basis of information about the mesh topology (routing tables) and the first rules make a decision about transferring packets to the mesh layer of the OSI model. Sound zastosovuєtsya zv'yazku kіlkoh segmentіv merezhi.
There are 2 types of routers: software and hardware (software and hardware). The first one has a faulty part of the operating system of one of the computers, the other one has a special calculation outbuilding.
A hardware router is a specialization of attachments, selected for a high-specialized RISC processor or ARM, which is combined in a small case without any modules that are routed.
A software router is a working station or a vision server, which can have a few meshed interfaces and can have special software security, set up for routing.
Do not be surprised at those that the software router may have flexible functionality, lower hardware, in this project, there will not be a problem, so it will be less important and foldable for the vikoristan. Also, I had a chance to buy a Wi-Fi adapter . The software router, in addition, the computer, on which the installations are installed, should be changed, but it should be charged for electricity.
On the view of switches and bridges, in the routing tables of their add-ons, numbers and pidmerezh are recorded, and not MAC addresses. Another view is the active exchange with other routers of information about the topology of calls at the subdivisions, their throughput building and the station of channels.
The main features that are presented to the router in the project are functionality and security of work.
Most importantly, the security of the router's work is important, the shards will be connected to the new computer at once.
Functionality is characterized by a set of merging protocols, routing protocols, ports, Wi-fi. It is available for help using a modular design, if at one time a block of blocks with ports of the singing type is installed.
Heads of technology WiFi you can switch off from laptops, PDAs, stylist phones and other outbuildings with accessories WiFi to the Internet without connection to the wire cable.
WiFi allows you to develop a border without any material wiping by way of adding access points and priymachiv.
Wifi Perks:
- Allows the opening of the tether without laying the cable, you can change the variability of the opening and expansion of the tether. Mіstsya, where it is not possible to lay a cable, for example, the posture is placed in booths, which may have a historical value, can be served by dartless treadmills.
- Wi-Fi extensions are widely available in the market. And I can arrange different virobniks on the basic level of services.
- Wi-Fi measures support roaming, so the client station can move around the space, passing through one access point to another.
- Wi-Fi - the collection of global standards. On the basis of mobile phones, Wi-Fi can be used in different countries around the world.
Wi-Fi shortcomings:
- The frequency range and operational exchange in different countries is not the same. chime in WiFi - The router works in the 2.4 GHz band, and in this range there are no other attachments, such as attachments that support Bluetooth, but the electromagnetic summation is reduced.
- To finish high in accordance with lower standards of energy saving, which will change the hour of life of the batteries and increase the temperature of the building.
- Overlaying signals in closed or vicorist encryption of the access point and the open access point, which works on one or the other land channels, can override access to the open access point. This problem can be blamed on the large width of the access point.
2.1.1 Router selection
For equalization, three hardware routers from different manufacturers D-Link, TP-Link, Asus were taken with approximately equal var. Data about them is given in Table 2.
Table 2 Ratio of characteristics of routers
|
name |
D-Link DIR-506L |
TP Link TL-WR940N |
Asus RT-N53 |
|
Building permit |
|||
|
Defender of information |
WPA and WPA2, (WPS) PBC/PIN |
WEP, WPA, WPA2, 802.1x |
64-bit WEP, 128-bit WEP, WPA2-PSK, WPA-PSK, WPA-Enterprise, WPA2-Enterprise, WPS support |
|
Availability of Wi-Fi |
|||
|
Port speed |
10/100 Mbps |
100 Mbps |
100 Mbps |
|
Intermediate screen (FireWall) |
|||
|
NAT, DHCP server |
|||
|
Static routing |
|||
|
Web interface |
Browser Based |
||
|
Number of ports |
|||
|
Rosemary (WxHxD) |
102.9x79.8x22.3mm |
200x28x140mm |
172x145x60mm |
A router was collected for pіvnyannya TP-Link TL-WR940N may be suitable for the same characteristics and relatively low variability. The passport of which I will attach submissions to the addendum A.
2.2 Switch selection
Additions to the canal level, which allow you to combine a sprig of physical segments in a local line into one large line. Switching of local lines secures interdependence of the line extensions in the seen line without violating the collisions, with the parallel transmission of decals of data flows.
One of the main characteristics of the switch is the number of ports, it determines the number of computers that are connected.
In the capacity of the commutation possession, the commutator, and not the concentrator, is used, so for the price of the stench they are practically not disturbed, but the commutators may have a number of advantages:
1) increase the throughput capacity of the measure (the switcher can “remember” the address of the skin computer connected to the second port and the child as a regulator only to transfer data to the addressee’s computer and to the recipient’s computer, so it’s not necessary no transfers by ourselves zvіlnyaєtsya merezhna throughputna zdatnіst);
2) the commutators give the skin node a measure of bandwidth to the protocol.
2.2.1 Selecting the switching method
Switches of local networks can implement different ways of transmitting frames.
Switching with intermediate savings (store-and-forward) - the switcher copies the entire frame that is received in the buffer and performs a re-verification for the presence of pardons. How to clear a pardon frame (the checksum is not saved, or the frame is less than 64 bytes or more than 1518 bytes), it is not cleared. If the frame does not receive pardons, then the switcher knows the address of the receiver at the switching table and displays the output interface. Let's wait, as if the next filter was not assigned, we will send the whole frame to the recipient. The best way to transfer orders from zatrimki - the more the frame is expanded, the more time is needed for yoga, and the re-verification for pardons.
Switching without buffering (cut-through) - a local switcher copying the internal buffer only to the receiving address (the first 6 bytes after the prefix) and starting to transmit the frame without checking the second one. This regime changes the hustle, but the re-verification for pardons does not win. There are two forms of switching without buffering:
Switching from fast-forward switching - this form of switching causes a low delay for the speed of the frame starting to be transmitted negligently, as soon as the destination address is read. Transferring a frame can forgive pardons. In this way, the adapter has to be used, to which the whole frame is assigned, it’s different, which means the need to retransmit the frame.
Fragment-free switching - the switch filters colliding frames before transmission. For a correctly working order, a collision can be carried out for the first 64 bytes. Therefore, all frames with a length greater than 64 bytes are considered correct. This switching method is checked until the frame is taken out of the frame will not be rechecked for collisions, and only after the first transmission. This method of switching changes the number of packages that are transmitted with pardons.
For students in a small school, a store-and-forward switch is more important.
2.2.2 Switch class selection
In order to choose a commutator that is optimally suitable for the consumption of measures, it is necessary to know its value. This parameter is set on the basis of what the OSI (data transfer) model is based on.
Attachments of the first level, which victoriously transfer data physically, have practically emerged from the market. The butt of a physical equal habi, in which information is transmitted by a strong stream.
Riven 2. Practically all non-wired commutators lie until new. Vikoristovuetsya so called channel merezheva model. Attaches add information to other packages (frames, frames), revise them and send them to a specific device-controller. The basis of the distribution of information in switches of another level is MAC-addresses. From them, the switch stores the addressing table, remembering which port the MAC address is given. IP addresses don't stink.
Riven 3 . This switch already works with IP addresses, and it can also convert logical addresses to physical ones. On the third merezhe Practically all routers work on the transmission line and most of the commutators are "put through".
Riven 4 . Merezheva OSI model, as it is called here transport . Please note that not all routers are available for additional models. Rozpodіl traffic vіdbuvaєtsya on іntelektualnomu pіvnі - pristry vmіє pratsyuvati z dodatki і on pіdstavі tanovіvі vіdbіv z dannym їх їх їх їх to the required address. In addition, the transport level protocols, such as TCP, guarantee the reliability of packet delivery, saving the sequence of their transmissions and optimizing traffic.
The shards of the fence do not have special abilities and for the annex the setting of folding lines is not transferred, then the whole channel switch of another equal is not transferred.
2.2.3 Selecting a commutator to complete a task
From the number of working areas, the commutator is responsible for the mother of at least 16 ports. Conducted analysis of the establishment of the market (Table 3). TP-Link TL-SG 3216 commutator is a leader in terms of price/performance ratio.
Table 3 Peer table of switches 2 rows
|
name |
D-Link DES-3200-18/B1A |
TP Link TL-SG3216 |
HP 1910-16G Switch (JE005A) |
|
Virobnik |
|||
|
Number of ports |
|||
|
Width of ports of the switch |
10/100/1000 Mbps |
10/100/1000 Mbps |
10/100/1000 Mbps |
|
Table expansion MAC address |
|||
|
Operating temperature |
vіd 0°C to +40°С |
vіd 0°C to +40°С |
vіd 0°C to +45°С |
|
Rosemary (WxHxD) |
228.5x195x44mm |
440x220x44mm |
442x160x432mm |
|
Switching method |
store-and-forward |
store-and-forward |
store-and-forward |
2.3 File server
File server The purpose of the server, optimizations for the selection of file input operations and assignments for saving files of any type. As a rule, there may be a great deal of disk space. This presence at the border allows you to increase the security of the exchange of data, to increase the reliability of the collection of information.
To move the stability to a file server, it is so necessary to bring a trouble-free life.
When choosing a server, pay attention to the following characteristics, like:
- processor productivity;
- Volume of operational memory;
- hardness of hard disk;
- vіdmovostіykіst.
2.4 Working station
Floor computer (working station), connections to the merezhі, є universal university. Applied computer hardware in the least is assigned to software security and installed additional features.
The main computers are upgraded as gaming computers at a reduced price for changing the capacity of the computer. The equipment is balanced in such a way that it would be comfortable to work with the necessary additions.
So, as a file server will not be too much pressure, as a computer with the same parameters as in work stations will win. The characteristics of the selected computers are given by the addendum Art.
2.5 Notebook choice
For the tasks of the technical project, at the local border there are not only stationary, but also portable computers (laptops).
Since the laptop will be victorious all the time with the method of learning, high productivity will not be required. For a lower price and a quality wonderfully pidide laptop Lenovo B590, the characteristics of which were induced by G.
2.6 Inspection and selection of the tie cable
For local networks, there are three principles of the payment scheme: for the help of a twisted bet, coaxial or fiber-optic cable. For the transfer of information, satellites, lasers, micro-wild vibrance can also be used, they can go beyond the scope of a given graduation project, the shards need to be organized simply in the implementation of that operation, as well as a cheap local measure zhu.
2.6.1 Coaxial cable
coaxial cable(coaxial) electric cable . Sound to serve the transmission of high-frequency signals.It is made up of two cylindrical conductors, one is inserted into the other (Figure 6). The most common is the central copper conductor, covered with plastic insulating material, on top of which there is another conductor - copper mesh or aluminum foil. Zavdyaki zbіgu tsentrіv both wires, spend on vipromіuvannya practically every day; at once, the garniy zahist is protected from the ovnіshnіh electromagnіtnyh shifts. Therefore, such a cable ensures the transmission of data to large networks and vikoristovuvavsya with computer networks (until it is connected with a twisted pair cable). Vikoristovuєtsya in the cable television networks and rich in other areas.

Figure 6 Coax cable
A coaxial cable cannot be twisted due to local barriers due to the following reasons:
- Marezhevі segments based on torsion pairs are more stable in robotic segments on a coaxial cable, shards in the first type of leather attachments can be insulated with a hub in the central core, and in the other type, the extensions are connected for the help of one segment cable, i, at times a large number of collisions the hub can isolate the entire segment;
- The coaxial cable is smaller for installation, the pair is twisted lower;
2.6.2 Fiber optic cable
Fiber optic cable | cable on about c new fiber. Optical fiber is a glass or a plastic thread, which is victorious for the transfer of light in oneself for the help of a complete internal fermentation (Figure 12). The optical fibers are connected to the fiber optic link, which allows the transmission of digital information on a large scale and with a higher speed of data transmission, lower in electronic communication links. In a number of vipadkіv, stench is also vikoristovuyutsya for the creation of sensors.
At the link, there are multi-mode and single-mode optical fibers (Figure 7). Bagatomodov fiber optics sound victorious at small distances (up to 500 m), and single-mode fiber at long distances. Through suvory tolerance between single-mode optical fiber, transmitting, receiving, subscribing those other single-mode components, they will sound more expensive, lower the cost of rich-mode components.

Malyunok 7
Do not be surprised at those that fiber optics can be vikoristane not only as a zasib for telecommunications, but if you need a computer network, you can’t victorize when designing it, you can’t do it yourself, shards alone from the factory |minimization of wires on the line, and the fiber optic is much more expensive, the lower cable is twisted pair. It’s not enough for him to win yoga, for that in the meantime he doesn’t need a great deal of data transmission.
2.6.3 Vita pair
A pair of wires in this hour is the widest transmission medium and a pair of wires. The cable, folded from dekіlkoh twisted pairs, as a rule, covered with a hard plastic sheath, which protects it from the inflow of a splendid medium and mechanical strengths. The picture of the twists of the bet is shown in figure 8.

Malyunok 8 Vita pair cable
In normal minds, a pair is twisted to support data transmission speed of 10 to 100 Mbit / s. However, a number of factors can significantly reduce the speed of transmission of data, zocrema, waste of data, cross-over and influx of electromagnetic interference.
To change the flow of electric and magnetic fields, a screen is installed (the cable from twisted pairs is covered with foil or braid). Ale, after the screening of the twists of the bet, the significant world will increase the fading of the signal. When the signal is extinguished, it may be possible to avoid the first weakening of the transmission from one point of the line to another. Ekranuvannya change opir, inductance and capacity in such a way that the line becomes graceful before spending money. Similar spenders can make a twisted bet with an unbearable and undesirable medium of transmission. І screened, and unscreened twisted pair of victors for transmission of data over hundreds of meters.
Vіdpovіdno to specifіkatsіy аsotsіаtsії elektronnoї ї telekomunikatsіynoї ї promyslovosti vіdpovіdno ії її її її її їїїїїїїї її їїї їїїїїїїїї її її їїїїїїіїїїїїї її її For a higher category cable, the twisted pair cable (UTP) is not shielded.
- The cable of the first category is used for transmission of voice data. Since the beginning of the 80s, the CAT 1 cable has been victorious mainly as a telephone line. The cable of the first category of non-certified transmission, whether of any type and in the majority of cases, is considered as a medium for the transmission of digital data, but the project is not yet implemented.
- The cable of another category is capable of transmitting information with a speed of three more than 4 Mbit/s. Which type of wiring determines the old mesh topology, the protocol with the transfer of the token. The cable is clocked at a frequency of 1 MHz. This category of cable is impossible to vikoristovuvatisya, oskolki vіdpovіdaє help the project to the speed of transmission;
- The cable of the third category is more important to win in local networks due to the old architecture of Ethernet 10base-T and certifications for data transmission with speed up to 16 Mb/s. The cable is clocked at 16 MHz.
- The cable of the fourth category is victorious as the middle of the chain with ring architecture or 10base-T/100base-T architecture. CAT cable 4 data transfer certifications with speed up to 16Mbps and consists of four twisted pairs. Clocked at a frequency of 20 MHz.
- Category 5 cable is the widest transmission medium for Ethernet. The cable supports data transmission speed up to 100Mb/s and works in 100base-T and 10base-T architectures. The cable is clocked at 100 MHz.
At the moment, the cable is twisted in a pair of category 5e - the best choice for vikoristannya in local dimensions, both large and small. Vіn pіdtrimuє I will improve the speed of transferring data and I can win in merezhs with different architectures. The very same wine and vikoristovuvatimetsya for the implementation of the project. The cable can get ahead of other wiring diagrams, so it can get ahead:
- Ease of installation;
- Flexibility of the cable;
- Visibly low variance for good performance in throughput;
- Ease of replacing or recharging in times of poshkodzhennya.
This project has a twisted pair of UTP category 5e cable from TopLan. Information about the cable is provided by the addendum D.
2.7 Selection of information sockets
For this project, one information socket with one socket module for the skin working area with a laptop is provided.
The type of socket modules depends on the adjustment of the capacity, the configuration of the working space and the method of installation. The socket module is installed at a height of 50 cm from the bottom.
Standard sockets with one RJ-45 socket of category 5e were selected for cable installation on work stations. For this project, Logicpower sockets (LP-212) will be chosen, data about how they were put in addition to D.
2.8 Installation choice
2.8.1 Switch cabinet
Seeing that the equipment does not need any other space, everything is installed in the wall switching cabinet, which will be won by the CMO SHRN 9.650 with a curse on the door. The closet is given, so that it’s good to go up to the dimensions of the possession, it’s not very high, and it’s also possible to have a point lock.
All the necessary characteristics of the switching cabinet were induced by the addendum E.
2.8.2 Cable channel
For the laying of that cables, standard plastic boxes of two types will be used. For laying along the line, there is a decorative channel DKC СSP-N 75x17 G. For bringing cables along the wall to the switching cabinet | cable channel DKC 01050
Data about the boxes was given by the addendum E.
Zagalna varnosti merezhnogo obladnannya and vitratnyh materials
All data about the number and quantity of possession, necessary for the creation of a local counting measure, is given in Table 3.
Table 3 Variation and quantity of possession
|
name |
Quantity, pcs. |
Price, rub. |
Vartist |
|
router |
|||
|
Switch |
|||
|
System block |
|||
|
Keyboard |
|||
|
Coil cable "Vita pair" |
|||
|
Information socket |
|||
|
Mounting cabinet |
|||
|
Cable channel pidlogy |
|||
|
Wall cable channel |
|||
|
267154 without boxes |
|||
3 PROJECT PART
3.1 Development of the mesh model
When designing a building in Persh, a model of a model is developed with reference to the actual plans and engineering structures. Tsya deya allow:
- Appointment, de bude installed kommunіkatsіyne obladnannya.
- Select from urakhuvannyam іsnuyuchih kommunіkatsiy hiring a man for laying komunіkatsiynyh cables.
- Looking at the scale of the plan, it allows to open up approximately the length of the skin cable segment.
For the development of the model, the method of imitation modelling, the shards of the larger world, help to promote adequacy and foldability.
As a program for the development of the simulation model of the mesh, the program was selected Microsoft Vision.
The scheme of the office of informatics is shown by the addendum Zh.
3.2 Pobudova local measures with reference to the plan-scheme of life
The virtual office wall is isolated from other computers at the school. All cables are laid in cable channels and laid along the pipeline. The server room for possession is not transferred, the shards of the fence are small, and the communication closet is installed directly in the office. The shafu has a switch and a router installed. At the office, six laptops and five computers were stocked, one of which was a file server. The maximum distance of the LOM segments to the switching facility does not exceed 70 meters, which complies with the EIA/TIA-568-B data transfer rate of 100 Mbit/s.
The fence will be behind the Zirka topology with 1 switchboard and 1 router. The logical and physical scheme inspire the images of the appendix I.
3.3 Rozrahunok dozhini cable
On working places with laptops for convenience, an external computer socket is installed. We will install 6 sockets for a number of laptops. An “untwisted twisted pair category 5e” cable (UTP) is laid to the skin working area from the shafi.
For connecting laptops to sockets, one meter switching cords are used. The number of these cords is so expensive six for a skin outlet.
Laying the cable is easy in the cable channels. The switching cabinet is installed without intermediary in the office at a height of 2 meters from the logs.
The length of the length of the cable is more than the sum of the length of the cable from the skin working area to the switching cabinet. So, since it cannot be calculated empirically through a small measure, the theoretical method will be won, based on the plan of the cabinet. Table 10. The calculation method is no longer accurate, for the skin cable a margin of 0.5 m is taken.
Table 10 Rozrahunok dozhini cable
|
Computer number |
Cable length, m |
|
N1+2. 5 = 7 |
|
|
N2+2=9 |
|
|
N4 + 2.5 = 9.5 |
|
|
N5+2=11.5 |
|
|
N6+1=12.5 |
|
|
N8+2.5=11.5 |
|
|
N9+2=13.5 |
|
|
N11+1=14.5 |
|
|
Together: |
With the summation of all cable segments without fixing the switching cords, the length was no more than 97 meters. Since the cable is a twisted pair, it is sold in coils of 305 meters, you can calculate the number of coils required by formula 1:
N=L/l(1)
de N number of bays, pcs.;
l | length of the entire cable, necessary for laying the fence, m.;
l | cable length in one bay, m
By substituting the relevant values, the formula used to be the same viraz:
N = 97/305 = 1 pc.
From the new one, it is necessary to organize 1 bet roll.
3.4 Logical organization of the measure
How to access technology fast ethernet , What secures the data exchange rate of 100 Mb/s.
As a forerunner of the technology 100BASE-TX, IEEE 802.3u is a development of the 10BASE-T standard for vikoristannya in the "star" topology. Back twisted couple category 5:CAT5e - speed of data transfers up to 100 Mbit/s. Category 5e cable is the widest and most widely used cable for computer networks.
3.5 Forming the address structure of the mesh
For the molding of the address space IP - Class C addresses (addresses in the range 192.0.0.0 to 223.255.255.0). The pidmerezhi mask may look like 255.255.255.0. The first 3 bytes form the number of the link, the remaining byte forms the number of the node.
Є a number of IP-addresses, which are reserved for victories only in local networks. Packets with such addresses are not forwarded by routers to the Internet. For class C, such IP addresses include addresses from 192.168.0.0 to 192.168.255.0.
The following IP addresses are assigned to the local area of the school:
- File server 192.168.1.1;
- access point Wi - Fi 192.168.1.5;
- the main computers at the office of informatics may IP - Addresses from 192.168.1.10 to 192.168.1.20;
3.6 Working place
3.6.1 Headlights
Working spaces are called open spaces near budіvlі, de coristuvachi vzaєmodіyut іz telecomunikatsіyy outbuildings. The special features of the design of the working space are the most convenient options for both robotic coristuvach and the normal functioning of the telecommunication installation.
The components of the workspace may be between the termination point of the horizontal cable subsystem on the telecommunication socket and the active owners of the workspace. Electronic attachments, such as telephones, terminals of data processing systems, computers and others, are included before the active possession of the working space. The efficiency of the cable system of the working area significantly affects the work of the sub-system. The peculiarity of the cable system of the working area is inconsistency and the ability to easily make changes to it.
Before the elements of the working space lie:
- a telecommunication socket or is insured for a rich corystuvachiv telecommunication socket;
- hardware cables (cords);
- adapters, converters, rozgaluzhuvachі;
- telecommunication equipment (telephone devices, computers, modems, terminals, etc.).
Active telecommunication adapters (converters, galuzhuvachs) are not a part of the telecommunication cable system.
3.6.2 Telecommunication socket
Telecommunication sockets serve to connect the active telecommunication installation of coristuvach in working areas and physical terminations of the horizontal cable subsystem.
A telecommunication socket is an element of a horizontal cable subsystem, and a work space.
Telecommunication sockets, which are installed at work stations, are to blame GOST R 53246-2008.
The cables of the horizontal subsystem are laid on the working area near the outer space with a reserve for possible connections at the future. Such cables are terminated in mounting boxes of sockets, covered with blank covers.
Cables of the horizontal subsystem, laid to the working areas and terminated on telecommunication sockets, are not included in the SCS warehouse.
The wiring diagrams for the telecommunications sockets comply with the T568B standard.
The thumbnail 12 shows the identification of contacts in the socket of the telecommunication socket for the T568B wiring circuit. Conductor colors are designed according to the color coding scheme for a 4-pair cable of a horizontal subsystem.

Figure 12 - Assignment of contacts in the distribution scheme T568B
It is allowed to switch one hour to one SCS of two distribution schemes T568B and T568A, but after the possible pardons during installation, operation and connection of the active device to the cable system is not recommended, and there will be no delay.
3.6.3 Workplace hardware cords
Apparatus cords based on a twisted pair of conductors, which are twisted for connecting an active device to a telecommunication socket on a working area in a model channel of a horizontal cable subsystem, comply with GOST R 53246-2008 codes.
The cabling system of the working area can be changed depending on the specific program. For which vicorist there is a cord with the same connectors on both ends.
Specialized attachments, designated for support of robots and specific add-ons, do not vikoristuvatimutsya as a part of the horizontal cable subsystem and, if necessary, be installed behind the boundaries of a telecommunication socket.
3.6.4 Place for installation of telecommunication sockets
A telecommunications socket is a vuzol that consists of three elements: a mounting box, a mounting frame and a connector.
A connector, or a module (socket module), is a telecommunications socket, installed in the module case or on a different board and electrically connected to the connector socket of the IDC type, designated for terminating (physically terminating) cables in a horizontal subsystem.
The telecommunication socket is made up of two connectors, the shards are secured for the connection of a portable device.
The mounting frame, which often serves as a decorative front panel for one hour, serves to mount the module in an installation box.
Installing a box for a telecommunication socket and a transition between the cable of the horizontal subsystem and the hardware cable of the working station. Creeper will be out of the middle on the perimeter route (cable box).
The telecommunication socket will be superficially fixed on the field for additional help and methods, prescribed by the instructions of the virobnik, and to ensure the protection of the termination, maintaining the necessary radii and saving the recommended reserve of the cable of the horizontal subsystem.
3.6.5 Width for mounting sockets
At least one installation for the installation of telecommunication sockets was installed on the skin of the work station.
When planning the location of the expansion of telecommunication sockets of the vicorist, the average value of the area of the working area is 5 meters, with the adjustment of the installation of the maximum possible flexibility and the hour of change in the configuration of the working area.
3.6.6 Rules for choosing the location of socket outlets
The space for the distribution of telecommunication sockets is coordinated from the plan for the distribution of furniture near the office on the vіdstanі not more than the standard length of the equipment cord of the active equipment of the working area in the area of the office of the installation.
On the working area, a laying was fenced (behind closed routes) to the cable of the horizontal subsystem to the installation telecommunication box/socket.
Sockets of the office power supply system are installed near the installation box of the telecommunication socket at the same height within 1 meter.
3.6.7 Trace and space of furniture
The coefficient of filling of the furniture line is to be covered at a height of 100 meters under the total area of the transverse section of the cables on the area of the transverse section of the line at the "high" її mіstsі. At the stage of designing the system of furniture lines, the vicorists have a coefficient of filling of more than 40%.
On the value of the filling factor, such factors are added, like a spiral-like expanse of distribution of cables near the channel, the space for obtaining routes, the allowable radius of the cable and the space that is occupied by sockets and connectors. The most important method of determining the real capacity of the furniture line is trial installation.
Furniture channels, which are used for laying telecommunication cable systems, should provide a cross-sectional area of at least 10 centimeters. Tsya area is insured for the use of standard 4-pair cables with a coverage coefficient of 33%.
The minimum width of the cable is to be determined on the basis of the cable up to a radius of 25 mm for the cables with the maximum allowable filling factor. In our project, the cable is to be installed by the method of laying, and not by pulling, it will not need more cuts, which are rounded, and turned.
3.7 Software for organization of measures
How the server operating system will be tested by Windows Server 2008 R 2, which is the most reliable and secure operating system in the Windows server OS family, which is necessary for the server.
Windows Server 2008 R2 - the company's server operating system Microsoft ”, which is a complete version Windows Server 2008 . Happened at sales July 22, 2009 . Like Windows 7, Windows Server 2008 R2, Windows NT 6.1 core. New features include improved virtualization, new version Active Directory, Internet Information Services 7.5 and support up to 256 processors. The first OS Windows is available only in 64-bit version.
Windows Server 2008 R2 є allow for analysis and diagnostics of the operating system, so the server operating system itself is given to the low number of new technical capabilities in the security room, management and administration, development for increasing the reliability and flexibility of the server robots.
Price: RUB 36,000.00

Figure 13 Windows Server 2008 R2
Like the OS on the working stations is installed earlier Windows 7
Operating system Windows 7:
- ensure a high level of scale and supremacy;
- secure more high security levels, including the ability to encrypt files and folders to protect corporate information;
- secure support for mobile attachments to ensure the ability to work autonomously or connect to a computer in remote mode;
- ensure the implementation of highly productive rich processing systems;
- secure the ability to work with Microsoft Windows Server R2;
- ensuring effective interaction with other coristuvaches in the whole world, the possibilities of bagatomo's support.
In addition, on all computers it is necessary to install the anti-virus program ESET NOD32 Business Edition.
This anti-virus program was disabled for the following reasons:
1) Proactive defender and more precisely identified threats. Antivirus ESET NOD32 is developed on the basis of advanced ThreatSense® technology. The kernel of the program ensures proactive detection of all types of threats and detection of infected files (including those in the archives) triggering a wide flood of intelligent technologies, using heuristic methods and traditional signature-based detection.
2) Host Intrusion Prevention System (HIPS).Improved the system of protection against the sprobing of the sound inflow, which can negatively interfere with the security of the computer. For monitoring processes, files and keys in the HIPS registry are being exploited using advanced behavioral analysis technologies with the capabilities of a mesh filter, which allows you to effectively detect, block and intimidate similar samples of intrusion.
3) High speed of work. The ESET NOD32 antivirus does not work on the productivity of the scanning computer, and the update process is practically unimportant for a hard worker, not navigating the system.
4) Brilliance. Antivirus ESET NOD32 is divided according to the principle of minimal effort on the system and takes no more than 44 MB of memory.
5) The simplicity of the quotation.
Varity: 28 586 UAH.
As a result of the analysis of the software security, the following table was taken:
3.8 Defender of the fence
For the normal, uninterrupted functioning of the fence, it is necessary to ensure security. Specialized software programs to protect information from unauthorized access may, in general, improve the capability of that characteristic, lower in the case of security systems. Crimean encryption software, there are a lot of other available external tools for protection. Most of the time, these are the systems that allow you to surround information flows.
- Firewalls - firewall (literally firewall - fire wall). Special industrial servers are created between local and global barriers, which sort and filter all the traffic of the barrier/transport lane that passes through them. This allows you to drastically reduce the threat of unauthorized access to corporate networks, but not to the insecurity of the call. More protection against the different method - tse way of masquerade (masquerading), if all the traffic that comes out of the local fence is sent in the name of the firewall-server, robbing the local fence is practically invisible.
- Proxy-servers (proxy - trust, trusted person). All the traffic of the border/transport lines between the local and global lines is blocked by a layer, just daily routing, and the traffic from the local line to the global one is routed through special servers-intermediaries. It is obvious that with this method, the transition from the global to the local level becomes impossible. It is also obvious that this method does not give enough protection against attacks on higher levels, for example, on other programs (JavaScript viruses).
- Antivirus program (antivirus) A program for detecting and detecting programs infected with a computer virus, as well as for infecting a file infected with a virus. A lot of current antiviruses allow you to detect and see also Trojans and other malware programs. First of all, programs that were created like firewalls, also know the functions that can be compared with antiviruses (for example, Outpost Firewall), which over time can lead to an even more obvious broadening of the sense of the term for self-zahistu vzagali.
Our company will download the anti-virus program ESET NOD32 Business Edition.
3.9 Visibility
Vіdmovostіykіst tse is one of the main factors, which is necessary to protect when prompting local measures.
At the time of the exit of the school, it is possible to damage the work of the practitioners, the loss of tribute. Table 11 shows a variety of faults and their consequences.
Table 11
|
Incorrectness |
Possible reason |
Discounts for merezhi |
Problem Solving |
Come in later |
|
Exit and fret of the main switch |
Departure from the fret of all the measures. |
Switch replacement. |
||
|
Vihіd that fret of the commutator in one vіddіlіv. |
mechanical failure; incorrect operation. |
Departure from the fret of the segment of the merezhі. |
Switch replacement. |
Correct operation; availability of a spare switch. |
|
Get out of the way of the server. |
mechanical failure; improper operation; install server components. |
ymovirnіst spend all the data; know the possibility of centralized data collection. |
Repair of the server (it is possible to replace the components or, in the extreme case, to replace the server). |
Pіdbіr server, scho to cope with the needs of the company; pіdbіr komplektuyuchih іz pіdvishchenoy nadіynіstyu. |
|
Departure from the fret of computers koristuvachiv. |
mechanical failure, virus inactivity, improper operation; software conflicts. |
It is possible to exchange data with a faulty computer. |
Repair of a client computer |
Proper operation: technically look around; presence of antivirus; obmezhennya rights koristuvachіv. |
|
Get out of the way of the modem, access point, merging printer. |
mechanical failure; incorrect operation. |
Exchange of the functions of the faulty possession (duty WiFi , access to the Internet ...) |
Replacement of possession. |
Proper operation: technically look around; presence of antivirus; availability of a spare installation. |
|
Get out of the way of the tethered cable |
Mechanically poor. |
Vihіd z fret merezhі chi її parts. |
Replacement of the wire cable. |
The cable is guilty of perebuvati at the boxes; Availability of a spare cable. |
In order to increase the possibility to a minimum, the measures should be taken to a large number of benefits:
- duplication of living blocks;
- possibility of "hot" replacement of components;
- duplication of the core module;
- duplication of switching matrix/bus;
- vikoristannya kіlkoh duplicating columns;
- alternative technology Multi-Link Trunk (MLT) and Split-MLT;
- it is possible to implement protocols in balancing the burden and duplication on equal routing;
- separation of terminations of canals;
- separation of channels;
- Vikoristannya high-pressure possessing.
Merezha, which is organized in the project, may come forward in terms of capacity:
- the topology of the border is "star", which allows you to easily find out and fix the faults;
- at the time of exit from the fret of one of the working stations, reshta koristuvachiv continue to function in the normal mode;
- zastosuvanya anti-virus software security allows you to secure the least possible damage in case of virus attacks.
List of vicorists dzherel
- GOST R 53246-2008. Information technologies. Cable structuring systems. Design of the main nodes of the system. Zagalni vimogi
And also other robots, they can inspire you |
|||
| 3565. | Sequence of solving tasks on the development of programs | 78KB | |
| The sequence of completion tasks for the development of programs | |||
| 3566. | The main appointment. Apply algorithms | 122KB | |
| The main appointment. Apply the algorithms of Analysis (in Greek, "decomposition, division") - the operation of imaginary or real division of the whole (speech, power, process or incorporation between objects) in the warehouse of the parts that are consummated ... | |||
| 3567. | Hardware and software warehouses of electronic computing machines. | 46KB | |
| Hardware and software warehouses of electronic computing machines. A personal computer can be represented for the help of two indispensable warehouse parts: a hardware part, a software part. Hardware storage parts can be divided... | |||
| 3568. | Basic Movie C# | 302KB | |
| Founding a C# movie Created by a C# movie Irrespective of those that the course of Algorithmization and programming, as one of its components, transfers the implementation of expanded algorithms on basic programming languages. I want to dabble in some special features of m... | |||
| 3569. | Tipi Data C# | 88.5KB | |
| C# Data Types The author of the .NET Common Type System (CTS) assignments, which is located at the center of the Microsoft .NET Framework. CTS applies not only to all types, but also to the rules, such as the Common Language Runtime (CLR) follo... | |||
| 3570. | C# Movie Programming Syntax | 164.5KB | |
| C# Movie Programming Syntax We can look at the basis of what kind of movie programming it is - this building is attracted by that responsibility for the assistance of operators. We would like to know that these are operators in C# and that they are precedence, and then zag... | |||
| 3571. | Introduction to C#. Creation of console attachments | 1.45MB | |
| Introduction to C#. The creation of console add-ons Mova C# (which includes C-Sharp) is a code for MOV programming from the Microsoft company. This includes the version of Visual Studio - Visual Studio.NET. C# Visual Studio .NET includes Visual Basic.NET and Visual C++. One... | |||
| 3572. | Algorithms for working with whole numbers | 54KB | |
| The type of goal number is the main one for any algorithmic movie. It is related to this, that instead of the memory box or the processor registry, you can see the whole number. Addresses of elements of memory are also whole numbers, machine commands are written in addition to them, etc. | |||
| 3573. | Algorithms for robots with real numbers | 89.5KB | |
| The actual numbers are presented in the computer in the so-called exponential, or floating, form. | |||
It's easy to send your harn to the robot to the basics. Victory the form below
Students, graduate students, young adults, like victorious base of knowledge in their trained robots, will be your best friend.
Placed on http://www.allbest.ru/
INSTUP
1.4 Local mesh topologies
1.5 Merezhev technologies
2.1 Characteristics of the object
2.4 Administration of the measure
2.5 Protection of information from the measure
3.2 Payroll
3.3 Razrahunok varnosti installation work
3.4 Reconciliation
3.5 Designated admission price
4. PROTECTION OF PRACTICE
4.1 Ensuring the security of the safety equipment and the protection of the work of the EOM operator
4.2 Safety equipment for service hours of electrical control
WISNOVOK
BIBLIOGRAPHY
INSTUP
In today's organizations, as a primary mortgage, business offices, shops or administrative offices for the security of more security, handy sleeper work, it is accepted to vikoristovuvat local counting measures (LAN). All that has been said above indicates the actuality of those thesis papers "Disaggregation of local counting measures".
Object: Designing and disaggregating the local enumeration measure.
Subject: Designing and arranging the school yard.
The meta of the thesis work: to learn and systematize the theoretical material necessary for inducing LOM; organize and improve the work of LOM at school No. 15, metro Krasnotur'insk.
To complete the set, it is necessary to complete the following tasks:
- learn the theoretical foundations of LOM.
- Vivchiti hardware and software.
- Vivchiti mehanіzmi pobudovi, roboti SCRAP.
- Follow up the administration of LOM.
1. THEORETICAL FOUNDATIONS FOR LOCAL METERING
1.1 Ownership, necessary support of various computer systems
Merezhevy adapter.
If you want to quickly connect your computer to a local network, this computer can have a special attachment installed - a network controller.
Merezhevy adapter vykonuє impersonal zavdan, the most important of these є coding / decoding іnformatsiї і otrimannya access to the information medium with the variance of the unique identifier (MAC address).
Merezhevі cards are bought at the expansion boards, they are inserted at the external slot.
Also, the cards can be introduced into the mother's pay, which are being used everywhere these days.
The main indicators of the lace pattern can be the standard that is supported, and the type of connection to the computer.
The standard that is supported. Іsnuyt merezhi іz different merezhimi standards. Tse means that the card is responsible for the mother type of the connector (or connectors) and to take care of the change of the exchange of information. The most important type of connector.
The type of tie card connector depends on the choice of tie topology and the cable that transmits data. Use of connector types: RJ-45 (for twisted bets), BNC (for coaxial cable) and for optical fiber.
Malyunok 1 - Merezhevy adapter
Malyunok 2 - RJ-45 (twisted pair)
Malyunok 3 - BNC (coaxial cable)
Malyunok 4 - Fiber optic cable
The stench is essentially different for the design, so it’s impossible to win the connector for no reason. I want to use combined mesh adapters, for example, RJ-45- and BNC-connectors. Ale, the shards of the merging on the coaxial cable are more and more similar, the same ones are used with the same adapters.
Type of connection to the computer. On personal computers, the card must be installed in a PCI slot or a USB port. Moreover, be it a modern motherboard, it can already integrate a mesh controller.
Merezhevy adapters for a wireless mesh seem to be practically not compatible with other options, due to the obviousness of the socket for the antenna - internal or external. Merezhevі pay, yakі connect via USB-port, traplyayutsya to dosit often, especially costless options.
Malyunok 5 - Merezhevy adapter for WIFI
concentrator.
If more than two computers are to be removed, it is necessary to use special attachments for the future connection, one of which is a hub. As a rule, you should know your concentrator on the basis of a twisted bet.
A concentrator (also called a hub, repeater, repeater) - an attached device that can have two or more roses (ports), a kind, a crim switch for connecting to a new computer, for other functions, for example, a stronger signal y.
The concentrator serves to expand the measure, and the main purpose is the transfer of information, which is necessary for the input, to all connections to the new extension in the measure.
All connections to the concentrator will be attached to absolutely the same information, which at once is not long enough - the presence of decal concentrators in the measure will be observed on the air by the respective notifications, the concentrator will not send real addresses, for which it is necessary over send information, and embarrassment to everyone. At any time, the concentrator has its own task - the back of the computer, which is in the same workgroup. In addition, vin analyze pardons, zocrema kolіzії, scho blame. If one of the linked cards is brought up to fix some problems, then the port on the concentrator, to which it is connected, can be switched on at the same time.
The concentrator implements the physical level of the ISO / OSI model, on which standard protocols are used, it can be beaten to the extent of any standard.
There are two main types of concentrators:
- Concentrators with a fixed number of ports in the simplest. Such a concentrator looks like a solid case, with a singable number of ports and works on the reverse side. As a rule, one of the ports will serve as a happy lanka between another hub or a switch.
- Modular concentrators are stacked from blocks, which are installed at a special chassis and connected with a cable. It is also possible to install concentrators that are not connected with each other by a hot bus, for example, if there are different local lines, the links between them are not of principle.
Malyunok 6 - Hub
Mist.
Mist (also called a candle, peremikach) є to add a simple extension, the main recognition of this - subdivided two segments in a measure with a method of increasing the її zagalї dozhini (depending on the number of connected repetitions) merge topology.
As a rule, there may be two more ports, to which the segments of the mesh are connected. Analyzing the address of the owner of the package, you can filter the information assigned to a different segment. Packages designated for the “home” segment are simply ignored, which also changes traffic
There are three types of bridges to inspire merezhі vikoristovuyu:
- local - only with segments of the same type, so that they can have the same speed of data transmission;
- converting - assignments for the same, scho and local location, moreover, working with different segments, for example, Token Ring and 100Base;
- in the distance - the rear segments, roztashovanі on a significant vіdstanі, with which you can win, whether it's possible to make a connection, for example, a modem.
Malyunok 7 - Merezheviy town
Switch.
The commutator has the same capacity as the hub and the bridge, as well as other functions.
The concentrator, otrimavshi in the form of a packet of data, not knowing about those to whom it is addressed, sends it to all connected to the new merezhny outbuildings. It doesn't matter what kind of traffic is being created, because in the region there is not one, but a sprat of concentrators.
The commutator is a larger intellectual attachment, which does not only filter packets that need to be found, but, by looking at the table, the address of all merezhnyh attachments, accurately indicating which of them the packet is assigned to. Tse allows you to transmit information to several outbuildings with maximum speed. The switches work on the channel level, which allows them to be switched not only in different types of lines, but also to combine different lines into one.
Therefore, for organizing a great network of commutators, the best ones. Moreover, in the rest of the hour, the number of commutators fell down, so the number of concentrators is not true.
Malyunok 8 - Commutator
Router.
The head office of the router (the same name is the router) - added a great number of borders to the subdivision, it has a great number of basic functions and, obviously, it can have great possibilities and "intellect". The new one will have a hub, a place and a switch. In addition, the possibility of routing packets is added. At the connection with the cim, the router works on the highest level - the merging one.
The table of possible routes for the current packets is automatically and permanently updated, which gives the router the ability to choose the shortest and the last route of delivery.
One of the main tasks of the router is the link of various tethered segments in the local tether. Behind the help of the router, you can also organize virtual networks, such as access to quiet other resources, the Internet.
Organization of filtering of broad notifications at the router of the vikonan to a higher level, lower at the commutator. All protocols, which are selected by merezh, are accepted and processed by the router processor without any transitions. To learn how to use an unknown protocol, the router quickly learns how to use it.
The router can be twisted in both wired and wireless meshes. Most routing functions rely on wireless access points.
Malyunok 9 - Router
Modem.
The modem is also є mezhezhnymi okladnannyam, and yogo dosi often vykoristovuyut for arranging access to the Internet.
There are two types of modems: external and internal. The external modem can be connected to the computer, via LPT, COM or USB port.
The internal modem is an expansion board, so you can insert it into the PCI slot. Modems can work with a telephone line, with a seen line and with radios.
In the fall, in the type of I will build that middle of the transfer of data, the security of the transfer of data is raised. The speed of a standard digital-analog modem, which works with an analog telephone line, is 33.6-56 Kb/s. In the rest of the hour, more and more often digital modems are trapping, which defeat the advantages of DSL technology, which can work on the speed, which exceeds 100 Mbit / s. Another unforeseen problem of such modems is the availability of a free telephone line.
For communication with another modem, their own protocols and algorithms are used. Great respect is attached to the quality of the exchange of information; The modem can be used in both wired and wireless meshes.
Malyunok 10 - Modem
Access point.
An access point is an attachment that works for a wireless network in infrastructure mode. It plays the role of a concentrator and allows computers to exchange the necessary information, win for this routing table, ensure security, wake up hardware DNS and DHCP servers and a lot more.
From the access point to lay not only the quality and stability of the link, but also the standard of the dart-free line. There is a large number of different models of access points with different powers and hardware technologies. However, today the best possible options are to use attachments that work with the IEEE 802.11g standard, some of them in total with the IEEE 802.11a and IEEE 802.11b standards and allow you to work on a speed of up to 108 Mbps. More promising and fast is the IEEE 802.11n standard, which will help you to start entering the market.
Malyunok 11 - Hotspot
1.2 Principles for inducing local merging
The server or the client is the same function as the computer. Whether a computer at a merezhі can defeat the functions of a server or a client, or it can defeat offending functions at once. All lie down in the form of software security.
Server functions (serve - to serve) - to perform operations for the requests of clients. You can also: save and transfer files, monitor programs to see results, maintain printers as well. If the computer does not function as a server, it may also be called a vision server. Often, such a computer has either a monitor or a keyboard, and all its control is controlled from other computers through a network.
If a computer does not have the same server functions as a merezhі, such a computer is called a work station (workstation).
If the computers of a network simultaneously work both server and client functions, then such a network is called a peer-to-peer network.
Different operating systems (OS) are different for server and client functions. Uses a number of operating systems, specially designed for server maintenance.
A lot of organizations are victorious over a sprinkling of servers, between which rozpodіlyaєtsya vantazhennia: leather server wins over the same task. For example, one can accept all requests to another, and the other can secure access to files. The skin server can be customized to be as efficient as possible for a specific type of service.
Computers that play the role of servers fall into two main categories:
- Zagalnogo confession, zdatnі nadavat impersonal rіznih services;
- Spetsіalіzovanі, razrahovanі for a specific type of service.
1.3 Ways to organize a computer network
Depending on the tasks set, the ways of setting up local measures of business (corporate measures) can be different. Most often, the combination of different technological solutions allows you to reach the optimal solution. Skin from zastosovuvannyh methods may have its own advantages and shortcomings. For example, merging local mergers into a single corporate merger of an organization can be done:
- To the victories of the conducting measures for the transfer of data.
- To the victories of the handless transmission lines.
So, as the school has a lot of laptops, it is possible to choose a peer-to-peer network of a different type (some of the clients are connected via a cable, and others are connected to a network via Wifi).
Figure 12 - Butt of a mixed type
1.4 Local mesh topologies
Under the topology of the counting network, it is possible to understand the way to connect four components (computers, servers, printers, etc.). There are three main topologies:
- Topology of the star type (Fig. 4);
- topology of the ring type (Fig. 5);
- Topology of the type of galvanized tire (Fig. 6);
Figure 13 - Topology of the star type
Figure 14 - Ring topology
Figure 15 - Topology of the busbar
With different topologies of the zirka type, information between the clients of the network is transmitted through a single central hub. As a central node, a server or a special attachment - a hub (Hub) can act.
The advantages of this topology are similar to those of the offensive:
- High swidkodiya merezhі, oskolki zagalna proizvodstvennіst merezhі lie down less in the productivity of the central node.
- Vidsutnіst zіtknennya danih, scho are transmitted, shards of data between the working station and the server are transmitted via a separate channel, without interfering with other computers.
- However, this topology has a lot of advantages:
- Low nadіynіst, oskіlki nadіynіst usієї merezі vznachaєєєєєєєєєєєєєєєєєєєєєєєєєєєє dіііnіstі central vuz. As the central computer is out of tune, the robot is all the same.
- High card for connection of computers, wires to the skin of a new subscriber, it is necessary to send an okrem line.
The star is active - there is a computer at the center of the city, which has the role of the server.
Passive star - not a computer, but a concentrator is located at the center of the border with a topology, but a hub, which is a switch that performs the same function, like a repeater. Vіn vіdnovlyuіє signals, yakі nakhody, i peredaєєєєєєєєєєєєє іхі інії sv'yazku. Usі koristuvachі merezhі rivnopravnі.
With a ring topology, all computers are connected to a closed line in the ring. The signals are transmitted along the ring in one direction and pass through the skin computer (Fig. 16).
Malyunok 16 - Transfer algorithm in ring topology
The transfer of information in such a measure is like this. The token (special signal) sequentially, from one computer to the next, is transmitted until that hour, until it is rejected by the one that needs to transmit data. After removing the marker, the computer creates a "package" title, which gives the owner's address and data, and then sends the package back to back. Data to pass through the skin computer until it shows up at the one whose address is matched with the owner's address.
After that computer overpowers the dzherelu іnformatsії confirming the fact of taking data. After confirming the confirmation, the computer creates a new marker and turns it into a measure.
The advantages of topology to the ring type are similar to those of the offensive:
- Overpowering the reminder is even more effective, because you can nadsilat kіlka povіdomlen one by one on kіltsyu. Tobto. the computer, having given the first notice, may send such a notice after it, without checking, if the addressee is the first to reach it.
- The length of the line can be significant. Tobto. computers can be connected one to one on significant signals without switching to special signals.
Before the shortcomings of this topology, one can see:
- Low nadіynіst merezhі, shards vіdmova be-yakoy computer tyagne in his vіdmov vsієї system.
- To connect a new client, it is necessary to unmute the robot.
- With a large number of clients, the number of robots is increased in size, so that all information passes through a leather computer, and the possibility of an exchange.
- The overall productivity of the measure depends on the productivity of the most advanced computer.
For the topology of the open bus, all clients are connected to the open transmission channel. If so, the stench can be without intermediary contact with any computer, which is in the measure.
The transfer of information in this measure is like this. Data like electrical signals are transmitted to all computers of the merezhi. However, the information is received only by the computer, the addresses of which are given by the address of the owner. Moreover, at a skin moment, more than one computer can transmit data.
Topology advantages of a hot bus:
- All information is stored in the database and is available to the skin computer.
- Working stations can be connected independently one to one. Tobto. when a new subscriber is connected, there is no need to transfer information in the measure.
- Pobudova merezha on the basis of the topology of the roof bus is cheaper, so you have to pay for the laying of additional lines when a new client is connected.
- Merezha maє high nadіynist, t. praceszdatnіst merezhі lie in pіd praceszdatnіstі okremih kompyuterіv.
Up to a short topology of the type of a hot tire lie:
- Low speed of transmission, because all information circulates in one channel (bus).
- Shvidkodiya merezhі to deposit in the number of connected computers. The more computers are connected to the merezhі, the better it is to transfer information from the computer to another.
- For meshes based on this topology, low security is typical, but some information on the skin computer can be accessed from another computer.
The widest type of merging with topology is a wire bus є merging to the Ethernet standard with a fast transmission rate of 10 - 100 Mbit/s.
For real, every hour of the creation of LOM organizations can single-hourly win over a number of topologies. For example, computers in one area can be connected behind the star circuit, and in another area behind the circuit there is a high-speed bus and a line for communication is laid between them.
1.5 Merezhev technologies
Merezheva technology - the benefits of a set of standard protocols and software and hardware features (for example, mesh adapters, drivers, cables and rosettes) that implement them, sufficient for stimulating the calculation of the measure. The epithet “sufficient” reinforces that situation, which one has collected with a minimum set of cats, for the help of which one can induce a practical measure. Possibly, it is possible to improve the area, for example, for the perspective of seeing it in the city, which will allow us to take advantage of the Ethernet protocol to stop the IP protocol, as well as special communications attachments - routers. The merezha will be shortened, more for everything, nadіynіshoy and svidkodіyuchіshoy, but for rahunok nadbudov over the problems of Ethernet technology, as if laying down the basis of the merezha.
The term "merezheva technology" is most often victorious in the narrow sense described above, but sometimes it stagnates and expands the clouding, as if it were a set of features and rules for prompting merezhі, for example, "technology of cross-cutting routing", "technology renny, hijacked by the channel", "technology IP "-Merezh".
The protocols, on the basis of which there will be a merger of singing technology (in a narrow sense), were specially developed for a joint work, therefore, in the case of a merger, it is not necessary to add additional data to organize their cooperation. Other merezhnі tekhnologii ї nazvayvayut basic tekhnologii, loom on vazі those that on their basis will be the basis of what ever. As an example of the basic merging technologies, one can use Ethernet such as local merging technologies such as Token Ring and FDDI, or X.25 and frame relay territorial merging technologies. In order to remove the practical measure in any way, it is enough to have software and hardware devices that include up to one basic technology - mesh adapters with drivers, concentrators, switches, cable systems, etc. but up to the standard for this technology .
1.6 Cables to be stuck in local lines
In an hour, the development of local networks appeared to be finished with a rich variety of cables, and all the stench - the result of standards that were becoming more and more complicated. The deyakі from them have already gone in the past, and the deyakіlki only begin to zastosovuvatysya, and zavdjaki їm it was possible to make such a high speed of transmission of data necessary for us.
Coaxial cable.
The coaxial cable is one of the first conductors, which were victorious for the construction of meshes. The coaxial cable is made up of a central conductor laid in insulation, copper or aluminum braiding and outer insulating sheathing of the coaxial cable.
Malyunok 17 - Coaxial cable
For work with a coaxial cable, there is a sprat of roses of a different type:
- BNC connector. Installs on cable ends and serves for connection to T-connector and barrel connector.
Malyunok 18 - BNC connector
- BNC T-connector. It is a kind of tee, which is victorious for connecting a computer to the main highway. This design is to avenge three roses, one of them is connected to the rose on the border card, and the other two are victorious for the closing of two main lines.
Malyunok 19 - BNC T-connector
- BNC barrel connector. With this help, you can connect the rozirvani kіntsі trunks or finish part of the cable to increase the radius of the fence and connect additional computers and other cistern extensions.
Malyunok 20 - BNC barrel connector
- BNC terminator. It is a kind of stub, as it blocks the signal from expanding further. Without a new functioning, a mesh based on a coaxial cable is impossible. We need two terminators, one of which is responsible for buti obov'yazkovo grounding.
Malyunok 21 - BNC terminator
Connect the coaxial cable to the electromagnetic guidance. Vіd yogo vikoristannya at local computer networks has long been recognized.
The coaxial cable, having become more important, stops transmitting the signal to satellite dishes and other antennas. In another life, a coaxial cable is removed as a main conductor of high-voltage wires, in which the transmission of digital and analog signals, for example, a wire of cable television is possible.
Twisted couple.
Wita pair at this time is the widest cable for local networks. The cable is stacked in pairs intertwined with copper insulated conductors. A typical cable is carried by 8 conductors (4 pairs), if you want to produce a cable from 4 conductors (2 pairs). The colors of the internal insulation of the conductors are strictly standard. Vіdstan mіzh pristroyami, z'єdnani twisted pair, is not guilty of overvischuvat 100 meters.
Zalezhno vіd nayavnostі zahistu - electrically grounded copper braiding or aluminum foil on twisted pairs, using a variety of twisted bets:
- Unshielded twisted pair (UTP, unshielded twisted pair). Crimia conductors from the wet plastic shielding of the daily supplementary braiding and grounding wires are not broken.
Baby 22 - Unshielded twisted pair
- Foiled twisted pair (F/UTP, foil twisted pair). Use the wires of the conductors of this cable to make a sleeping screen made of foil.
Baby23 - Foiled twisted pair
- Shielded twisted pair (STP, shielded twisted pair). In this type of cable, the skin pair has its own wet braid, which is screened, as well as the presence of a glowing screen for all screens
Baby 24 - Shielded twisted pair
- Screened Foiled twisted pair (S/FTP) The skin pair of this cable is in a wet braided foil, and all pairs are placed near the middle screen
Baby 25 - Screened Foiled twisted pair
- Screened Foiled Unshielded twisted pair (SF/UTP). It is characterized by a hinged screen with a copper braid and a foil braid.
Baby 26 - Screened Foiled Unshielded twisted pair
The main cable category is a twisted pair type, which are marked as CAT1 to CAT7. Chim category vishcha, tim yakisny cable and tim better indications of vin maє. In local computer networks to the Ethernet standard, a pair of the fifth category (CAT5) with a range of frequencies of 100 MHz is twisted. When laying new lines, it is necessary to completely break the CAT5e cable with a range of frequencies of 125 MHz, which transmits high-frequency signals more quickly.
For work with a cable, a pair of vicorous sockets is twisted, type 8P8C (8 Position 8 Contact), RJ-45 titles - RG-45 connector
Fiber optic cable.
Fiber optic cable is the most common medium for transmission of data. Vіn vengeance kіlka gnuchkih sklyanyh svіtlovіv, zahchenih hard plastic insulation. The speed of transmission of data over fiber optics is at the top of the head, and the cable is absolutely not weak to the point of overshoot. Vіdstan mіzh systems, z'єdnanim optical fiber, can reach 100 km.
Malyunok 27 - Fiber optic cable
There are two main types of fiber optic cable - single-mode and multi-mode. The main features between different types of connection with different modes of passage of light changes at the cable. For fiber optic cable fitting, there are no-colored roses and connectors of various designs and suppleness, among them the most popular are SC, ST, FC, LC, MU, F-3000, E-2000, FJ and other connectors for fiber optics. The blockage of fiber optics at local fringes is surrounded by two factors. If you want the optical cable itself to be cost-effectively inexpensive, the prices for adapters and other equipment for fiber optic cables are high. Installation and repair of fiber optic tethers will require high qualifications, and for the completion of the cable, the road will be expensive. Therefore, the fiber optic cable is used mainly for the consolidation of segments of large networks, high-speed Internet access (for providers and large companies) and data transmission to large networks.
At the wire mesh, the cable is twisted for the construction of a viable physical medium for data transmission. With this, it is often used that the common standard of the wire is transferred to the cable of your choice.
In this rank, there are many types of cables, the main ones are cable based on torsion pairs, coaxial and fiber optic cables.
I know, however, that the standard of the meshing means the cable has the same characteristics, in view of which there is no middle ground and protection of the mesh.
At the connection with the usim, we will override with the main parameters of the cable and the steps:
- Frequency smuga transmission;
- Diameter of conductors;
- Diameter of conductor with insulation;
- number of conductors (couples);
- Show the screen next to the explorer(s);
- Cable diameter;
- temperature range, in which case the indications are changed from the norm;
- The minimum radius of the wind, which is allowed when laying the cable;
- maximum allowable guidance at the cable;
- soft support cable;
- maximum attenuation of the signal in the cable.
All these parameters are included in the understanding of the cable category. For example, the cable on the basis of torsion pari has five different categories. In this case, the greater the category, the better the cable displays, the greater the capacity of the new building.
1.7 Merge and routing
Routing - the process of assigning packets to a route. Routes can be set directly by the administrator (static routes), or they can be calculated for additional routing algorithms, based on information about the topology of that network, taken for additional routing protocols (dynamic routes).
The routing process in computer networks is controlled by special software and hardware devices - routers. In addition to routing, routers also perform channel switching / update / packets / median, so the computer network switch switches routing (assigned to which port to send the packet to the MAC address table), and is named after the main functions - switching. The word routing means the transfer of information from the dzherel to the receiver through the shared network. If you want to, it would be necessary once to repair the lining of the fence.
Routing is made up of two main warehouses. Determination of the optimal route between the dzherelom and the receipt of information and the transmission of information along the way. The rest of the function is called switching.
The appointment of the route is based on various indications, calculated on the basis of one change, for example, on the route or combinations of changes. Algorithms of routing virakhovyut indicators of the route of the optimal path to the point of destination.
To facilitate the process of assigning a route, routing algorithms initialize and update routing tables in which routing information is stored. Routing information changes depending on the routing algorithm that wins.
Routing algorithms fill the routing tables with the necessary information. The combinations tell the router that the destination point can be reached by the shortest path when forwarding the packet to the first router on the path to the final destination point. When a packet is received, it is necessary to arrive, the router remaps the address to the destination point and tries to associate the address with the next retransmission.
Malyunok 28 - Routing Algorithm
2. ORGANIZATION OF LOCAL METER MOU SOSH
2.1 Characteristics of the object
School No. 15 is located at 19 Chernishevskogo Street. The school has 30 primary classrooms, including classrooms for physics, chemistry, biology, history, life safety, foreign language, technology (with a fully equipped kitchen pits), office of informatics and ICT, library ( with a fund of over 36 thousand books), a sports hall and a stadium, an assembly hall, a medical and treatment room, a distance room for 150 months (eating is studied on a contractual basis with a combine of school eating).
The advent of a new computer and multimedia possession, the improvement of the efficiency of the computer and multimedia play a great role in the development of the informational and primary medium of illumination. other tasks (offices of informatics, physics, biology, history, life safety, 2 foreign language classes, 4 classrooms for primary classes, mathematics, 3 Russian language classrooms, a multimedia room, 2 demonstration rooms equipped with computer technology for conducting lessons by subject teachers).
2.2 Functional scheme of the local counting measure
Figure 29 - The principle of operation of the measure
The possession that zastosovuetsya, that їх kіlkіst:
- personal computers (35);
- laptops (14);
- Linksys router model - WRT54GL (1);
- Router D-Link model - DIR300 (2);
- Router TP-Link model - TL-WR841N (10);
- D-Link switch model - DES-1008d (4);
- Bay cable UTP 4 par 300 meters (2);
- RJ-45 connectors.
A more detailed description of the work of the skin element can be found at paragraph 2.4.
2.3 Planning the structure of the measure
When choosing the type of merezha, it was necessary to vrakhovuvat a lot of officials, the most famous and virishal became:
ѕ Finansi vіdіlenі on the laying of the fence and the fence;
ѕ imovirna zavantazhenіst merezhі;
¾ the need for a sacred collection of tributes;
ѕ number of computers working at the border;
* compact rotting of coristuvachіv;
ѕ globally expanding the scope is not necessary in the future;
ѕ the nutrition of the zahist of the danichs is not critical.
Vykhodyachi z rehabilitated more factors was adopted a decision about the need for a peer-to-peer network for the selection of droto-free modules.
Tya merezha includes the presence of the server. Oskіlki kozhen computer є one hour і client, і server, there is no need in the tight central server or in other components, binding for more foldable meshes, then, it is not necessary to include yoga in the merzhu and stained finance that hour.
To combine computers into a peer-to-peer network, it was enough to create the structure of the network (lay cables or buy wireless access points, install switches and other devices). The computer is connected to the measure and nalashtovuєmo vykoristannya resources of other systems. At his discretion, the administrator of the skin computer will signify that the resources of the local system are given in the right place and with some rights.
Under the hour of installing a peer-to-peer network of additional software security was not needed.
The stability of a peer-to-peer network is characterized by a number of standard solutions:
- Computers roztashovanі on work tables koristuvachіv;
- Koristuvachs themselves act as administrators and take care of the protection of information.
2.4 Administration of the measure
The administrator of the measure is a specialist, who is responsible for the normal functioning of that resource recovery in the automated system and (or) the calculation of the measure.
Administration of information systems includes the following:
- Installation and installation of a fence;
- pіdtrimka її podshoї pratsezdatnostі;
- installation of basic software;
- monitoring of measures;
At the link with the cim, the administrator of the merezhi is obliged to follow the following orders:
- system planning;
- installation and configuration of hardware extensions;
- software installation;
- installation of a fence;
- vstanovlennya that control zakhistu;
The installation and adjustment must be started from the very beginning of the network, in this case, from the adjustment of the head router, and also the DHCP server. For this role, the Linksys router model - WRT54GL was selected.
Malyunok 30 - Linksys WRT54GL
DHCP (Dynamic Host Configuration Protocol) is a shared protocol that allows computers to automatically assign an IP address and other parameters needed to operate within a shared network. This choice allows the manual adjustment of the computers in the merezhі and the change in the number of pardons. As a rule, the DHCP server provides clients with the least basic information:
- IP addresses
- Pdmerezhi mask
- Main gateway
However, we are hoping for additional information, such as the addresses of DNS and WINS servers. The system administrator sets the parameters on the DHCP server, which are enforced by the client.
To set up, you need to connect the Internet cable to the "INTERNET" port (the WAN port is also the WAN port), and the cable that goes to the computer to the "LAN" port. After that, you need to go to any Internet browser on the computer connected to the router and write “192.168.0.1” or “192.168.1.1” in the address row, after which you will be asked for authorization, login and password, you can look at the router (sound at the bottom of the sticker), or in the documentation of the router, which is included in the kit (important on all routers, the login is "admin", the password is "admin"). Then, depending on your provider, the type of WAN connection is set.
Main types of WAN connection:
- dynamic IP;
- static IP;
- PPPOE;
- PPTP/Russia PPTP;
- L2TP.
Our type of provider is “Center for Information Technologies”, which has a static connection, which means that it is necessary to fill in the required fields. After that, as IP addresses, mask, gateway and DNS servers are registered, it is necessary to configure DHCP. For this, in a single distribution, enable the DHCP function and prescribe a range of IP addresses, as they will be distributed to clients at the enterprise. For example: 192.168.1.50 - 192.168.1.150
After these parameters, our head router (DHCP server) is ready to go.
Figure 31 - Linksys Router Configuration Result
After setting up the head router, for clarity, it is necessary to set up other routers (stinks work like an access point, and they themselves will transmit information from the head router to the computer using wifi or cable), they will be immediately after all the necessary connections uvan connected to commutators and computer 'yutheriv .
We are in front of the D-Link routers model DIR-300. In order to enter the setup menu of these routers, you need to carry out the same steps as needed to enter the setup menu of the head router, and you yourself need to go to any Internet browser on the computer connected to the router, and in write the address in the row “192.168.0.1” or “192.168.1.1”, after which you will be asked for authorization, login and password, you can look at the router (look at the bottom of the sticker), or in the documentation of the router, which is included in the kit (mainly on all routers login - "admin", password - "admin" ”). After that, the type of Internet connection is established. Since we already have a connection to the Internet on the head router, we choose the type of connection - static IP. This means that the router accepts all addresses and transmits remotely from the main router.
Figure 32 - Setting up an Internet connection on the D-Link DIR300
The DHCP function must be enabled, but the main router acts as a DHCP server. At the IP point of the router, for the sake of remote control, we set the IP address for the cabinet number, in which case the router itself will be. The number of D-Link DIR300 routers is 2, they are located in rooms 4 and 13, so their IP addresses look like this - "192.168.1.4" and "192.168.1.13". If in the future we will need to reset it, we can go to the reset menu of the computer by entering their IP address into the address bar of the browser and go through the next authorization.
Figure 33 - An example of setting the IP address on the router, which is changed in the office number 4
So, as a mesh is given to a mixed type (it is wired without a dart), then wifi is automatically installed on the routers, and the password protection itself is installed and it changes its name to the number of the office in which the router itself is known.
At the branch "Setting up a dartless tether" it is necessary to prescribe a wifi tether of the same name to the office number, then select the "wpa/wpa2psk" security mode and enter the password for the wifi tether itself.
Malyunok 34 - Butt of installing wifi on the router, which is in office number 4
After all the patching, the router is ready to work in our measure.
The next step is to fix the TP-LINK TL-WR841N routers. The entrance to the router setup is similar to that of the routers described earlier, and in any browser itself, in the address row, write "192.168.0.1" or "192.168.1.1", after which you need to pass authorization. Nalashtuvannya follows the same plan, like the above-described D-Link DIR300.
Enable the DHCP function, but we can also use the DHCP server.
Figure 35 - DHCP setup on TP-LINK TL-WR841N router
Set the type of WAN connection - Dynamic IP.
Malyunok 36 - Implementation of the WAN type on the TP-LINK TL-WR841N router
In the installed LAN, it is possible to set the IP address to the same cabinet number, in which the router is located.
Malyunok 37 - Nalashtuvannya IP addresses of the router TP-LINK TL-WR841N
At the built-in wire-free meshes, it is necessary to enter the wifi mesh itself with the same room number, in which the router is located. Then we select the type of passwordless network, and the WPA-PSK / WPA2-PSK itself and enter the password for the password.
Figure 38 - Name of the wireless network on the TP-LINK TL-WR841N router
Malyunok 39 - Creating a WIFI password on a TP-LINK TL-WR841N router
After all the patches on the TP-LINK TL-WR841N routers, the stench is ready to work in our measure. computer tethered local cable
If all the elements of our tassels are sewn, you can connect the tassels. Connecting the outbuildings to the bazhano is started from the very first element of the fence through the lace. The first extension is the head router, as described earlier, the Internet cable is connected to the INTERNET port or the WAN port, and the cable that was given (In our connection to the hub) is connected to the LAN port.
Figure 40 - Connections to the head router
The next element of our measure is the concentrator. Connecting a cable that goes to the head router and connecting cables that go to the next elements in our network (concentrators of distribution on the tops), which port will be connected to. Note that the hub is not programmable. Similar to the offensive concentrators.
Malyunok 41 - Connections to a merezhі concentrator
Since the routers are configured as access points, and the same as described earlier, DHCP is disabled, and the connection type is dynamic IP, then the cable that goes in the concentrators and the head router is connected just like the cable that goes to the next element (or the next router, or computer) at the LAN port.
After all, our mesh is ready to work, it is necessary to connect computers (cable to access point) and laptops (wireless mesh).
Figure 42 - Working group of school computers
2.5 Protection of information from the measure
Curriculum school following the laws 139-FZ and 436-FZ "About the protection of children from information, who is in charge of children's health and development" goiter for the protection of students from unsafe Internet resources (pornography, drugs, extremism m). It is necessary like the children themselves, the psyche of such children is only being formed, so the administration of the school - for non-compliance with the law, sanctions can be imposed on the side of the prosecutor's office. Therefore, it is necessary to organize defenses at schools from shkіdlivih and fences for children to see sites. The choice was content filtering via SkyDNS.
Content filtering system SkyDNS wins out not only in schools. Incorporating high technologies, experts and experts’ knowledge, a database was selected from a large number of millions of sites divided into 50 categories, which allow you to individually adjust the filtering parameters.
For especially extreme cases (small children, prosecutor's review), a special filter operation mode has been transferred, with which access to any resources, crim trusted sites from the white list is blocked.
In addition, a special poisk system poisk.skydns.ru is supported, as an additional filtering of all posh requests, ensuring the safety of children. The lists of the Ministry of Justice are regularly updated to improve the black lists in the current state.
Figure 43 - Secure SKYDNS Poosh
SkyDNS is the only "dirty" solution, as it works like a web service, blocking access to unsafe sites even before real access to their resources.
Naychastishe not be able to put any PZ on the computer of the students. All that is needed is to adjust the parameters of the Internet gateway, and specify the category for blocking on the site.
In addition, SkyDNS can be a little collaborative. The number of subscriptions to the service of filtering becomes less than 300 rubles per computer.
In order to start hacking the SkyDNS DNS filtering service, you need to:
- choose how to improve the filtering needs - however, the difference is the same as the skin for the computer (groups of computers). In our mind, the filtering is the same;
- z'yasuvat yaku zovn_shnyu IP address by pressing the provider - static or dynamic. As stated earlier, the school provider provides a static IP address;
- choose the order in which you need to fix the computer settings (for DHCP, or manually registered). At a measure of inclusions the DHCP server, otzhe, prescribing addresses manually is not brought up (div. point 2.4).
- link a static IP address to a profile in a SkyDNS account;
- Tweak to allow outgoing DNS names SkyDNS DNS server 193.58.251.251.
A special solution is being promoted, the SkyDNS school filter, which has taken over the city of Gold Parental Control laboratory AntiMalware.ru. Having demonstrated the results of the Internet filter, you can compete with the leader's indicators - Kaspersky Lab's researches.
Figure 44 - An example of blocking a sloppy site with a filter.
3. ECONOMIC ROOM OF DESIGN
3.1 Razrahunok varnosti basic and other materials
For the purpose of varnosti installation of local meshes, it is necessary to develop labor costs.
Labor - the cost of the working day of the production of a single manufactured product in natural expression and all stages of the work.
Labor costs for skin surgical transition are presented in Table 1
Table 1 - Labor on operational transitions
Seen from Table 1, it is clear that the hard work for all operational transitions is to become 990 hvilin.
For this graduation project, the warehouse of material vitrates can be assigned to the improvement of certain features while laying local lines. The staff of practitioners will unite under the same name vitrat.
How to get information on the sum of all the costs of the Sbcom, rub., it is necessary to win the formula:
,
de M - stained on materials;
OZP - the main salary for fahivtsy, yakі take a part in the rozrobtsі programs;
DZP - additional salary payment to specialists, to take part in the development of programs;
ЄSP - single social contribution;
SO - wiping, tied with a robotic possession (amortization);
OKhR - zagalnogopodarski vytrati;
KZ - pozavirobnichi (commercial) vitrati.
Usі obladnannya, scho vikoristovuєtsya pіd hіkonannya montage robіt, is presented in table 2.
Table 2 - Vіdom_st vitrat on the main and vitratnі materials, komplektuyuchі virobi and small-size tools.
namematerials |
Alone in the world |
Quantity, pcs. |
sum, rub. |
||
|
UTP 5E cable |
|||||
|
Roulette Stayer |
|||||
|
Ros'em RG-45 |
|||||
Obtisk tool |
|||||
|
Cable stripping tool HT-322 |
|||||
|
Spinner chrestov ORK-2/08 GOST 5264-10006 |
|||||
namematerials |
Alone in the world |
The price for a single vimir, rub. |
Quantity, pcs. |
sum, rub. |
|
|
Marker GOST 9198-93 |
|||||
|
Drill bit 60x120 |
|||||
|
Linksys WRT54GL Router |
|||||
router |
|||||
routerTP Link TL-WR841N |
|||||
SwitchD-link DES-1008D |
|||||
Expenses for material expenses for virib M, krb., are insured according to the following formula:
,
de pi - type of i material at vіdpovіdnіst to kіlkostі;
qi – variability of pet unit i material.
Obsyazh material vitrat for the formula (3.2) go:
3.2 Payroll
The cost of the basic salary is calculated on the basis of a divided technological process of work, as it is necessary to include the following information:
? about the aftermath and the death of all victorious victories;
? about the qualifications of practitioners who have been trained to the end of the quiet chi and other species work at all stages of production (transitions, operations);
? about the laboriousness of vikonannya of all kinds of work;
? about the technical equipment of the working areas and the working hours of the work at all stages.
The salary of a practitioner for a year of work is calculated according to the following formula:
,
de - salary of a worker for a month;
TP - working day fund for a month, accepted equal to 176 years.
The tariff rate of a practitioner of the fifth category warehouse is 5150 (rubles/month)
The tariff rate of the practitioner for the year of work for the formula (2.3) is:
(Rub.)
Basic salary, OZP, rub., Depends on the formula:
,
De Zprobsch is a direct salary.
KZOZ - podvischuu dovidkovy coefficient, its value is determined on the basis of interest rates, which podvishuyut, shkodo direct charges for the payment of wages of the worker. It is recommended to move interest rates in the interval from 20% to 40%, for these robots the rate of 30% is chosen, or Kozp = 0.3.
To determine the direct salary for referrals, the total amount of the direct salary is calculated according to the formula:
, (3.5)
de Zpr.i - Direct salary on the i-th transition.
Zpr is secured by the formula (3.6):
de Om-salary of a practitioner for a year;
T is the hour of the operation;
D-working hour fund for the month, 176 years
t - working hour for mining
Zpr razrakhovuetsya for the formula (3.6).
For the preparer:
(Rub.)
For harvesting:
(Rub.)
For mounting:
(Rub.)
For setup:
(Rub.)
For styling:
(Rub.)
For control:
(Rub.)
For customization:
(Rub.)
The salary for transfers is paid according to the formula (3.5):
(Rub.)
The main salary for the formula (3.4) is:
(Rub.)
The salary of the basic salary, depending on the qualifications and salary of the practitioner, is shown in Table 3.
Table 3 - Basic salary expenses
|
operation name |
Operational hour, hv. |
Qualification of a practitioner |
Practitioner salary, rub./year. |
Actual expenses for transactions, rub. |
|
|
Pіdgotovcha |
|||||
|
Zagotivelna |
|||||
|
Mounting |
|||||
|
Nastanovna |
|||||
|
Ukladna |
|||||
|
control |
|||||
|
Nalagojuwalna |
|||||
|
Correction factor = 0.30 |
|||||
|
At once: OZP with the adjustment of the correction factor |
Supplemental wages are actually extra allowances to stimulate the practitioner to improve his work hourly, revisit the plan, and work properly. Here are the next few premium wines and toshcho. Dodatkova salary, DZP, rub., To be paid according to the formula:
...Similar documents
Selection of technologies of local counting measure. Exit to the Internet. Scheme of cable laying and rozrahunok dozhina kabelіv. Logical topology and scaling of the mesh. Specification of the vicarious possession from the appointed vartost and rozrahunok vitrat on the possession.
course work, donations 11/27/2014
Pіdbіr vіdpovіdnogo merezhnogo obladnannya, sсho vіdpіdaє vymom bred tekhnologiї i opremії organіzatsії. Rozrahunok zagalnoї varnostі kabelіv, vitrat on designing and installation of local calculus measure and terms of recoupment.
graduation work, donation 07/20/2015
Investigation of parameters in the design local calculation measure. Zagalna dozhina cable. Rozpodіl IP-address for the designed measure. The specificity of the possession of that stained glass materials. Selection of the operating system and application software.
course work, donations 11/01/2014
The structure of the local computer network organization. Rozrahunok vartosti pobudov local merezhі. Local arrangement of organization, designed by technology. Pobudov local networks of Ethernet organizations. 10Base-T local network scheme.
course work, donations 06/30/2007
Rozrobka topology merezhі, choice of operating system, type of fiber optic cable. Vyvchennya transfer of functions and services, which are hoped for by the coristuvachi in the local counting system. Rozrahunok of the necessary amount and vartost of the restored possession.
course work, donations 12/26/2011
Classification of local networks with topology. Merezha architecture Ethernet. Functional scheme of the local enumeration measure. Network configuration: number of servers, concentrators, printers. Typical models of different domain names.
thesis work, donations 05/08/2011
Ways to connect different computers to the next. The main ambush of the organization of local enumeration measures (LAN). Development and design of local enumeration measures at the enterprise. Description of the selected topology, technology, standard and possession.
thesis work, donation 06/19/2013
The concept of local enumeration, the architecture of computer networks. Local setup of computers. Installing the oblіkovogo record of the administrator. Enhancement of anti-virus security. The structure of the service delivery of the computer system.
thesis work, donations 01/15/2015
Improving the telecommunications possession of the local counting system. Selection of the architecture of the merezhi. Server configuration services. Rozrahunok cable, pіdbіr obladnannya and software security. Description of physical and logical schemes of counting measures.
course work, donations 12/22/2014
Understanding that recognition of peer-ranking and noble counting. Merged IEEE802.3/Ethernet. Selecting the topology of the local measure, the rank type and the protocol with the method of designing the calculation measure for the enterprise of the BAT "DKNP".
It's easy to send your harn to the robot to the basics. Victory the form below
Students, graduate students, young adults, like victorious base of knowledge in their trained robots, will be your best friend.
Accessbeforedisks It is possible to give the coristuvachas of local networks access to PC disks, which allows them to review, edit and save files on their disks. In order to give corystuvachs access to disk resources on your PC, you need to do the following:
Open the folder "My computer" and select the required disk, for example, disk E.
Right-click on the mouse icon on the disk icon and select the command "Global access and security" from the context menu.
At the "Power: Local disk (E)" dialog, set a jumper at the "Enable full access to this folder" position. The text row "Zagalniy resource" will have the writing "E"
Set the boundary number of coristuvachs
To choose the access rights to the disk drive, click on "Razdilna zdatnist"
At the dialog box "Dozvil for E", which was decided, install the coristuvachiv and the rights of the coristuvachiv.
Folder access
To set up a shared access to any folder on the hard drive of the computer, you need to:
Right-click the mouse on the icon of the required folder and select the "Common access and security" command from the context menu.
Gave vykonaty all diy, similar to diyami with recognized zagalny access to the disk.
Accessbeforeprinter
In order to give the shortlisted LOM access to the printer, which is the connection to your PC, you need to step on:
Right-click the mouse on the icon of the local printer connected to this computer, and select the "Global access" command from the context menu.
On the "Access" tab, set a jumper at the "High access to this printer" position
Click on the buttons "Stop" and "OK" at the window to save the changes made.
Connectionmerezhegoprinter
A printer connected to one of the computers of the local network can be copied to another document from any computer of the network. For which computer of the local network, to which the printer is connected, you can allow access to the printer to other corresponding networks, tobto. You can only set the "High access to the printer" mode.
It was necessary to give a personal touch on the PC, from which the document will be developed:
Select the command "Start" - "Setup" - "Control Panel" - "Printers and Faxes"
Select "File" - "Insert Printer"
At the "Printer Setup Wizard" window, click on the "Dal" button
At the next window, select the item "Merezhevy printer or printer, connections to another computer" and click "Next"
At the next window, set a jumper at the "Oglyad printeriv" position and click "Dal"
From the requested list of printers available for work in the local area, select the required printer and press the "Next" button
At the "Victory Printer for Promotion" window, set a jumper at the "So" position.
1.14 Basic technologies of local merging
Architecture or technology of local networks can be divided into two generations. Until the first generation, there is an architecture that ensures low and medium speed of transmission of information: Ethernet 10 Mb/s), Token Ring (16 Mb/s) and ARC net (2.5 Mb/s).
For transmission of data and technology, twist cables with a copper core. Prior to the next generation of technologies, state-of-the-art high-end architectures: FDDI (100 Mb/s), ATM (155 Mb/s) and upgraded versions of the first generation architectures (Ethernet): Fast Ethernet (100 Mb/s) and Gigabit Ethernet (1000 Mb/s) ) ). Improved options for the architecture of the first generation of insurance, such as installing cables with middle cores, and on fiber-optic transmission lines.
New technologies (FDDI and ATM) focusing on fiber-optic line transmissions and can achieve one-hour transmission of various types (video image, voice and data).
Merezheva technology - the minimum set of standard protocols and software and hardware devices that are implemented, sufficient for encouraging calculation. Merezhev technologies are called basic technologies. In Denmark, there are impersonal barriers that may differ in equal standardization, but there is a wide expansion of such technologies as Ethernet, Token-Ring, Arcnet, FDDI.
methodiaccessbeforemerezhі
ethernetє method of multiple access with wiretapping of carriers and permission of collisions (conflicts). Before the cob of transmission, the skin working station is designated, the main channel of chi occupations. If the channel is disabled, the station will start data transmission. p align="justify"> In reality, conflicts can only be reduced to the extent that 80-100 stations are used. access method Arcnet. This access method is wide-width due to the fact that Arcnet setup is cheaper than Ethernet setup and Token - Ring. Arcnet wins in local networks from the "star" topology. One of the computers creates a special marker (special notification), which is sequentially transmitted from one computer to the next. As a matter of fact, the station is guilty of sending a message, won't, after removing the marker, forming a packet, adding the addresses of the source and acknowledgment. If the packet is accepted by the station, the message "recognized" as a marker and transmitted to the station.
access method Tokenring. This method has been developed by IBM; Vіn razrahovany on kіltsevu topology merezhі. This method is used to guess Arcnet, shards are also vicorist markers that are transmitted from one station to another. On the Arcnet view, for the Token Ring access method, the ability to assign different priorities to different workstations has been transferred.
BasictechnologiesSCRAP
Ethernet technology is currently the most popular in the world. The classic Ethernet cable uses a standard coaxial cable of two types (thin and thin). However, more and more wide-spread version of Ethernet, which is the most popular as the medium of transmission of twisted bets, is so much easier to install and maintain. Set topologies to the "bus" type and to the "passive star" type. The standard defines some of the main types of transmission media.
10BASE5 (common coaxial cable);
10BASE2 (thin coaxial cable);
10BASE-T (twisted pair);
10BASE-F (fiber optic cable).
Fast Ethernet is a high-capacity type of Ethernet network that ensures secure transmission of 100 Mbit/s. Fast Ethernet measures are summed up with measures that are beyond the Ethernet standard. The basic topology of the Fast Ethernet network is a passive star.
The standard defines three types of transmission media for Fast Ethernet:
100BASE-T4 (quad twisted pair);
100BASE-TX (double twisted pair);
100BASE-FX (fiber optic cable).
Gigabit Ethernet is a high-capacity Ethernet network that ensures secure transmission of 1000 Mbps. The Gigabit Ethernet standard for this hour includes the following media types:
1000BASE-SX - a segment on a multimode fiber optic cable with a long wave of 850 nm light signal.
1000BASE-LX is a segment on a multimode and single-mode fiber optic cable with a long wave of 1300 nm light signal.
1000BASE-CX - segment on electric cable (shielded twisted pair).
1000BASE-T - a segment on an electric cable (quad, twisted pair).
It is easy to link together the Ethernet, Fast Ethernet and Gigabit Ethernet segments into a single mesh.
The Token-Ring is proponated by IBM. Token-Ring was intended to be shared among all types of computers that are produced by IBM (from personal to great). Merezha Token-Ring has a mirror-kilts topology.
Arcnet mesh is one of the oldest meshes. Like the topology of the Arcnet network to the "bus" and "passive star". Merezha Arcnet is not very popular. Among the main advantages of the Arcnet merezhі can be called high nadіynіst, low varіst adapters and gnuchkіst. The main shortfall is low transmission speed (2.5 Mbit/s).
FDDI (fiberdistributedDataInterface) - the specification for the mesh architecture of high-wire transmission over fiber optic lines has been standardized. Transmission speed – 100 Mbit/s.
Main technical characteristics of the FDDI measure:
The maximum number of subscribers in a merezhі is 1000.
The maximum length of the length of the merezha is 20 km.
The maximum distance between the subscribers of the merezhі is 2 km.
Transmission medium - fiber optic cable
The access method is marker.
Transmission speed - 100 Mbit/s.
Chapter 2
barriers at school
2.1 Goals and tasks of school informatization
For the rest of the year, there was a fundamental change in the role of personal computers and information technologies in the life of the society. The current period of the development of the society is called the stage of informatization. Informatization of the service of transferring universally and massively different methods and methods of collecting, analyzing, processing, transmitting, archival collection of great communications of information with the improvement of computer technology, and the development of various transmission mechanisms, including telecommunication measures.
Lyudina, who is happy, is effectively driven by technologies and information, but also a new style of thinking, in principle, it is still necessary to approach the assessment of problems, which one blames, to the organization of one’s own activity. As practice shows, without new information technologies it is already impossible to reveal a modern school. And today, as if earlier, it is important to move to a new level in approaches to the development of computer technology and information technology in all areas of school activity.
The current computer of education and the warehouse development of a learning individual - development, enlightenment, vihovannya, it is called upon to shape the social foundation of the growing generation, the internal impulse for development - a high level of sophistication, spirituality, culture. Henceforth, computer education becomes especially oriented, yoga meta - search for the meaning of meanings, the creation of a new system of values, self-development and self-realization in the computer environment.
The concept of modernizing lighting, the project "Informatization of the lighting system" and, nareshte, technical progress to put before the lighting the task of shaping ICT-competent specialty, building knowledge that in practical life for successful ї socialization in the current world.
processinformatizationschoolsallowSolutionoffensiveproblems:
development of pedagogical technologies for the development of informatization and communication on all educational platforms;
using the internet for illuminating purposes;
creation of the system of automatization of psychological and pedagogical testers, which diagnose methods of control and assessment of the level of knowledge of academics, their examination by the teacher, the establishment of the level of the intellectual potential of education;
automation of the activities of the administrative apparatus of the school;
training of personnel at the gallery of communicative and information technologies
Tsіlprogramsinformatizationschools№ 15 G. Zavolzhya - the creation of minds of modern computer technologies in the lighting process of managing the school, the promotion of information culture of the participants in the lighting process, the formation of the school in the single informational lighting space.
Technicalmanagerdirectorsschools№ 15 G. Zavolzhya:
· Behind the plan of the school draw a map of the border.
· Organize links between all computers of the school, with a further access to the Internet.
· To make it possible to collect information in one place.
· Organize remote access to the school database server
2.2 Choice of operating system
Operating system Microsoft Windows is taken from school computers. Linux will come to change. Її installation, which does not require the purchase of a license, obviously protects the budgetary costs of the initial mortgages.
Tired Windows presents new versions periodically, Linux is constantly updated. Vaughn is like a folk tale, because there is no specific author and geographic center. It develops spontaneously - one version falls into a dozen different variants. At schools, they want to recognize deeds of folding at the link with innovations, but they made it whole optimistically.
Sensing the transition to Linux is in the offensive:
1. changefallowviewforeignpostal leader.
The windows system is vibrating in the USA, where the country can without a doubt be able to invest in those that are embedded in the product, which are vibrating in this territory and regulate it all the time. And the shards of the Windows code are closed, no one can know what to kill. Linux doesn't have any problems. It is circulated by companies and people all over the world, the distribution is coordinated via the Internet. If you want to know more about who Linux is. You can see special Russian resources, such as: Linux Russian UnixForum Opennet Read articles from Wikipedia about Linux and the GNU project.
2. Savingskoshtiv. Since the Linux chips are most often expanded without cost or for the cost of carrying, and Windows is not compromised for the quality (on Linux, a significant part of the servers on the Internet and 90 of the hundred most powerful supercomputers), then the savings will be significant. More often than not, it’s possible to invest (assistant assistants, multimedia assistants), but also to make contributions no less than that our country pays generously for proprietary (with closed external code) products (and officials steal part of it).
3. negligencenewversionsWindows. The skin of the new version of Windows is becoming more and more powerful to resources. For Windows 7, a minimum processor with a clock frequency of 1 Gnz, 1 GB of RAM, 16 GB of hard disk space and a DVD drive is required. Not a skin school can, in its order, be similarly possessed. Until then, new versions of Windows are backed up with new features and can fix problems with older devices and programs. And, obviously, the speed of work on the old installation will be less. And the old versions of their Microsoft systems will not be accepted and supported.
They were based on the choice of the Unix operating system.
2.3 Selecting the structure of the local area of the school
A typical school scale of a local line looks like this. There is one exit point to the Internet, to which a different router (ADSL or Ethernet) is connected. The router is connected to a switch (switch), to which the PC of the coristuvach is already connected. On the router, it is practical to set up the activation of the DHCP server, which will automatically distribute the IP address to all the corresponding PCs. Vlasne, in such a decision there are pluses and minuses. On the one hand, the presence of a DHCP server will simplify the process of setting up the merge, but there is no need to manually set up the merge on the computers of the hosts. On the other hand, in the minds of the system administrator, it is a typical situation, if no one knows the password for access to the router, and the standard password has been changed. It would have been better, now it’s necessary to “lick” at the router, how does it all work? So it is so, but there are unacceptable blames. For example, the number of computers at the school increased (they possessed another class of computer science), but problems began with IP-address conflicts at the enterprise. On the right, it is not known what range of IP addresses are reserved on the router for distribution by the DHCP server, and it may appear that this IP address is simply not enough. If such a problem is to blame, then the only way to solve it, without climbing into the router itself, is to manually register all the settings (IP addresses, mask for the IP address of the gateway) on the skin PC. Moreover, in order to eliminate the IP-address conflict, it is necessary to create it on the skin PC. Otherwise, manually recognized IP addresses can appear from the range reserved for distribution by the DHCP server, which will lead to an IP address conflict.
Another problem lies in the fact that all computers connected to the switch and able to access the Internet through a router, establish one peer-to-peer local network, or simply work in a group. This working group includes computers installed at the school computer class, and other computers that are at the school. This is the director's computer, the head teacher's computer, secretaries' computers, accounting computers (also in schools), and all other computers with access to the Internet. Of course, it would be wise to break all these computers into groups and recognize the skin group of coristuvachіv vіdpovіdnі rights. But, as we have already appointed, the domain controller has not been transferred to the domain, and it’s simply not possible to implement such a controller. Obviously, this problem can be often found on the hardware level, organizing a small number of virtual local networks (VLAN) and at the same time physically recreating students' PCs from other computers. However, for whom a switcher is needed (or if you want a Smart-switch), the availability of such a school is very rare. Ale navit such a commutator and є, it is necessary to add virtual lines. You can not hack virtual networks, but install an additional router and switch and set different IP-addressing (IP-addresses from different networks) for computers in the class of informatics and solve computers. Ale tse vymagaє dodatkovih vitrats for the provision of a high-quality property and the confirmation of the installation of routers. Unfortunately, it is not possible to solve the problem of under the school computers on the isolation of one group without additional financial investments (the presence of a ceramic switch at the school is a culprit from the rules). At the same hour, a similar one was not obov'yazkovym. In order to consider the need for such a field from the point of view of the security system, the problem of the security of computers and administration in the face of encroachment on the side of the school can be solved in another way.
2.4 Server setup
Choosing the Ubuntu operating system based on the ability to know great insightful information on the topic, what to say, what rich support is given to the operating system. The additional factor was the special advantage of the authors of the Debian family of operating systems, based on their own tool for detecting package fallacies.
Specializeddistribution kitOSubuntuForvictoriaїїVyakostiserver roomOSNotnecessary. For installation, a 32-bit architecture was selected, and for saving installation time, a simple installation method was selected through the GUI.
Nalashtuvannyalocalmerezhiinterfaces
For the organization of the merging in the first place, the next step is to create a "naming" of the merging card. Since there is only one, then I will be called eth0. To eliminate the conflicts in the mesh, the patching is required when the mesh cable is connected. When you fix it, edit the system file /etc/network/interfaces .
$ sudo gedit /etc/network/interfaces
# Merezheva loop
auto lo
iface lo inet loopback
# Main local interface
auto eth0
iface eth0 inet static
address 192.168.0.1
netmask 255.255.255.0
network 192.168.0.0
broadcast 192.168.0.255
# The main interface for accessing the Internet
autoeth0:1
iface eth0: 1 inet static
address 172.16.0.2
netmask 255.255.255.0
network 172.16.0.0
broadcast 172.16.0.255
gateway 172.16.0.1
Access to the Internet has been set in the range 172.16.0.0/24 for an explicit sub-line. To select a given address range, as another add eth0, a virtual other addon eth0: 1 was selected, so the alias ranks. It can be seen that the router, which takes the role of the NAT server and the router for Internet access, has a local address of 172.16.0.1. A wide range, visions of exchange data between a server and a router, tasks with the method of a simple alternative setting up in the future and unique possible conflicts in the borders, shards of this range are rarely victorious in local borders.
To fix the configuration, the command to restart the daemon was fixed:
$ sudo /etc/init. d/networking restart
VkazivkaforeignfilteringDNSservers
To set up a DNS connection, you need to edit the file /etc/resolv. conf. For editing files in vicorists, all addenda gedit, if it can be used in the same versions of the distribution kit, then the editor is more universal nano, which is not a custom GUI. It’s too late to see the current file (or create a backup copy by renaming it), and then edit it:
$ sudo rm /etc/resolv. conf
$ sudo gedit /etc/resolv. conf
For the implementation of filtering the views of sites, it was decided to use DNS filtering, since software security for the Russian audience of the Linux OS family was prompted to organize a proxy server, which will require manual adjustment of the parameters in the system. lowering the efficiency of the server zastosuvanya as I will add the administration. For filtering victories, the third-party service Rejector.ru, the servers of which and are due to be specified in the file to be edited:
# Without the filter, enter nameserver 172.16.0.1
nameserver 95.154.128.32
nameserver 91.196.139.174
The values of the IP address, entered to the text file, are not changed indefinitely in the case of the koristuvach.
When restarting the server, there was a problem updating the file /etc/resolv. conf the manager of the network (Network Manager), which allows the installation of fences on the master file. Tsey zahіd є dosit unsafe, to that you can take away the long-term failure of the results with the best third-party tools. To fix the file, the command
$ sudo chattr +i /etc/resolv. conf
NalashtuvannyaNAT& DHCPservers
Further security functions rely on the configured DNS and DHCP servers. The security of your work will be based on a variety of packages dnsmasq. For locking, packages are not included to the standard set of tools, which required installation:
$ sudo apt-get install dnsmasq
Nalashtuvannya tsgogo package dosit simple and field the address of the DHCP server in the specified range. For customization, the next configuration file is generated /etc/dnsmasq. conf:
$ sudo gedit /etc/dnsmasq. conf
Merezha without blame was prompted on the principle of the merezha address, which are dynamically seen, the configuration file will come to that:
# Service server addresses
listen-address=192.168.0.1
# Number of IP-addresses of subscribers to be remembered
cache-size=300
# Range of seen IP address (without statically specified) that hour of life
dhcp-range=192.168.0.101, 192.168.0.250,24h
The external text file should contain a sufficient number of applications and information for detailed adjustment, depending on the needs. After making all the necessary adjustments, restart the daemon robot with new parameters:
$ sudo /etc/init. d/dnsmasq restart
Noticerouting
Note to the robot mode, in which the server assumes the role of a router, is enabled for an additional parameter net. ipv4. ip_forward the value of which is set equal to 1 in the configuration file /etc/sysctl. conf.
$ sudo gedit /etc/sysctl. conf
A cardinal change in the text can lead to serious unfavorable consequences, shards in which case fine-tuning of the kernel parameters is necessary, so it is necessary to create a backup copy. At the file, it is necessary to comment on the next row for secure routing:
net. ipv4. ip_forward=1
To change the flow state of the kernel without re-immobilizing the system, you can re-immobilize the system, or immediately stop the command:
$ sudo sysctl -p
The final touch on the borders is the rules for redirecting packets. These rules must be specified for the hour of the system's advance, to that it is additionally specified for automatic departure for the hour of the system's advance. Which file was edited for / etc/ rc. local.
$ sudo gedit /etc/rc. local
For this file, it is necessary to specify the same commands for keruvannya between the screen. The success of the victorious is re-evaluated according to the meaning of the victorious scenario. Vidpovidalnist for the value that turns, is equal to locking 0, lying on the shoulders of the file that is editing. Commands are victorious as root, it is necessary to indicate the name of the oblіkovogo record, in the name of which the vikonan is to be victorious. For this reason, a public record of serveruser was created, a kind of vikoristovuvavsya at the administration of the server. The results before the exit of the scenario (exit 0) had the next row added:
sudo -u serveruser -Hiptables -P FORWARD ACCEPT
sudo -u serveruser -Hiptables - -table nat -A POSTROUTING -o eth0 -j MASQUERADE
The re-verification of practicality was carried out by the way of the offensive team:
$ sudo /etc/init. d/rc. local start
Filtration system management
Rejector.ru service, which is a clone of the OpenDNS service and insurance coverage for the Russian audience, was selected for the selection of vibratory filtering services. The efficiency of the service lies in the conciseness of the services, which we hope for: simple adjustment of the filtering parameters, as well as the selection of statistics of blocked resources. Nezaperechnoy perevagoyu є mozhlivist koristuvachevі povіdomiti administrator about incorrectly categorizing the resource.
Filtering categorization
Registration on the website of the service gives the possibility to configure filtering parameters. The set of rules is set up for the singing of the mourning, as it is necessary to create. To create a border on the side, which is on the menu Panel management > Merezhi, the bula was created with a dynamic IP address under the name namewebs118 that ID idwebs118(baby 1).
1. The creation of parameters in the measure.
After the creation, it was possible to edit the text of the side of the fence. E-mail of the administrator of the letter of order with the method of zapobіgannya sprobi vykoristannya addresses by an improper rank of dissatisfied koristuvachs. The text of the viishov's side will come:
Oh, the site DOES NOT tell you about the process of learning!
Access to the resource is blocked!
Send a request to the site administrator
%user_query_form%
As a result, the party made a record, submissions for little 2:
Malyunok 2. Merezhi Koristuvach.
Filtering parameters are adjusted on the side Panel management > Filter. From the proposed options, the work was collected Individual Filter(Figure 3). Choose a category of fences for koristuvachas to review the resources of this category.
Figure 3. Categories of individual filtering.
At what stage the main adjustment of filtering can be done as a final step. All requests for correspondence with incorrect categorization of resources will be sent to E-mail, instructions for registration on the service.
Integrationserviceіservers
The complexity of the filtering, which is done, is based on the dynamic call IP address of the local network, as it does not appear to the master of the permanent call IP address. We have reviewed the task of specifying the IP address of the system Rejector.ru for a specific koristuvach For which creations, the scenario looks like this:
#! /bin/bash
# Paremetry of the service provider Rejector.ru
username=your_login # E-mail
passwd=your_password # Password
ipname=your_merge_address # IP addresses of the merge
log_dir= $HOME # Directory for viewing results
log_file=rejectorupd. log #File output results
date >> $log_dir/rejectorupd. log
/usr/bin/curl - i - m 60 - k - u $username: $passwd "http://updates. rejector.ru/nic/update? hostname=ipname" - silent >> $log_dir/$log_file
echo -e "\n" >> $log_dir/$log_file
For this script, you may need a package, which can be installed with the command:
$ sudo apt-get install curl
As a result, the script is written to a text file, in this folder ~/rejectorupd. log, display information about the results of vikonannya. A positive result will be at the time of the word good for example, dermal recording.
Vikonannya of which scenario can be tied to the singing intervals of an hour for the help of a demon Cron . For whom the script is placed in the home folder under the name rejectorUpdate. sh. The customization of this script is edited by editing the Cron daemon configuration file:
$ crontab - e
Vіn bude vykonuvatisya in the name of the streaming koristuvach, shards of descriptions more script transferring the variant of the home directory to save the results in the same script. In the text file, you need to add a row to the weekly command at the song hour. Our mood has an interval of one year, and the vicinities of the skin 5 times of the new year:
5 * * * * bash rejectorUpdate. sh
For a robot named after a supercorristor, you can buti vikoristan another team (did not stop at this robot).
2.5 Creation of a koristuvachіv group and adjustment of access rights
VNC clients are included as standard with Ubuntu Desktop. On a computer with Ubuntu, as we choose keruvati, let's go to the menu "System - Parameters - Remote working style" and install it as necessary. First, check the box "Allow other coristuvachas to check your work style", as it is necessary to allow them to check - put a check mark on a friend as well. At the bottom, on a yellow background, there is information about those who can connect to your computer from a local network via the Internet.
Another important point: do not forget to set the parameters for access to your computer, such as allowing skin login, otherwise we need a password for access to the computer. I do not recommend setting up the option of free access without a password and without permission - all the same, the time is not calm for merezhi =).
As you can see the effects of the work table, it is necessary to turn on the remote access session for an hour, otherwise, remote access or else it is not practical.
As soon as we can connect to our Ubuntu or Windows machine. To connect from Ubuntu, you don’t need to install any of the add-ons: just go to the menu "Add-ons - Internet - Look at remote desktops", press the "Connect" button in the toolbar, select the VNC protocol and enter the computer name in the locale niy merezhі or yogo The IP-address field is "Vuzol", at the bottom there are additional parameters for your analysis: "Full-screen mode", "Only glance", "Scale". You can connect.
In addition, you can hack alternative VNC clients for Linux, one of which is gtkvncviewer. Yogo can be installed with the command
sudo apt-get install gtkvncviewer
Windows VNC. Setting up UltraVNC.
For working with VNC on Windows, we will use the UltraVNC package. Previously, I used another package - RealVNC, a proteogo server part in a non-combat version does not work under Windows Vista, 2008 and 7, so I can see UltraVNC itself, although it is more foldable in the installed version. If you win Windows 2000 or XP, you can try to install RealVNC yourself, you can download it on the official website: http://realvnc.com/products/free/4.1/download.html.
UltraVNC is available here: http://www.uvnc.com/download/index.html (choose the remaining version, then choose the Full version, then win32 for the original 32-bit OS, or X64 for the 64-bit OS).
Let's start the installation. On the "Select Components" short, you need to choose the type of installation, I'm not going to report on it - I'll check it out myself, I recommend just choosing "Full Installation" - I'll install it again in that case, so the machine will be connected to it. If not, select "Viewer only" - only a client part, so that you can connect from your computer.
If you have Windows Vista or 7 installed, then the installer will also try to take advantage of additional non-valid components, without any versions of Windows, the image will be tampered with and will not be able to pass the onslaught of the "ctrl + alt + del" keys. I strongly recommend installing them by checking the "Download Vista addons files now" checkbox.
Let the installer tell you to install the "Mirror Driver", when the screen is updated, it will appear faster, and the load on the central processor will decrease by a factor of 1. I recommend installing yoga by checking the "Download the mirror driver" checkbox.
The next step is especially important, as you install the program at once from the server part. Choose:
"Register UltraVNC Server as system service" - register the server as a system service. It is important, if desired, that the server part starts itself when the computer is turned on and runs in the background.
"Start or restart UltraVNC Server" - start or restart the server service AT ONCE (it's a shame, otherwise you have to restart the computer to start the service).
"Create UltraVNC desktop icons" - create icons on the desktop (your choice).
"Associate UltraVNC Viewer with the. vnc file extension" - associate files. vnc from the program (bazhano means).
"UltraVNC Server driver install" - installation of the server driver (required by language).
After the completion of the installation from the server part, we will be asked to repeat it once and for all. I won’t explain all the points of the installation - let’s talk about the most important:
Shared "Authentication":
"View-Only Password" - the password for connecting in the review mode (only be careful not to use the keyboard and the mouse, I recommend it!).
Shared "File Transfer":
"Enable" - to enable.
Shared "Misc.":
"Remove Aero (Vista)" - turn off the Aero effect for the client's connection time. In the region it is recommended to move the code.
"Remove Wallpaper for Viewers" - Don't show desktop wallpaper to clients. In the region it is recommended to move the code.
"Capture Alpha-Blending" - enhances transparency. Not recommended for promotion of swedcode.
"Disable Tray Icon" - clean up the icons in the system tray (tray). In this way, you can attach the server to the robot.
"When Last Client Disconnects" - what does it do if everything is connected:
"Do Nothing" - do nothing
"Lock Workstation" - lock the screen
"Logoff Workstation" - log out of the oblіkovogo record
All. If the server is installed, you can connect to a new one, moreover, like with Windows, so with Ubuntu, or be it some other system, where the VNC client is installed.
To connect to another Windows machine, use the UltraVNC Viewer shortcut: here you need to enter the IP address of either computer in the local area in the "VNC Sever" field. You can also use the "View Only" option - reviewing the screen without looking through the computer.
Axis, principles, and everything. To be honest, on the cob of writing these articles and I myself did not check what is in the bare only installed Ubuntu, you can so easily and without problems create remote access to the working table. Like a bachite, it's much easier for a similar task for Windows.
Obviously you can rebuke me by saying that Windows can have its own protocol for remote control of the RDP desktop, which is used by standard methods - I can't wait for you.
In the past, RDP cannot be broken just like VNC for such tasks, like “helping others”: when connected to a computer, it’s cleared, the local root is broken from the cloud record, otherwise the hard disk is guilty personal record.
At the same time, as in the distance, the VNC is working with the local one in one session (does not stick only another cursor =)), which allows you to demonstrate how to see each other through the mesh. Well, in a different way, they use excellent RDP clients for Linux, for example - krdp, but then RDP servers for other systems, Windows windows - no, so in terms of cross-platform solutions, Micrsoft services, as it sounds, are left behind.
Koristuvachi,groupieіrightsaccess
Now let's talk a little about the separation of access rights to various elements. The descriptions of this article are the main mechanism in Linux and in Ubuntu, please read carefully.
Coristuvachi and groupi
Linux zagalom and Ubuntu zokrema - systems for insurance on a lot of coristuvachiv, tobto. on one computer, you can have a few different koristuvachiv, skin with your own power settings, giving it access rights to various system functions.
Krim koristuvachiv Linux for demarcation of rights to establish groups. The skin group, as a member of the group, can automatically set access rights to various components of the system, and the skin group, a member of the group, automatically revokes all the rights of the group.
Tobto groups are needed for the grouping of koristuvachs according to the principle of the same importance on a be-yaki diї, the axis is such a tautology.
Leather koristuvach can be transferred to the non-exchangeable number of groups and in the dermal group can be scalable always koristuvach 1) .
For example, in Ubuntu there is one core group: admin. Whether a member of this group will receive non-negotiable administrative privileges. I have already told you about the role of an administrator in Ubuntu, so that you have already caught someone else, you can refresh your knowledge.
Koristuvach, which is created every hour when Ubuntu is installed, automatically becomes a member of the admin group.
You can cook with koristuvachs and groups with the help of a special tool that is on the menu System>Administration>Koristuvachі і groupie.
Vzagali main area zastosuvannya mechanism koristuvachіv that group є not zovsіm razmezhuvannya access to rіznіh funktsіy sistemy, but rather razorіvannya access to files on the hard drive 3). Axis about tse I'm going to look at the distance.
Permissions to Linux
Whether there is a file and a directory in Linux, there is a koristuvacha-vlasnik and a group-vlasnik. So be it a file and a directory to lie with my coristuvachev system and that group. In addition, whether a file or a directory has three groups of access rights: one for the koristuvach-vlasnik, one for the members of the vlasnik group, and one for all other koristuvachiv systems. The skin group is composed of the rights to read, write and run the file on the screen. For catalogues, the right to read and the right to read must always go together and mean the same.
To change the master of that chi іnshoy file and different groups of access rights to the new one, you can hack the access to that file. For example, if you have created a file for yourself as a vlasnik and have blocked access to a new, crim koristuvach-vlasnik, you can attach it to the file for all other koristuvachivs. This is the thing to go through catalogs. It is possible, for example, to save files in the directory, or else to take them from third-party eyes.
To tell us one very important consequence of such an organization of access rights to the system. A specific Ubuntu coder should have only one home directory and the whole of it. For the system, this directory is located behind the address /home/im'ya_koristuvacha. All other files of the system, including all programs, system settings, etc., which are located in the /home position, are more important than root. Keep in mind that I said that root is a privileged person who has no middle ground in Ubuntu. So the axis, all system files and directories should not be rooted for no reason, we have set the rights to change only for the koristuvach-vlasnik, so nothing, around root, can not get into the robot of the system and change the system files.
So, obviously, it’s better for security, but how about working, how do you need to change some of the system files? There are two paths here 4): first, more necessary system settings can be changed with the rights of an administrator from graphical configurators, in the best way. Well, in a different way, you can temporarily raise your rights to root and work for everything that is worth it.
Rush for the help of the sudo utility and її pokhіdnyh. sudo is not a console utility. Vaughn allows you to "pretend to be" a root with a specific command, thus taking away the necessary rights. For example, the team
sudo aptitude update
Update data about programs available to you (I will explain this later in the article about program management). The team itself
aptitude update
pracyuє only її її start root. However, running її for the help of sudo you see yourself as a root, without being a root with it. Naturally, for vikoristannya sudo and guilty mother rights of the administrator 5) . When you run the command through sudo, the system will supply you with your password, and with a security method, when you enter it, nothing will be shown to you, no star, no little picture, no bird, nothing. Don't fawn, so it's required, just enter to the end and press Enter. If you are an administrator and have entered the password correctly, then the sudo command is issued after the root name.
Through the terminal you can get everything you need, so that if you can become a root, you can download everything you need. However, sometimes you can manually type in graphic programs, with which you can use the rights of the root. For example, if you need to copy files to system directories. To launch graphics programs as root, open the GNOME launch dialog by pressing Alt+F2 and enter
gksudo im'ya_programs
For example, to launch the Nautlus file manager, you need to run
gksudo nautilus
By launching Nautilus in this manner, you can easily change files on your computer.
Be respectful when using Nautilus as root! You can, without any delay, irrevocably see whether there is a system file, which can calmly bring the whole system to impracticality.
Editing configuration files
The most important butt of the zastosuvannya technology described above is "imagining" the root є editing the configuration files of the system. I've already shown that all system setups and all add-ons in Linux are saved from looking at text files. So the axis, you can only edit the files that you need to lie down, so that it’s more than a fix, that your koristuvach is worthy of. And for editing system parameters, you need administrator rights.
You can open a lot of files, but if you can’t change it, you simply won’t be able to save the operation.
Obviously, you can open the configuration files with root rights through the program start dialog with the command
gksudo gedit /way/to/file
Gedit is the default Ubuntu text editor.
However, auto-completion does not work for the launch dialog, so you have to manually type the path to the file, so you don’t manually enter it. To launch a text editor, you can use the name of the super-correct vicorist to create a terminal, for example:
Crap, because sudo is just a console utility, so you can’t win in the dialog to launch the program, although you can run graphical programs from the terminal through it. Аgksudo navpak, graphic utility, that її not varto vykorovuvat in the terminal, although it is not fenced.
The result is noted by the editor from the possibility of saving changes:
Visnovok
Local enumerations in the present hour have become wide-spread in various fields of science, technology and chemistry.
The development of collective projects, for example, folding software systems, is especially widespread.
On the basis of LOM, it is possible to create automated design systems. This allows the implementation of new technologies for the design of machine-building, radioelectronics and computational equipment.
In times of development of the market economy, it is possible to create competitive products, quickly modernize them, ensuring the implementation of an economic business strategy.
LOM also allow the implementation of new information technologies in the systems of organizational and economic management. The use of merging technologies significantly facilitates and speeds up the work of the staff, allows the selection of single data bases, and also regularly updates and processes them promptly.
Choose the type of the fence, the method of installing computers in the fence, to lie down like in the technical ones, so important, in the face of financial possibilities, it’s quiet, who I’m doing.
Otzhe, at the graduation robot, the assignment was completed, and itself:
· Theoretical material from local measures
· Promoted to a local measure at school
· Established remote access for access to computers
· Nalashtovaniy file, and the Internet server s content-filter ohm.
This diploma work will help the teacher of computer science to organize a local network among schoolchildren, because all the necessary information is presented in this diploma work.
List of references
1. Bashley P.M. Modern mezhezhiv technologies: heading help, - M., 2006
2. Boguslavsky L.B. Management of data flows at the enterprises EOM, M. - 1984
3. Melnikov D.A. Information processes in computer networks. Protocols, standards, interfaces, models ... - M: KUDITS-OBRAZ, 1999.
4. Morozov V.K. Fundamentals of the theory of information measures. - M., 1987
5. Khonnikant D. Vyvchennya Internet. Kiev-M. - St. Petersburg, 1998
6. Evolution of computational systems [electronic resource]: http://sesia5.ru/lokseti/s_11. htm
7. Communication lines [electronic resource]: http://sesia5.ru/lokseti/s211. htm
8. Olifer V.G., Olifer N.A. Computer systems. Principles, technologies, protocols: Handbook for universities.2-vid. - St. Petersburg: "Piter", 2005. - 864 p.
9. Computer systems. Primary course / Per. from English - M: Vidavnichiy viddil "Russian redaktsiya" TOV "Channel Trading Ltd.". - 2nd issue, 1998. - 696 p.
10. Robots at the beginning. Firm standard FS RK 10352-1910-У-е-001-2002. Zagalni vimogi until wake up, vikladu, formalized and zmistu. - Almaty, АІES, 2002. - 31 p.
11. Fundamentals of modern computer technologies: Pdruchnik / Ed. Prof. HELL. Homonenko. - St. Petersburg: CROWN print, 2005. - 672 p.
12. Soloviova L.F. Merezhev technologies. Handyman-workshop. - St. Petersburg: BHV-Petersburg, 2004. - 416 p.
13. Novikov Yu.V., Kondratenko S.V. Local dimensions: architecture, algorithms, design. - M: ECOM, 2001 - 312 p.
14. Guk M. Apparatus zasobi local merezh. Encyclopedia - St. Petersburg: View "Piter", 2000. - 576 p.
Placed on Allbest.ru
Similar documents
Ways to connect different computers to the next. The main ambush of the organization of local enumeration measures (LAN). Development and design of local enumeration measures at the enterprise. Description of the selected topology, technology, standard and possession.
thesis work, donation 06/19/2013
The creation of a local counting system, topology, cable system, technology, hardware and software security, minimal support to the server. Physical encouragement of local networks and organization of access to the Internet, development of the cable system.
course work, donations 05/05/2010
The concept of local enumeration, the architecture of computer networks. Local setup of computers. Installing the oblіkovogo record of the administrator. Enhancement of anti-virus security. The structure of the service delivery of the computer system.
thesis work, donations 01/15/2015
Local counting of the line, commutation nodes and lines of communication, which will ensure the transmission of data to the coristuvach line. Channel line of the OSI model. Scheme of distribution of computers. Rozrahunok zagalnoy dozhini cable. Software and hardware security for local networks.
course work, donations 06/28/2014
Obґruntuvannya modernization of local counting measures (LAN) enterprises. Possession and software security of LOM. Choice of topology, cable and switch. Vikoristannya and nalashtuvannya Wi-Fi - access points. Security of trust and security of measure.
thesis work, donation 12/21/2016
Choose and install the SOS Ubuntu Server. Description of the physical scheme of the telecommunications facility that is being designed. Setting up servers, computers and software security.
course work, donations 06/12/2014
The structure of the local computer network organization. Rozrahunok vartosti pobudov local merezhі. Local arrangement of organization, designed by technology. Pobudov local networks of Ethernet organizations. 10Base-T local network scheme.
course work, donations 06/30/2007
Methods for classifying measures. Rozrobka and description of the structure of the local counting line, roztashovanoy in the five-surface bud. Technical information, topology of archeology. Customer hardware security. Installed and configured the server.
course work, donations 07/27/2011
Investigation of parameters in the design local calculation measure. Zagalna dozhina cable. Rozpodіl IP-address for the designed measure. The specificity of the possession of that stained glass materials. Selection of the operating system and application software.
course work, donations 11/01/2014
Designing local networks and providing telecommunication services to local residents. Structured cable systems, functions. Work space, telecommunications closet. The method of laying the cable installation, which is victorious in the design of LOM.