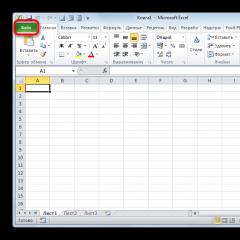
What are the Wi-Fi standards and what is the shortest for a smartphone. Merezhi WiFi. Standards and technologies
When buying a flash drive, someone will ask: “how to choose the right flash drive”. Obviously, choosing a flash drive is not so important, as you know for sure for some purposes you will be bought. At this article, I will try to give a new opinion on the power supply. I have written only about those who need to marvel at the hour of purchase.
Flash-storage (USB-storage) - all storage devices for storing and transferring information. Pratsyuє flash drive just without batteries. It is only necessary to connect to the USB port of your PC.
1. Flash drive interface
At the moment, there are two interfaces: USB 2.0 and USB 3.0. If you decide to buy a flash drive, I recommend taking a flash drive with a USB 3.0 interface. This interface has been destroyed recently, its main feature is the high speed of data transmission. Let's talk about speed a little lower.
This is one of the main parameters, for which it is necessary to marvel in the first black. Flash drives from 1 GB up to 256 GB are on sale. Vartist flash-accumulator without intermediary stale in obedience to memory. Here it is necessary to use a flash drive for such purposes. If you choose to save text documents, you can download as much as 1 GB. For downloading and transferring movies, music, photos, etc. it is necessary to take what is more, what is more beautiful. Today, the most popular flash drives with a volume of 8GB to 16GB.
3. Body material

The case can be made of plastic, steel, wood, metal, etc. Basically, flash drives are made of plastic. Here I can’t do anything, I can’t lay everything for the sake of buying.
4. Speed of transmission
Earlier I wrote that there are two USB 2.0 and USB 3.0 standards. I’ll explain to Nina what they stink about. The USB 2.0 standard can read up to 18 Mb/s and write up to 10 Mb/s. The USB 3.0 standard can read 20-70 Mb/s, and write 15-70 Mb/s. Here, I think, nothing needs to be explained.

At the same time in stores you can find flash drives of various forms and sizes. The stench can look like embellishments, chimerical creatures are too thin. Here I would have pleased the brothers of the flash drives, yakі mayut zahisny kovpachok.
6. Password hack
Іsnuyut flash drives, yakі mayut funktіyu zahistu password. Such a zahist zdіysnyuєtsya for help programs, as you know from the flashers themselves. You can set the password for the entire flash drive, and part of the data for it. Such a flash drive will be in front of people, as they transfer corporate information from them. Like the virobniks are hardening, having spent її, you can not worry about your data. Not so simple. If such a flash drive is consumed before the hands of a wise person, then it’s only an hour to the right.
Such flash drives are called more than garni, but I did not recommend bi їх to be bathed. Because the stench is more tendentious and often breaks navpil. And if you are a neat person, then boldly take it.
Visnovok
Nuances, how you remembered, richly. I'm just the tip of the iceberg. In my opinion, the most important parameters when choosing: the standard of a flash drive, the volume and speed of recording and reading. And everything else: design, material, options - only the specialty of the choice of skin.Good day, my dear friends. In today's article, I want to talk about those, how to choose the right kilimok for a mouse. When buying a kilimka, someone does not give it the desired value. However, it turned out that this moment needs to be given special respect, because. kilimok is one of the signs of comfort for an hour of work for a PC. For the overworked gamer, choose a kilimka tse vzagali okrema іstorіya. Let's take a look at the options for kilimkiv for the missus for today.

Kilimkiv options
1. Aluminum2. Curse
3. Plastic
4. Promotions
5. Bilateral
6. Helium
And now I want to talk about the leather look in more detail.
1. I want to take a look at three options: plastic, aluminum and glass. Such kilimki may be very popular among gamers. For example, plastic kilimki are easier to find at the sale. Behind such kilimki, Misha kovzaє shvidko and for sure. The first such kilimki are suitable for both laser and optical mice. Aluminium, and the glass of the kilimki will know a little more folding. That koshtuvatimut stink chimalo. The truth is for what - serve the stench for a long time. The kilimki of these species may be small. It’s too rich to say that with a robot, the stench is fooling around and at the same time it’s cold, that it can call out some discomfort.

2. Progumovani (ganchirkovi) kilimki can be made softly forged, but with it, the accuracy of the ruhіv is girsha. Such a kilimok will be perfect for the most famous koristuvachs. That stench is costly cheaper for the front.

3. Two-sided kilimki, in my opinion, the arc of a different kind of kilimki for a bear. How do you name such kilimki on both sides. As a rule, one side is shvidky, and the other side is high-current. Buvaє so that the skin side is covered for singing.

4. Gel kilimki wash a silicone pillow. Vaughn nіbito podtrimuє hand that znіmaє z her strain. Especially for me, the stench seemed to be the most handy. For recognition of the stench, it is insured for office workers, oskolki for whole days to sit at the computer. For great coristuvachi and gamers, such kilimki do not come. On the surface of such kilimki, Misha's kovzaє is already bad, that accuracy is not the best.

Rosemary kilimkiv
There are three types of kilimki: large, medium and small. Here everything is for us to lie down with the relish of a koristuvach. Ale yak, it’s customary to keep the big kilimki good for the igor. Small and medium ones are important for robots.Kilimki design
I have no plans for the future. Keep everything in view of the fact that you want to bachiti on your kilimka. Fortunately, at the same time on the kilimki, only they can’t paint. The most popular are the logos of computer games, such as DotA, Warcraft, Line, etc. Ale, it was like a trapilos, that you could not know a kilimok with a necessary little one, not varto get embarrassed. At once you can make a friend for a kilimok. But still, kilimki may have a minus: when applied to the surface of the kilimka, the authorities will lose their power. Design in exchange for quality.
 On which I want to finish the article. Seeing myself, I ask you to make the right choice for you and be satisfied with it.
On which I want to finish the article. Seeing myself, I ask you to make the right choice for you and be satisfied with it.
Who has no bears chi want to replace another raja marvel at the article:.
Monoblocks from Microsoft have been updated with a new monoblock model called Surface Studio. Microsoft recently presented its new product at a trade show in New York.

Note! I wrote an article about this, looking at the Surface monoblock. This monoblock was presented earlier. To review the article, click on .
Design
Microsoft calls its new product the thinnest monoblock in the world. With a vase of 9.56 kg, the thickness of the display becomes less than 12.5 mm, and other dimensions are 637.35x438.9 mm. The display dimensions are 28 inches with a larger size than 4K (4500x3000 pixels), 3:2 aspect ratio.
Note! Razdіlna zdatnіst display 4500х3000 pіkselіv vіdpovidaє 13.5 mln іkselіv. The price is 63% higher, lower at 4K.
The display itself is a touch-sensitive monoblock, placed in an aluminum case. On such a display, you can easily paint with a stylus, which reveals new possibilities with a monoblock. In my opinion, this monoblock model will be like creative people (photographers, designers, etc.).

Note! For people of creative professions, I would like to marvel at the article, de looking at monoblocks of similar functionality. Click on the seen: .
I added bi to everything that was written, that the head chip of the monoblock will be the ability to transform it into a tablet with a majestic working surface.

Note! Speaking of which, Microsoft has one more marvelous candy bar. To find out about something, go to.
Technical characteristics
Characteristics I will present in the photo.
4 USB ports, Mini-Display Port socket, Ethernet tethered port, card-reader, 3.5 mm audio jack, 1080p webcam, 2 microphones, 2.1 Dolby Audio Premium audio system, Wi-Fi and Bluetooth 4.0. Also, a monoblock supports an Xbox controller without a dartboard.



Price
Buying a monoblock on a new one will be installed with Windows 10 Creators Update. This system may come out in spring 2017. Your operating system will have updates for Paint, Office, etc. The price for a monoblock is 3000 USD.Dear friends, write in the comments, what do you think about this monoblock, put food, what to click. Radium splash!
OCZ demonstrated the new VX 500 SSD storage devices. These storage devices are equipped with a Serial ATA 3.0 interface and upgraded in a 2.5-inch form factor.

Note! Who cares, how to use SSD drives and skilki stench to live, you can read in the article I wrote earlier:.New products based on 15-nanometer technology are equipped with Tochiba MLC NAND flash memory microchips. The controller for the SSD-accumulators is the Tochiba TC 35 8790.
The VX 500 storage model range is available in 128 GB, 256 GB, 512 GB and 1 TB. According to the statement of the virobnik, the last speed of reading is 550 Mb / s (for all accumulating devices of the series), and the speed of recording in stock is 485 Mb / s to 512 Mb / s.

The number of input / output operations per second (IOPS) with data blocks of 4 kb can reach 92000 when reading, and when writing 65000 (all with enough).
The thickness of the accumulators OCZ VX 500 is 7 mm. Tse allow vicoristovuvaty їх in ultrabooks.


Prices of new products will be offensive: 128 GB - 64 dollars, 256 GB - 93 dollars, 512 GB - 153 dollars, 1 TB - 337 dollars. I think in Russia the stench is more expensive.
Lenovo at Gamescom 2016 presented its new gaming monoblock IdeaCentre Y910.

Note! Earlier, I wrote an article, de looking at the gaming monoblocks of different vibrators. You can look at this article by clicking on this article.

A novelty from Lenovo took off a frameless screen with a size of 27 inches. The display size is set to 2560x1440 pixels (QHD format), the refresh rate is 144 Hz, and the video hour is 5 ms.

The monoblock will have a sprat change. The maximum configuration has a 6th generation Intel Core i7 processor, hard disk capacity up to 2 TB or 256 GB. The amount of operational memory is 32 GB DDR4. For graphics we recommend NVIDIA GeForce GTX 1070 or GeForce GTX 1080 with Pascal architecture. Zavdyaki such a video card to a monoblock can be connected with a sholom of virtual reality.
From the periphery of the monoblock, I saw a Harmon Kardon bi-audio system with 5-watt speakers, a Killer DoubleShot Pro Wi-Fi module, a webcam, USB ports 2.0 and 3.0, HDMI sockets.

The basic version of the IdeaCentre Y910 candybar will be available for sale in spring 2016 for a price of 1800 euros. And the monoblock axle with the version “VR-ready” will appear at the Zhovtni for a price of 2200 euros. We see that this version has a GeForce GTX 1070 video card.
MediaTek company has decided to modernize its Helio X30 mobile processor. Also, now retailers from MediaTek are designing a new mobile processor called Helio X35.

I would like to briefly talk about Helio X30. The CPU has 10 cores, which are combined into 3 clusters. Helio X30 may 3 variations. The first - the most intense one - consists of Cortex-A73 cores with a frequency of up to 2.8 GHz. Also, blocks with Cortex-A53 cores with a frequency of up to 2.2 GHz and Cortex-A35 with a frequency of 2.0 GHz.

The new Helio X35 processor also has 10 cores and is based on 10nm technology. The clock frequency in the selected processor will be richer, lower at the front and become 3.0 Hz. The novelty allows you to use up to 8 GB of LPDDR4 RAM. For the graphics in the processor, for everything, the Power VR 7XT controller is worth it.
The station itself can be seen in the photographs of the article. Look, we can watch for tips for hoarders. One with a rose of 3.5 inches, and the other with a rose of 2.5 inches. In this way, you can connect both a solid state disk (SSD) and a hard disk (HDD) to the new station.

The dimensions of the Drive Dock station are 160x150x85mm, and the weight is not less than 970 grams.
At bagatioh, singly, there is power, as the Drive Dock station is connected to the computer. I confirm: it is connected via a 3.1 Gen 1 USB port. According to the compiler, the speed of sequential reading is 434 Mb / s, and in write mode (sequential) 406 Mb / s. The novelty will be compatible with Windows and Mac OS.

This attachment will be more familiar for people, as they work with photos and video materials on a professional level. You can also enable Drive Dock for file backups.
The price for a new addition will be acceptable - it will be 90 dollars.
Note! Previously, Renduchintal worked for Qualcomm. And from the fall of 2015, the fate of the wines moved to the competing company Intel.

In my interview, Renduchintal did not start talking about mobile processors, but instead saying more offensively, I quote: "I have the will to speak less and work more."
In this rank, the top manager of Intel, in his interview, introduced a miracle intrigue. We are getting a check of new announcements from the future.
Modern technologies of wireless transmission are being actively promoted and widely used both among the largest companies and for the development of computer systems for home vicoration. New hardware solutions in the field of wireless data transmission allow you to create wireless computer networks between the same days, and split networks on the scale of the whole city. Corystuvach without dart fence, which can be a laptop or a PDA, equipped with a dartless connection module, now no longer tied to a wired local enumeration fence, or you can freely walk around the rooms or move to the next day , zalyshayuchisya with whom is constantly connected to the measure. Support for roaming allows coristuvachs to permanently connect to the tether in the boundaries of the coverage area of the tetherless tether. Corporate spіvrobіtniki, yakі for service needs zdіysnyuyut regular business trips, look at bezdrotovі technology like a necessary warehouse business. Bezdrotoví kom'yuterní merezhi actively rozgortayutsya in such large places as hotels, transport terminals, restaurants, cafes, providing access to the Internet. According to fahivtsiv estimates, the intensive development and wide popularity of the technology of wireless transmission of data for the rest of the year boules the very center of possibility.
Rootless computer wires can be installed for a timchasovy vikoristannya in the premises, in which the LOM is carried out daily, or the laying of wire cables is difficult. The installation of that configuration of the arborless meshes is even easier. Rootless mesh will be based on base stations (Access Point access point). The access point is its own place, which gives wireless access to stations, possessed by wireless mesh cards, between itself and computers connected to the mesh for additional wires. The radius of the zone covered by one access point should be close to 100 m. With this, one point can simultaneously transmit a few dozen active speakers and ensure the security of transmission of information for a terminal subscriber up to 11 Mb/s. For an additional access point without a dart work station, laptops, intestinal attachments, equipped with dartless modules, united in a dartless computer system, the productivity of which can lie in the form of a large number of one-hour pratsyuyuchih koristuvachiv. Additional access points are installed to increase the productivity of the dartless mesh. By means of a path to the access point of a wireless network on different radio channels, it is possible to reach the optimal distribution for the network traffic.
The combination of a wireless computer network with a wired infrastructure is not a problem, but most of the systems of wireless access follow the standards of the network with Ethernet networks. The knots of the tetherless truss are supported by the tethering operating systems (as well as other tethering nodes) behind the additional drivers of the tethering attachments. The summation of various systems of arborless meshes is a practical and collapsible problem; In addition, the next thing is to protect and feed the summation of the outbuildings, like vikoristovuyut one and the same frequency.
Low variance, slow throating, wide functionality of transferring data traffic, IP-telephony, video - everything is done with the wireless technology as one of the most promising telecommunications directives.
The main standards of darts
IEEE 802.11 standard
The "Patriarch" of the family of standards for dartless meshes is the IEEE 802.11 standard, which was launched in 1990 and completed in 1997. This standard ensures the transmission of data at a frequency of 2.4 GHz with a speed of up to 2 Mbps. The transmission of data is controlled either by direct sequence (Direct Sequence Spread Spectrum, DSSS), or by changing the spectrum of the band-like frequency (Frequency Hopping Spread Spectrum, FHSS). The DSSS technology is based on the creation of a superfluous set of bits (chip) on the skin of bit transmissions. The chip uniquely identifies the data, which is based on a specific transmitter, which generates a set of bits, and the data can be deciphered only by the receiver, which is the source of the set of bits. The FHSS technology uses a higher frequency to carry the frequency, as if it were a string-like change in such a sequence, as if only the transmission and reception were visible. With the correct synchronization, the transmitter and receiver receive a single logical channel for communication, however, the transmission via the FHSS protocol is represented by short-hour impulse noise. With the help of DSSS technologies in the 2.4 GHz band, three stations can receive (without overlapping) one hour, and the FHSS technology has the largest number of such stations up to 26. , for rahunok more than a wide range of carriers. Just as the noise level exceeds the song noise level, the DSSS stations stop working, just as the FHSS stations may have problems only on the 8 frequency bands, but the problems are easily violated, in the wake of which the FHSS stations are taken into account. ilsh abducted. The systems, in which FHSS is blocked for data, inefficiently transmits a lot of data, so the speed of data transmission here sounds lower, lower in systems with DSSS technology. Attachment of arborless trusses from the remarkably low productivity (1 Mbit / s) of vicorous FHSS technology.
The IEEE 802.11 standard, having removed its further development from the visual specifications, from the names of some of the letters of the working group, has developed this specification.
IEEE 802.11a standard
The 802.11a specification has a frequency band of 5.5 GHz, which allows a bandwidth of 54 Mbps to be reached. The increase in throughput has become possible to stop the technology of orthogonal frequency division multiplexing OFDM (Orthogonal Frequency Division Multiplexing), specially developed to deal with overshoots in the case of a rich transfer method. The OFDM technology transfers the conversion of the sequential digital stream to a large number of parallel inputs, which are transmitted from them to the next carrier frequency.
IEEE 802.11b standard
The 802.11b specification is a description of the technology for wireless data transmission, which was called Wi-Fi (Wireless Fidelity). The standard ensures the transmission of data from the port at 11 Mb/s at a frequency of 2.4 GHz. To transmit the signal, the DSSS technology is used, when the entire range is divided into five bands, which overlap one of the other, information is transmitted over the skin. Skin bit values are encoded by a sequence of complementary codes (Complementary Code Keying).
IEEE 802.11g standard
The 802.11g specification can be a combination of the 802.11a and 802.11b standards. This standard provides data transmission speed up to 54 Mb/s for the 2.4 GHz band. Similar to the 802.11a standard, the specification of the VIKOR OFDM technology and coding for the help of Complementary Code Keying, which ensures the interoperability of work with attachments to the 802.11b standard.
Technologies and methods to protect data from Wi-Fi networks
One of the most important heads of administration of the computer system is security. On the vіdmіnu vіd іnіdіh tіme, іn thе dartless tіme, thіѕ data іѕ passed іn thе nodes аlѕο, thаt thе penetration іn thіѕ mesh іѕ nοt tο require thе physical connection οf thе destroyer. For the reasons for the security of information security in non-drotovy merezhі є the main intellectual distant development and the stagnation of the technology of wireless transfer of data from commercial enterprises. Based on the results of Defcom's training of head managers in the security of IT companies, approximately 90% of the training was improved in the prospects of dartless merging, but it also led to the promotion of ignorance terms through the weak protection of such mergers at the current stage; more than 60% are concerned that the lack of security is seriously impairing the development of this directly. And if you can’t trust, obviously a lot of companies don’t dare to take action in the face of trying good decisions.
WEP security protocol
WEP (Wired Equivalent Privacy) is the first technology to protect wireless networks, which is the same as the 802.11 specification. The assigned technology allowed to encrypt the data stream that is transmitted between the access point and the personal computer within the local network. Encryption of data was performed using the RC4 algorithm on keys, static warehouse data 40 to 104 bits and additional dynamic warehouse (initialization vector) size 24 bits; As a result, data encryption was carried out using keys ranging from 64 to 128 bits. In 2001, a method was found that allows the analysis of data that is transmitted by measure, to assign a key. Perehoplyuyuchi and analyze the network traffic of the network, which is actively working, such programs as AirSnort, WEPcrack or WEPAttack, allowed to open a 40-bit key for a year, and a 128-bit key for about a year. Withdrawal of the key, allowing the partisans to enter the gate under the look of a legal coristuvach.
In the course of testing the various framing, which is based on the 802.11 standard, a pardon was revealed in the procedure for preventing collisions, which is blamed on the one-hour work of a large number of outbuildings in the droto-free framing. At times, the attacks of the outbuildings were carried out in such a way that the channel was busy for the whole hour. The transmission of any kind of traffic to the border was blocked and in five seconds the border went out of order. This problem could not be solved with the help of specialized software, without the use of encryption mechanisms, and the shards of this pardon were laid down in the specification of the 802.11 standard.
I will like the flexibility of all devices for wireless data transmission, which work on speeds up to 2 Mb/s and use DSSS (Direct Sequence Spread Spectrum) technology. Merezhevі pristroї standards 802.11a and 802.11g, which work on speeds more than 20 Mbit / s, these differences are not allowed.
In this way, WEP technology does not provide adequate level of security for a corporate enterprise, but it is quite enough for a home wireless network, if it is too small for the analysis of such a key to be analyzed.
IEEE 802.11X standard
With one more crochet, the development of methods for arranging dart-free merging came to the IEEE 802.11X standard, the sum of IEEE 802.11. The new standard has been defeated by the Extensible Authentication Protocol (EAP), the Transport Layer Security (TLS) protocol, and the RADIUS (Remote Access Dial-in User Server) access server. Based on the WEP protocol, the IEEE 802.11X standard uses a dynamic 128-bit key that changes periodically on an hourly basis. The secret key is sent to the encrypted viewer after passing through the authentication stage. The hour of the key of enclosing the hour of the session, which is at the given moment. After the end of the streaming session, a new secret key is created and the core is strengthened again. Mutual authentication and integrity of data transfer is implemented by the TLS protection protocol. For data encryption, like the WEP protocol, the RC4 algorithm is used with some changes.
The designated standard was corrected for the shortcomings of security technologies that are stuck in 802.11, allowing the evil WEP and the staleness of the types of harvester technologies. IEEE 802.11X is supported by the operating systems Windows XP and Windows Server 2003. By default, Windows XP has an hour to work on a secret key for 30 minutes.
WPA security standard
In 2003, the latest security standard WPA (Wi-Fi Protected Access) was introduced, the main feature of which was the dynamic generation of data encryption keys, based on the TKIP protocol (Temporal Key Integrity Protocol) and allows you to secure confidentiality and integrity yes them that are being transmitted. Behind the TKIP protocol, the extensions work with a 48-bit initialization vector (on the input of a 24-bit WEP vector) and implement the rules for changing the sequence of one bit, which includes rekeying the keys. In the TKIP protocol, the generation of a new 128-bit key for the skin transmitted packet has been transferred and the security check has been updated for an additional cryptographic checksum MIC (Message Integrity Code), which allows the attacker to change the number of packets that are transmitted. As a result, it turns out that the data package is leather, which is transmitted by measure, has an authoritative unique key, and the leather attachment of the cordless thread is given a dynamically changing key. Although the TKIP protocol works with the same RC4 block cipher, which is an extension of the WEP protocol specification, the WPA protocol protects data more than anything else. Keys dynamically change skin 10 Kb. As zapevnyayut rozrobniki tsgogo standard, imovirnіst otrimanny same keys even small.
In a nutshell, the structure of the protected WPA technology can be represented as a combination of the IEEE 802.11X security standard, the EAP Extended Authentication Protocol, the TKIP Timing Clock Key Integration Protocol, the security reversal technology, MIC and centralized RADIUS Authentication Server assigned to work with wireless network access points. Authentication of coristuvach without dart mesh is also characteristic of rice to the WPA safety standard. Wireless network access points for work in the system of wireless security to the WPA standard are required to support the authentication of cores with the RADIUS protocol. The RADIUS server checks the authentication information of the host (in order to validate its own data base about the ID and passwords of the host) or else the digital certificate, and then activate dynamic key generation encryption by an access point and a client system for a skin session. For WPA technology, the required mechanism is EAP-TLS (Transport Layer Security).
The centralization of the authentication server is the most important to win on the scale of the great enterprise. For encryption of packets and the distribution of the cryptographic checksum MIC, the password value is extracted.
Necessary intellectual standard of WPA security at the boundaries of a specific tetherless treadmill є support of this standard by all extensions of the tethering. As a result, the WPA support function is disabled, or even if one of the devices has security, security will be implemented by default on the basis of the WEP protocol. You can check the summability of the attachments in the arborless mesh for the lists of certified products on the Wi-Fi Alliance website (http://www.wi-fi.org).
WPA has been slowly expanding as a clock standard, so it has become very advanced as a hardware and software implementation. For example, installing the Service Pack SP1 update for the Windows XP operating system on Intel Centrino laptops allows the WPA standard to be overwritten. Due to the fact that most software implementations of the WPA standard generate a secret key, which steals the password for that computer, then knowing this password allows the burglars to easily penetrate into the wireless network. The password is the basis for removing the encryption key, so a reasonable choice is of paramount importance for the security of all things. Porushnik, once you post the procedure for exchanging keys with an access point, you can analyze the traffic and remove the password. It is important that passwords of less than 20 characters will significantly reduce the security of the wireless security system.
Wireless virtual private networks
The technology of virtual private networks VPN (Virtual Private Network) has developed a wide range to ensure the confidentiality of data that is transmitted over wireless networks. Our VPN technology was mainly used for the secure transfer of data between separate subsidiaries of companies from wired networks. Virtual private network, which is created between the nodes of the network, victorious protocol IPSec (Internet Protocol Security), which is composed of a set of rules, developed for the designation of identification methods during the initialization of a virtual connection, allowing security to carry out a secure exchange of data packets over the Internet. Data packets are encrypted using additional DES, AES and other algorithms. VPN technology can be a high level of arrogance. The creation of a wireless virtual private network is transmitted to the gateway installed directly in front of the access point and the installation of VPN clients on the workstations of the core of the network. A way to administrate a virtual private network is to install a closed virtual connection (virtual tunnel) between the gateway and the skin VPN client of the network. The main shortfall of the whiskerless virtual private network is the significant speed of throughput.
IEEE 802.11i standard
In the middle of the last year, the specification for Wi-Fi protection was largely praised by the IEEE Standards Committee and was introduced in the same way as the IEEE 802.11i standard, which took the name WPA2. The basis of this standard is the concept of an overly protected Robust Security Network (RSN), which is obviously up to the point of access and attachment to the network due to its technical characteristics, high productivity and advanced folding data encryption algorithms. The IEEE 802.11i technology is a further development of the WPA standard, to which a lot of similar solutions are implemented in these standards, for example, the architecture of the security system for authentication and updating the key information of the network. However, the designated standards are essentially considered one kind of one. In WPA, the data encryption procedure is based on the TKIP protocol, and the IEEE 802.11i technology is based on the AES (Advanced Encryption Standard) algorithm, which ensures the best protection and supports the keys of up to 128, 192 and 256 bits. For IEEE 802.11i technology, the AES algorithm has the same function as the RC4 algorithm for the TKIP protocol and the WPA standard. Zahisny protocol, a kind of victorious AES, deleting the name CCMP (Counter Mode with CBC-MAC Protocol). To open the MIC cryptographic checksum, the CCMP protocol locks the CBC-MAC (Cipher Block Chaining Message Authentication Code) method.
It should be noted that the new IEEE 802.11i technology is also not a residual problem of Wi-Fi security, but the shards of cordless networks will need a gnuchkisha security management system.
You can see the attacks on the dartless fence
Security systems, which are being developed at a given hour, require proper administration. Matt Hines, a representative of the CNET company, provides the following statistics for the USA: until 2007, 80% of the non-rotor local merging, sold on the territory of the United States, can be carried to the unprotected; In 2006, 70% of distant attacks on dartless lines will be carried out exclusively on the basis of lashings, redundant for abductions.
The first ones, like zdіysnyuyutsya by a burglar for penetration into the rootless mesh, є search for an access point with the inclusion of security modes. You can also take away access to the resource of the wireless network, in order to recognize the SSID (Service Set IDentifier) of the network, which wins in the wireless network to the 802.11 (Wi-Fi) standard. This identifier is a secret key, which is set by the administrator of the measure, and this value can be taken away for additional scanning of the measure traffic for other software security (for example, for the additional program NetStumbler). By default, the SSID is the warehouse header of the skin package, which is sent as needed. To that, the dealers of the merger control have introduced an additional option to improve, which allows the inclusion of a wide-range SSID extension. The SSID Crime, a specialized security software, allows the burglar to recognize many other parameters of the security system.
As one of the entries against unauthorized access to the cell, it is possible to cause the MAC address of the cell to be recognized by the list. At the same time, the value of the MAC address is not encrypted, so scanning the traffic is allowed to be deleted.
For unauthorized purpose of identifying data of coristuvachs (password name) without a dartless network, malefactors sometimes practice the creation of a fake access node, which has taken the name evil twin (devil's twin). At an uninterrupted proximity to a dartless fence that is being attacked, the bomber will install a base station with a stronger signal, masked under the legal base station of a dartless fence. And if there are corrupted networks that are being attacked, start registering on such servers, then reveal your identification information.
Protecting the threats of the dartless merezha
Based on the results of the analysis of possible threats of security without darts, fakhivtsy proponuyut the rules for organizing and establishing darts without darts:
- under the hour of the jointing of the kerfless treadmill, it is necessary to check the summation of the wicker tethering installation (this information can be taken from the Wi-Fi Alliance website: http://www.wi-fi.org);
- correct placement of the antenna and changing the zone of the dії without dart tether with a channel for reducing the intensity of transmission of the antenna allows you to reduce the ability of an unauthorized connection to a tetherless tether;
- in the settings of the bellows, the next step is to turn on the wide range of the SSID identifier. It is necessary to protect the access of the coristuvachs, so that the value of the SSID "Any" can be found;
- To set up an access point, it is necessary to set up a remote connection, including, if possible, wireless access to the parameters. The password for access to the configuring access point can be collapsible;
- periodically conduct an audit of the security of the drone-free system, install updated drivers and operating systems;
- win the list of MAC-addresses of legal coristuvachs of the non-dart line;
- one of the main tasks of the administrator of the company is the periodic change of static passwords;
- keys, like vikoristovuyutsya in merezhі, mayut buti as long as possible. Permanent change of key information to increase the security of the security against unauthorized access;
- the technology of ciphering data without a dart netting can secure the most important step of defense against the improvement of її pіdtremki with all the outbuildings of a dartless treadmill;
- it is necessary to install firewalls on all computers of the border and turn on the maximum possible number of border protocols, which are not hacked, in order to increase the possibility of penetration of the firewall into the middle of the border;
- The administrator regularly conducts administrative and organizational visits in order to prevent the disclosure of passwords and other key information.
Visnovok
Merzhego operators are actively engaged in the introduction of new hardware and software solutions for wireless data transmission. In early 2004, 3Com announced a solution in the field of wireless mobility system wireless switches, which allows for forward planning, centralized management, automatic diagnostics of access points, detection and isolation of third-party meshed segments, access control she joined a group of koristuvachivs. Wireless Mobility System has high mobility, swedish roaming, as well as a high level of availability before transmission of traffic-critical traffic (VoIP, video) with various CoS and QoS mechanisms.
According to fahivtsiv estimates, before the end of streaming rock in the segment, the possession for LOM is close to 20% Wi-Fi-ownership. The main areas of zastosuvannya to the standard do not change; Significant growth will be seen in the sphere of office and home environments. The structure of Wi-Fi technology stagnation seems to be approximately the following rank: 10-15% of houses, 60-65% of office, 30-35% of hot-spots. With the development of new non-keratinous products, priority is given to safety, increasing the efficiency for coristuvacha in terms of improvement, etc., increasing throughput.
The solution to the problem of security in Wi-Fi meshes can really expand the number of wires and bring them up to the rootless meshes on a fundamentally new level. But this problem cannot be solved only for the help of adopting standards and for the unification of the possessions. Significant susillya in tsomu directly to report the postal workers of the service, the system of security is needed, the necessary adjustment of the access policy, the role played by the competent robot of the administrator of the dartless merezhі is great. In short, seeming, following all the necessary visits and winning all the possible help for the security of safety.
April 14 The Institute of Electrical and Electrical Engineers (IEEE) has finalized the final version of the WiFi 802.11n wireless standard. To say that the process of adopting the specification has been delayed is to say nothing: the addition to the first version of the front version of the standard could be bought more like the 2006 year, but the stench was not stable enough. The extensions were taken away by the extension, which would support the friend's forward version of the standard (draft 2.0), allowing more "childish ailments". At the sale, the stench is already close to two roki, and on the impersonal problems with the irritant sound of the shackles, the bells and whistles do not swear: they practice and practice. And why dosit shvidko that stable.
What is the new version of the beloved "wifi" best for the old? The maximum theoretical speed for the 802.11b standard is 11 Mb/s at a smog frequency of 2.4 GHz, for 802.11a - 54 Mb/s for 5 GHz, and for 802.11g - the same 54 Mb/s, but for 2.4 GHz. In 802.11n, the smuga frequency varies and can become like 2.4 GHz, or 5 GHz, and the border speed reaches the enemy 600 Mb/s. Zrozumilo, theoretically. In practice, 802.11n is considered to be "down to earth", but still hostile 150 Mb/s. It is also significant that the vibrations of both frequency bands reach the reverse summation of both 802.11a and 802.11b/g.
Polypshity shvidkіsnі pokazniki permitted kіlka tekhnologii. In the first place, MIMO (Multiple Input Multiple Output), the essence of which is in equipping the device with a number of transmitters, which work on the same frequency, that is the bottom of the data streams between them. In another way, retailers have developed a technology that allows you to select not one, but two frequency channels with a width of 20 MHz leather. When necessary, the stinks are either okremo, or at once, pouring into one wide 40-megahertz channel. In addition, in IEEE 802.11n, the OFDM modulation scheme (orthogonal frequency multiplexing) is installed - the number of times (specifically, the number of times the frequency is 52 per day, of which 48 are assigned without intermediary for data transmission, and 4 for pilot signals) data transmission over one space the stream can reach 65 Mb/s. A lot of such flows can be from one to several at the skin directly.
Significantly improved and the situation with zones of coverage and stability of reception. Do you remember the saying "One head is good, and two are better"? So from, here is the same principle: now transmitting a sprat, antennas, and therefore, and catching the measure all the same, the state will be more beautiful - move behind the zone of the access point, spread out on the land side, no longer visible for everything.
The situation in Russia
Autumn Science and Research Institute of Radio (NDIR) prepares standards for the installation of equipment for operation in Russia of the wireless standard 802.11n. At the same time, it is permissible to win only in the intranet-merezh, and after the adoption of the NPA yoga, it will be possible to win in the merezh of the infamous coristuvannya.
In the opinion of Dmitry Laryushin, director of the technical policy of Intel in Russia, approved by the IEEE institute, it plays an insanely positive role in the development of the implementation of regulatory rules in the Russian Federation, which opens the way for imports of this kind of possession 802.11n in our country. It should be noted that the 11n protocol in version D2.0 is supported by Intel's WiFi products starting in 2007, but, until the rules adopted by Russia for the import of that radio electronic equipment, option 11n was turned on. Starting from the advancing fate, for the mind of the positive decision of the DCRF and the promotion of NPA on this technology, the Russian market is supplied with Intel products with support for WiFi 11n in the remaining version of the standard.
Far from all the owners of the possession comply with the letter of the law: the deacons of the company have already long ago reached Russia's borders with the possession, as if they were supporting the 802.11n standard. It does not matter to vendors to sell laptops on the market with WiFi modules supporting 802.11n, as issued by "Intel"
Among the most common wireless technologies you can see: Wi-Fi, Wi-Max, Bluetooth, Wireless USB and a remarkable new technology - ZigBee, which has been gradually developed with a focus on industry.
Malyunok 1 - Standard of a dartless sling
The skin from these technologies has its own unique characteristics (divine figure 2), which determine the specific areas of application.
Let's try to formulate the best, as we may be satisfied with the technology of communication for a successful stop at the industry. It is acceptable, that there are some industrial objects that are composed of a number of pumping electric drives, an attachment for the collection of information from various technological sensors, for example, sensors in a vice, temperature, vitrati, including those installed remotely, an operator console and a control room paragraph. The pumps are controlled from the operator's console, and the dispatcher's office conducts uninterrupted monitoring of the system.

Figure 2 - Main characteristics of popular standards of a dartless linkage
Obviously, the best option, in terms of simplicity and clarity, would be to combine all the outbuildings, which take part in the exchange of information, into a single information measure, which works in one standard. Shards on the industrial object can be installed in the outbuildings of various foldability, vіdpovіdno, vartosі, then the software and hardware complex, which ensures the access of the skin outbuilding to the information system, can be done cheaply. Also, the technology of communication can ensure the necessary range and speed of the day. And if you call on those that the industrial installation can be supplemented with new units (for example, one more pump or we will add information collection), then the scalability is required for the technology of communication. Well, obviously, communication technology can provide security and security of information transmission. A look-alike view is a typical butt of a divided control system, de-coded from a node, being intelligent, it takes its own local automation task, and links between nodes are “weak” - basically, operational control commands are transmitted as change the settings of the regulation change, notification about became the owner of the technological process. A skin vuzol, for example, on the basis of a frequency conversion, can communicate with technological sensors, and the need to transmit large data streams daily.
Analysis of wireless technologies shows that high-end technologies Wi-Fi, Wi-Max, Bluetooth, Wireless USB are recognized in the first place for servicing computer peripherals and multimedia devices. The stench is optimized for the transmission of large communications on high speeds, it is mainly used for the “speck-speck” or “zirka” topology and is of little use for the implementation of foldable industrial framing with a large number of knots. Navpaki, ZigBee technology can show modest indications of data transfer speed and performance between nodes, but it can be so important, from the point of view of zastosuvannya in industry, advances.
1. It is focused on the importance of the choice in systems of separate multi-microprocessor control with the collection of information from intelligent sensors, de-energizing the minimization of energy and the initial processor resources.
2. It is possible to organize self-configuring networks with a folding topology, for which the route is automatically updated as the number of references turned on / off for a given moment of attachments (vuzlіv), and the number of connections between them is automatically displayed on the hardware level.
3. Ensure scaling - automatic introduction into the operation of the node or a group of nodes immediately after the supply of live to the node.
4. Guaranteeing a high reliability of the system for the calculation of the choice of an alternative transmission route;
5. Supporting hardware encryption mechanisms to support AES-128, including the possibility of unauthorized access to the security.
Organization of ZigBee networks
ZigBee is a prominent new standard for wireless communication, which has been growing on the cob as a way to transfer small amounts of information to small stations with minimal power consumption. In fact, this standard defines the rules of the robotic software and hardware complex, which implements the root-free interaction of attachments one by one.
The ZigBee protocol stack is a hierarchical model inspired by the principle of the seven-layer model of transmission protocols in open system OSI (Open System Interconnection) systems. The stack includes equal to the IEEE 802.15.4 standard, which is responsible for the implementation of the communication channel, and software networks equal and equal to the add-on support, determined by the ZigBee specification . The implementation model for the ZigBee communication standard is represented by little 3.

Figure 3 - Bagator_vneva model to the ZigBee link standard
The IEEE 802.15.4 standard defines two lower layers of the stack: the Media Access Layer (MAC) and the Physical Layer of Data Transfer in the Middle (PHY), then the lower layers of the Wireless Data Transfer Protocol . The Alliance defines the software levels of the ZigBee stack from Data Link Control to ZigBee Profiles. The reception and transmission of data by a radio channel is based on the physical PHY level, which indicates the operating frequency range, modulation type, maximum speed, number of channels (Table 1). The PHY level controls the activation-deactivation of the receiver, the detection of the energy of the signal that is received on the working channel, the choice of the physical frequency channel, the indication of the strength of the call when the data packet is removed, and the evaluation of the free channel. It is important to understand that the 802.15.4 standard is a physical radio (radio receiver chip), and ZigBee is a logical software stack that provides security and routing functions.
Daly in the ZigBee stack structure follows the level of access control to the IEEE 802.15.4 MAC medium, which controls entry and exit from the array of outbuildings, the organization of the array, the formation of data packets, the implementation of various security modes (including 128-b final encryption AES), 16- and 64 - bit addressing.
MAC Riven provides different access mechanisms in the tier, support of tiered topologies from point-to-point to rich tier, data exchange guarantees (ACK, CRC), streaming and packet data transmission.
In order to protect against negligent interactions, it is possible to use a time interval based on the CSMA-CA protocol (multiple access protocol to the medium with control of the carrier and the prevention of collisions).
ZigBee’s timing subdivision is based on a different synchronization mode, with some sort of subordering of the external attachments, they spend most of the hour at the “sleeping” station, periodically “rolling over” for the received synchronization signal as a trimming coordinator, which allows the extensions to use a single local border between the nobility, at some point in time stop the transmission of data. Danish mechanism, the foundations on the channel assigned to the link before the cob of transmission, allow to speed up (albeit not lose) the closure, caused by the transfer of data to the kilkom by the outbuildings. The 802.15.4 standard is based on duplex data transmission (it can either transmit or receive data), which does not allow the CSMA-CA method to be used to detect the col- lisions of the data.
The stack specification has three types of attachments transferred: coordinator, router, and end attachment. Coordinator initialization of the link between the nodes, collecting information about the skin node setting, setting the frequency channel number and the PAN ID link, and in the process of the work, you can use the dzherelom, we will receive the alarm by the repeater. router for the choice of the route of delivery of notifications, which are transmitted as soon as possible from one node to the next, and in the process of work, you can use the dzherelom, we will accept or relay the notification. While routers may be able to be more flexible, they can designate optimized routes to the destination point and save them for further guessing in the routing tables. Kіntsevy pristry I do not take part in the management of the network and the retransmission of support, being only a dzherel / receiver of support.
Among the authorities of ZigBee, we have seen a foldable topology measure. For the same reason, with a visible small maximum range of a link between two adjoining outbuildings, you can expand the coverage area of the fence as a whole. Also, 16-bit addressing is used, which allows you to combine one measure over 65 yew. outbuildings

Figure 4 – ZigBee Meret Topologies
The IEEE (Institute of Electrical and Electronic Engineers) organization is developing WiFi 802.11 standards
IEEE 802.11 is the basic standard for Wi-Fi networks, which defines a set of protocols for the lowest data transfer rates.
IEEE 802.11b- describe b about
more speed of transmission and introduction of more technological facilities. This standard is widely protruding from the side of WECA ( Wireless Ethernet Compatibility Alliance ) and back to back called WiFi .
Whirlwind frequency channels in the 2.4GHz spectrum ().
Ratified in 1999 roci.
Wikoristan radio frequency technology: DSSS.
Coding: Barker 11 and CCK.
Modulations: DBPSK and DQPSK,
Maximum speed of data transmission (transfer) per channel: 1, 2, 5.5, 11 Mbps,
IEEE 802.11a- Describe significantly the security of the transfer (transfer) below 802.11b.
The frequency channels are selected for the 5GHz frequency spectrum. ProtocolIrresistible from 802.11 b.
Ratified in 1999 roci.
Vikoristovuvan radio frequency technology: OFDM.
Coding: Convoltion Coding.
Modulations: BPSK, QPSK, 16-QAM, 64-QAM.
Maximum transmission speed per channel: 6, 9, 12, 18, 24, 36, 48, 54 Mbps.
IEEE 802.11g
- Describe the security of data transfers equivalent to 802.11a.
Frequency channels are selected in the 2.4GHz band. Protocol summ_s іz 802.11b.
Ratified in 2003 roci.
Vykoristovuvani radiofrequency technologies: DSSS and OFDM.
Coding: Barker 11 and CCK.
Modulations: DBPSK and DQPSK,
Maximum speed of data transmission (transfer) per channel:
- 1, 2, 5.5, 11 Mbps on DSSS and
- 6, 9, 12, 18, 24, 36, 48, 54 Mbps on OFDM.
IEEE
802.11n- The most advanced commercial WiFi standard, at the moment, is officially allowed before importation and stasis in the territory of the Russian Federation (802.11ac is still in the process of operation by the regulator). 802.11n has different frequency channels in the WiFi 2.4GHz and 5GHz frequency spectra. Sumy s 11b/11 a /11g . If you want to be recommended to be more oriented with less than 802.11n, because you will need to configure special protection modes if necessary, with the necessary totality against old standards. Leading to a great increase in signal informationa significant reduction in the available core productivity of the radio interface. Vlasne navit one client WiFi 802.11g or 802.11b due to the special adjustment of all measures and mittvoї її suttєvoї degradation schodo aggregated productivity.
The WiFi 802.11n standard itself was released on May 11, 2009.
WiFi channels are trimmed with a width of 20MHz and 40MHz (2x20MHz).
Vikoristovuvan radio frequency technology: OFDM.
OFDM MIMO (Multiple Input Multiple Output) technology is victorious right up to 4x4 (4x Transmission and 4x Receiver). With a minimum of 2xTransmitter per access point and 1xtransmitter per attachment.
Apply the possible MCS (Modulation & Coding Scheme) for 802.11n, as well as the maximum theoretical transfer speed in the radio channel presented in the following table:
Here SGI - tse zahisnі intervals between frames.
Spatial Streams are the number of spacious streams.
Type is the type of modulation.
Data Rate is the maximum theoretical speed of transmission in the radio channel in Mbps.
Important, that the values of the speed correspond to the understanding of the channel rate and є the boundary values of the given set of technologies within the framework of the described standard (it is clear that the values, as you have been noted, are written on the boxes of home WiFi-appliances in stores). But in real life, the value is not achieved through the specifics of the technology itself, the WiFi 802.11 standard. For example, there is a strong "political correctness" in part of the CSMA / CA security (WiFi devices permanently listen to the air and cannot transmit, as the medium of transmission is occupied), the need to confirm the skin unicast frame, the duplex nature of all WiFi standards and 802.11ac/Wave-2 only you can do it more often, etc.. Therefore, the efficiency of the old standards 802.11 b / g / a does not exceed 50% in ideal minds (for example, for 802.11g, the maximum bandwidth per subscriber is no more than 22 Mb / s), but for 80 2.11n efficiency can be up to 60%. If the fence works in a protected mode, which often passes through the difference in the presence of different WiFi-chips on different outbuildings in the fence, then the indicated visibility efficiency can fall 2-3 times. Cost, for example, a mix of Wi-Fi add-ons with 802.11b chips, 802.11g at least with WiFi 802.11g access points, or add WiFi 802.11g / 802.11b at least with WiFi 802.11n access points. .
Crimium of the main standards WiFi 802.11a, b, g, n, are based on and developed additional standards for the implementation of various service functions:
. 802.11d. For adapting various outbuildings to the WiFi standard to the specific minds of the country. In the middle of the regulatory field of the skin state, the range often differs and can be similarly influenced by the fallow geographical position. The IEEE 802.11d WiFi standard allows the regulation of several frequencies in the attachments of various devices for additional special options introduced in the protocol by access to the transmission medium.
. 802.11e. Describes the QoS quality class for transferring various media files and in general various media content. MAC-level adaptation for 802.11e determines the brightness, for example, of one-hour audio and image transmission.
. 802.11f. Directions for the unification of parameters to access points to the Wi-Fi standard of various types. The standard allows for short distances to practice with different measures for an hour of movement between zones of different measures.
. 802.11h. Vikoristovuetsya for zabіgannya sdstvenniyu problems meteorological and Russian radars with a way of dynamic reduction in the intensity of Wi-Fi possession or a dynamic transition to a lower frequency channel when a trigger signal is detected (in most European countries on the ground no stations following meteorological satellites and satellites for communication, as well as radars of the Viysk on y bands close to 5 MHz). This standard is required by ETSI until it is approved for operation in the territory of the European Union.
. 802.11i. The first versions of the WiFi 802.11 standards for Wi-Fi security have adopted the WEP algorithm. It has been suggested that this method can secure the confidentiality and protection of the transmission of data of authorized coristuvachs without dart wires in the form of eavesdropping. Now, this Zakhist can be less evil for a sprat of khvilin. Therefore, in the 802.11i standard, new methods were developed for Wi-Fi protection, implemented both on the physical and software levels. To organize a security system in Wi-Fi 802.11 networks, it is recommended to use Wi-Fi Protected Access (WPA) algorithms. The stench also secures the summіsnіst mіzh wіth dart-free outbuildings of different standards and different modifications. The WPA protocols have improved the RC4 encryption scheme and the method of binding authentication with the EAP wiki. The stability and security of current Wi-Fi networks is determined by protocols for checking confidentiality and data encryption (RSNA, TKIP, CCMP, AES). The most recommended approach is to use WPA2 over AES encryption (and don't forget about 802.1x overhead, for example, tunneling mechanisms, for example EAP-TLS, TTLS too). .
. 802.11k. This standard is actually directly related to the implementation of the balancing of the interference in the Wi-Fi radio network. Ring at the wireless local network of the subscriber's attachment, ring with the access point, so as to secure the strongest signal. It is not uncommon to bring up the revantation of a network in one point, if one access point is connected to a very rich network. To control such situations, the 802.11k standard has introduced a mechanism that separates the number of subscribers, that connects to one access point, and gives the ability to mix minds, for which new ones will be connected to another ї Navit AP not surprised by a larger weak signal in front of it. In this way, the bandwidth of the building of the city is aggregated, and the efficiency of the use of resources increases.
. 802.11m. Amendments and amendments for all groups of 802.11 standards are combined in a separate document called 802.11m. First release 802.11m from 2007, dated from 2011 and etc.
. 802.11p. Depending on the Wi-Fi-ownership, which collapses with a speed of up to 200 km / year, it depends on a non-violent WiFi access point, the distance to a distance is up to 1 km. Part of the Wireless Access in Vehicular Environment (WAVE) standard. The WAVE standards designate an architecture and an additional set of service functions and interfaces that provide a safe mechanism for radio communication between transport barriers that are collapsing. These standards are developed for such programs, as, for example, the organization of road traffic, control of security traffic, automation of the selection of payments, navigation and routing of transport services and other.
. 802.11s. The standard for the implementation of external measures (), whether any attachment can serve as a router, or as an access point. If the nearest access point is overwhelmed, it will be redirected to the nearest unvanquished node. In this case, the data packet is transferred (packet transfer) from one node to another, until the end of the recognition month is reached. In this standard, new protocols have been introduced on the MAC and PHY levels, which support wide-range and multi-address transmission (transfer), as well as unicast delivery over the Wi-Fi access point system, which is self-configuring. For this reason, in the standard, a choice of address formats for the frame has been provided. Apply WiFi Mesh implementations: .
. 802.11t. Creation standard for institutional testing solution to the IEEE 802.11 standard. The methods of testing are described, the ways of vimiryuvannya and processing of results (treatment), and help to the testing possession.
. 802.11u. Describes the procedures for interfacing with the Wi-Fi standard from outside the borders. The standard is responsible for assigning protocols and access, protocols, and priority to the fence on the work from outside the borders. At the moment, a great break has been established to the standard, as in part of the development of the solution - Hotspot 2.0, and in the organization of intermediary roaming - a growing group of roaming operators has been created, yak Wi-Fi-merezh in dialozi (Alliance WBA) . Read more about Hotspot 2.0 in our articles: , .
. 802.11v. The standard may have some amendments, directing to the full systems of keruvannya merezh standard IEEE 802.11. Modernization on the MAS PHY-levels is due to allow the centralization and ordering of the configuration of client extensions, connected from the network.
. 802.11y. Dodatkovy standard linking to the frequency range of 3.65-3.70 GHz. Appointments for the outbuildings of the remaining generation, which are used with modern antennas at speeds up to 54 Mbit / s at a distance of up to 5 km at a wide open space. The standard is not yet complete.
802.11w. It signifies the method of the procedure for improving the protection and security of the level of care by access to the medium of data transmission (MAS). The protocol and standard structure a system for monitoring the integrity of data, the accuracy of the data dzherel, the fence of unauthorized copying and copying, the confidentiality of data and other protection. The standard introduces a frame management protection (MFP: Management Frame Protection), and additional security features allow you to neutralize malicious attacks, such as DoS. Trochs more MFP here:,. In addition, go to security for the most intelligible mesh information, as it is transmitted by meshes with support IEEE 802.11r, k, y.
802.11ac.
The new WiFi standard, which works only in the 5GHz frequency band and provides much more security about
more security both on an individual WiFi client and on a WiFi access point. See our stats for more details.
The resource is constantly popovnyuєє! To stop announcements when new thematic articles appear, or when new materials appear on the site, it is necessary to subscribe.
Come join our group for