The process of upgrading the operating system begins with. Inspiration for the operating system. Initializing the system using the BIOS
When the computer is turned on, the processing is transferred to the basic input/output system, the BIOS. It finally verifies the computer's hardware nodes, forms the first part of the vector table, initializes the device, and begins the installation process. operating system.
The problem begins with the BIOS trying to read the first sector of the floppy disk inserted into drive A: (on a new floppy disk, this sector is the same as the operating system). If a system floppy disk is inserted into the drive, it is considered to be a copy of the diskette and the diskette is transferred to it.
If the floppy disk is a system one, then. Do not delete the necessary recording; a notification about the steps to replace the floppy disk appears on the screen.
If there are no floppy disks in drive A:, the BIOS reads the master boot record of drive C: (Master Boot Record). Select the first sector on the disk. The kerubanya is transferred to the vantageur who is in this sector. The owner analyzes the partition table (which is also located in this sector), selects the active partition and reads the owner's entry for that partition. The backup record of the active partition (Boot Record) is similar to the backup record that is located in the first sector of the system floppy disk.
The final record of the active partition reads the IO.SYS and MSDOS.SYS files from the disk (in that order). Then resident drivers are read and enlisted. Formation of the associated list of device drivers begins. It is analyzed in conjunction with the CONFIG.SYS file, and the drivers described in this file are included. Initially, drivers described by the DEVICE parameter will be used, then (only in MS-DOS versions 4.x and 5.0) resident programs specified by INSTALL statements. After this, the command processor is read and control is transferred.
The command processor consists of three parts - resident, initialized and transit. The resident part is attracted to the first one. Vaughn collects the alteration of INT 22H, INT 23H, INT 24H, which is important for the transit part. This part of the command processor collects MS-DOS bugs and asks the user to do things to detect bugs.
The initialization part is only removed during the installation of the operating system. This indicates the primary address behind which the client program is located and initiates the entry to the AUTOEXEC.BAT file.
The transit part of the command processor is located at the highest memory addresses. This part contains extractors of internal MS-DOS commands and an interpreter of command files with the extended name.BAT. The transit part is a system request (for example, A:), which receives the entry of an operator command from the keyboard or from a batch file and organizes their execution.
After installing the command processor and completing the initial procedures stored in the AUTOEXEC.BAT file, the preparation of the system for operation is completed.
1.3. Zagalna robot dos scheme
In order to correctly deal with system software and hardware, it is necessary to clearly understand the mechanism of interaction between application programs and the computer. In Fig. 1.1 shows the functional connections of programs from the software and hardware of the IBM PC.
Fig.1. Functional connections between programs for MS-DOS and hardware and software PEOM
Typically, the DOS kernel is divided into a number of subsystems, each of which is responsible for completing these and other tasks. As the baby is shown, the following subsystems are visible:
file system;
keruvannya pam'yattyu system;
keruvannya program system;
system linking with device drivers;
system for processing pardons;
service to the hour;
operator console entry/display system.
These subsystems communicate with the equipment through the BIOS, drivers, and in between. Application software can access DOS subsystems, work with BIOS, or directly with hardware. Please note that application programs can only access drivers through the DOS subsystem.
Obviously, the greater the importance of the interface of application programs and hardware, the less the program depends on the features of the hardware.
Let's take a closer look at the DOS subsystem.
Have you ever wondered what comes with the operating system at that moment when it paints its logo and says “Starting Windows”? And I was infatuated, why is she so infatuated for so long? Even at the start of the system, there are definitely no problems that arise from the calculation point of view!
What then is important to the importance of the operating system? Much attention is paid to the solution of concatenated modules and the initialization of service data structures. The structures of these data live in memory, so operations with them may be fluid. It all comes down to the idea of those who are constantly involved in the process of attracting the mounted modules to the riddle.
Let's figure out what modules, in what quantity and in what order are installed when the OS starts. To be clear, you can, for example, remove the log of the system. My current OS is Windows 7 Enterprise x64. Log the process of downloading the additional kernel manager. There are many options for kernel managers, and I particularly prefer WinDbg. We also need a number of additional tools for the charming transformation of the light into a more acceptable way for the eye.
Mining and crafting
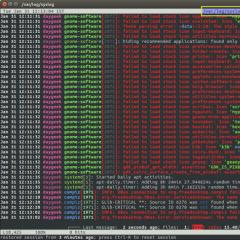
It’s good to google it, but I won’t describe this process in detail. So that we can collect everything that is expected from the moment the system starts, we need to select the Cycle Initial Break item, which will allow the controller to stop, as only in the system that is being developed, the kernel development subsystem will be involved. The file can be duplicated using the additional commands ".logopen" and ".logclose", which is simple. The other command is ".cls". Vaughn clears the command screen, and thus removes the command screen.The function for us is “MiCreateImageFileMap”. This is an internal function of the memory manager that projects the file that is saved into memory. Projection into memory is created when a section is created, for example, when starting a file that is being saved. However, keep in mind that the file that is being compiled and projected into memory is not a guarantee that your code will be compiled! This function simply creates a projection, most often in reserve, so that if you decide to launch the module on Wikonanny, you can protect the hour of your interest. We will put a logging point on this function.
If you have enough money, enter the following command:
bu nt!MiCreateImageFileMap "dt nt!_EPROCESS -d ImageFileName @$proc; dt nt!_FILE_OBJECT -d FileName @rcx; g"
The magic row literally means on the offensive:
- bu (Set Unresolved Breakpoint) - set an unresolved breakpoint. Not those that are not permitted, but for its installation it is necessary to indicate which address you are putting it at. On the right is that it is not known from behind what address you may be looking for. When any module is selected, the presence of a new necessary function is checked, and if such a function is found, the stop point is set automatically. This installation method is indispensable when ASLR is enabled - randomization of the address space, module fragments will be assigned to different addresses, and the anchor point, installed behind a fixed address, will most likely appear not on the right.
- nt!MiCreateImageFileMap is a symbol that needs to be taken into account. WinDbg has accepted the entry for the form "module_name!function_name". In this case, nt is the nickname for ntoskrnl.exe.
- The following is a part of the WinDbg script that will be completed immediately when this function is introduced. "dt nt!_EPROCESS -d ImageFileName @$proc" in Russian means "display the ImageFileName field of the _EPROCESS structure from the nt module at the same time as the address designated in the "threaded process" pseudo-registry." Comes after the separator ";" The command means approximately the same, only the structure addresses are taken from the rcx register, to which the first function parameter is passed in the Microsoft x64 ABI. "g" means "go" then. continue to live as a viconn.
A small recommendation for vikoristaniya logical points of the command: try not to vikoristovat extension of the controller (commands that begin with "!"), since in this case the login will end up much more.
Let's go! We squeeze the pin point and check it. I checked the docks and wandered around the work table, then. I'm logged in. After removing the “harvest”, the bits are edited, all crops are trimmed for ease of further processing and are harvested for the python. Please don’t bother me about parsing the log. It is also significant that the graph fits into the shape of the Archimedes spiral with further manual correction, since the nodes were superimposed one on one. In the selected column, the procedure for acquiring libraries is covered. It’s a pity that I had to donate to the doctor’s order for the collection of files to be saved in order to save the library for the ease of reading the graph.
Dawn sky map

Intellectually there is a small group of attraction.
The OS starts from the ntoskrnl.exe module, which is the OS kernel. And even more specifically, with the KiSystemStartup() function. Together with the required system components, it forms the foundation of the OS: a subsection of robot modes, basic services for customer add-ons, etc. This group includes drivers intended for installation at the time of system startup. In a nutshell, this turtle will be born with Windows OS.

Nastupnyi Vuzol – session manager. This represents the first system process that starts in Windows – smss.exe. The process is notable because it is a native Windows process, so it does not rely on the Win32 subsystem, which is not yet installed. This process uses the native services of the operating system with the help of ntdll.dll, which is the interface to the server mode for OS services. This process is also a trusted component of the operating system and is subject to security rights, for example, it can create security tokens. Another main purpose is the creation of sessions and the initialization of subsystems, both graphical and various types (Windows, POSIX). This turtle supplies everyone with their needs.

The logon group consists of several processes. The stink indicates the initialization of sessions. This includes displaying the mobile screen, creating desktops, launching auto-login processes and initializing the security subsystem, etc. This broom throws out all outsiders.

The most pressing was the group of services. That's a lot of what she does with the SuperFetch service. That's the same thing, as I can say, that at the end of the weekend she's going to use the office package, and at the beginning of her work day - Steam with games. Superfetch promotes a large number of modules at system startup, so that then everything works smoothly. In addition, the system contains service add-ons and drivers that start automatically. I think everyone was upgrading the “Services and Programs” equipment. The whole point of life is to provide the system with everything that is needed and no longer needed.

The last thing I love is explorer.exe. It is noteworthy that before the moment of its launch, all modules that are being tested are already stored in memory. The screenshot also shows that vcredist_x64.exe is missing, lying on the desktop under the virtual machine and asking the explorer to solve the riddle.

There are a lot of ways to get involved in the riddle of the module. For example, it is enough to supply information from resources to a file, including its icon. The application explorer itself has verified that this program will require increased privileges, then. Let's paint it up to the icon of the top baby with a yellow-bladed shield. Let me emphasize once again that focusing on a module for a riddle does not mean violating its code!
I especially rub the picture sideways. It’s good to quilt the deposits, for example, drivers. Also, when paired with the Sysinternals Autoruns utility, you can determine at which stage of installation these and other modules are pulled.
Graph of demand acquisition for Windows 7 Enterprise x64 installed on a VMware virtual machine. Below is a vector image of the graph and a file in gml format, which you can use in any graph editor.
It’s a frustrating time to run from one operating system to another, which is installed on two computers, without leaving. After diligently choosing both, it’s too early to choose one of them - basically It is important to carry out work with a robot. Since there is more than one Windows system, other versions or editions are located on different disk partitions, It’s not obvious to say. Of course, obviously, the space of a hard drive is not limited by dimensions.
The ability to work in the future with other computer systems can be deprived, but for the sake of convenience, you can simply log in, avoiding the delay. In this case, starting the computer will be simplified by automatically installing the required operating system. Another option to get started with your computer is to not select the settings for all systems, but to consider the required version of Windows as selected and change the time for selecting other options in the selection window. vaca.
How to edit the process of installing multiple Windows operating systems installed on one computer is described in more detail below.
Also, you may have a computer with installed versions of Windows 7 and 8.1. Once your computer is installed, you will be able to choose from a variety of systems.
Right now, when you need a computer, you can use the system you need by making a confirmation selection. At any other time after the singing hour - and after the end of the day 30 seconds– will be automatically enchanted by Windows, come first on the list. Our vipadka has this Windows 7 The fragments of it are installed on the remaining computer, and they themselves are important, as it is important to us after starting the computer.
Well, that’s changeable. The system is automatically set up - Windows 8.1. For which, naturally, it is necessary to go to her.
We need a separate adjustment section, and Windows 8.1 can now be used using the additional context menu on the button.

At the end of the system, select Additional parameters.

You can also set up a partition in Windows 7 using the context menu by clicking on the icon "Computer" at the conductor. Among the commands you need to select.

In Windows 7 you can also select Additional parameters.

Further details of both systems are identical.
At the office of the authorities of the system, what appeared at the deposit "Dodatkovo" We will emboss the parameters button in the remaining section.

It is now possible to edit the configuration of several systems. I am very interested in installing Windows from the number of options in the list that appears. Our version has Windows 7 installed, which can be changed to Windows 8.1.

As I thought, Windows is checking for your clothes pvhvilini You can then select your operating system.

It is important that the work is carried out only in one system, there is no sense in depriving the sense of self-awareness and automatic attraction. Another operating system may not be able to start up, but the speed of installation will allow you to select options. The following list of systems that you are interested in will be installed in our selection. 5 seconds Wake up before the automatic installation of Windows 8.1. What time should you spend too much time to make a choice, just in case you need to upgrade to Windows 7.

To revert to using another system from the transfer of data, you need to check the option Display of the list of systems. In this case, without any time-consuming steps, there is no system for getting things done.

If you need another operating system, you can go to it by enabling this option I'm back active.
After making changes, it will be embossed "OK" at the bottom of this window, and also at the bottom of the window of the authorities of the system.

All – the list of favorite operating systems has been edited.
We looked more closely at the editing of existing operating systems. Also, when you start your computer, you can often see a list of operating systems that are already on the computer neither. This natural development is possible after the other operating system was introduced by the way of initially formatting the disk partition or reducing system files manually, otherwise The record about the capability of this feature was not collected from the system configuration. You can also choose the option to start the main Windows after the system has been reinstalled. This, by the way, is not the main thing, but one of the reasons why system engineers want to do a so-called clean installation of Windows without saving the files of the previous system and formatting the disk partition.
It is better to remove the unnecessary operating system from the installation options, so that it does not delay the process of starting the main Windows.
In the main system, click the command. Windows 8.1 has easy access to its implementations from the context menu on the button.

We need system configuration section. Enter the following values in the command field:
Tisnemo "OK".

In Windows 7, you can launch the system configuration window in a simpler way - by entering a key entry in the search menu field.

The system configuration window will appear, go to the tab. We select the entry about the attachment of the unknown system and delete it.

In our opinion, there is an overflow of interest in different versions of Windows, and is indicated by the deleted "Simka" We obviously didn't have a hard time. Also, it is important to note that there are records about two new versions of Windows, in view of the fact that it is necessary to delete the system descriptions. Windows, in which we are aware of the fact, will be designated as continuous.
Changes made can be saved using the button. After pressure "OK" the system registers re-enchant.

After restarting the computer, you can prevent the system from auto-locking.
After the computer is powered down, there is no operating system in its RAM. By itself, without an operating system, the computer’s hardware cannot handle operations such as storing programs in memory. In this way, we are faced with a paradox that seems inextricable: in order to entice the operating system to solve the riddle, we are already responsible for the operating system’s memory.
The solution to this paradox is the use of a special small computer program called cob zavantazhuvachem, or the commands are located in non-volatile memory (for example, on the IBM PC - restart commands without any help). This software can detect devices that are suitable for anti-aging, and anti-aging in a special section of the selected device (usually the anti-aging sector) of these devices in the operating system.
Pochatkov's vanguards may indicate specific conditions, especially obedience. For example, on an IBM PC Vantazhuvach of the First Rivnya is guilty of being located in the first 446 bytes of the head locking record, which leaves room for the 64 byte partition table and 2 bytes for the AA55 signature, which is necessary for the BIOS to detect the head lock.
History
The first computers had a small set of remixers that allowed the operator to place the initial memory in the memory before starting the processor. Then you need to read the operating system from an external device, for example, from a punched paper or from a hard drive.
The pseudo-assembly code of the cob developer can be easily forgiven, since there is a sequence of instructions:
0: write the number 8 to the P register 1: check that the device can start reading from the punched strip 2: if you can’t, go to step 1 3: read the byte from the device and write it to the battery 4: when the punched stitch has run out , go to step 8 5: write the values that are saved in the battery into the RAM behind the address that are saved in register P 6: increase the value of register P by one 7: go to step 1
This butt of the base is based on one of the minicomputers released in the 1970s by Nicolet Instrument Corporation.
0: write the number 106 to the P register 1: check that the device can start reading from the punched strip 2: if you can’t, go to step 1 3: read the byte from the device and write it to the battery ulator 4: the punched stitch has run out , go to step 8 5: write the value that is saved in the battery into the RAM behind the address that is saved in register P 6: change the value of register P to one 7: go to step 1
The duration of the acquisition of another level was such that the remaining byte of the acquisition of the command changed to address 6. In this way, after completing point 5, the acquisition of another level started. Another level of refilling of the devices will read the punched stitches with a full number of punched stitches to suit the operating system. The difference between the vantage of the first level and the vantage of the other level was the re-verification of the readings from the punched pages, which were often recorded at that time, and, at the same time, on ASR-33 teletypes, which are being used in the future nomu vipadku.
These operating systems, most characteristic of the older (pre-1995) operating systems of Apple Computers, are closely linked to the hardware of the computers, which is impossible to install on these computers live like the operating system. In these types of cases, the cob attachment begins to break down, which works as an extension of the standard OS, and then transfers it to the alternative operating system. Apple used this method to run the A/UX version of Unix, and then used it for a variety of other no-cost operating systems.
Devices that are initialized by BIOS
A powerful device is a device that may be installed before the operating system is installed. These include the input devices (keyboard, mouse), the basic output device (display), and the device that will be used - disk drive, hard drive, flash drive, PXE).
The consistency of a standard IBM-size personal computer is preserved
Obsessed with a personal computer
Posilannya
Wikimedia Foundation. 2010.
Look at the “Infatuation of the operating system” in other dictionaries:
Operating system backup is a system security program that ensures the backup of the operating system immediately after turning on the computer. Protect the operating system: provide the necessary features for dialogue with... Wikipedia
This term has other meanings, div. Core. The kernel is the central part of the operating system (OS), which provides coordination components with access to computer resources, such as processor time, memory and external hardware... Wikipedia
For the term “planuvalnik zavdan” div. Other meanings. Task planning is one of the key concepts in task richness and rich processing power, both in operating systems for external purposes and in operating systems for real ... Wikipedia
This is a form of distribution of system software security. The popularity of distributions is due to the fact that the form of software that is used for its expansion may not be comparable to the form of software that operates ... Wikipedia
The protected function of a personal computer is entrusted to prevent unauthorized launch of the client, the protection of the operating system (OS) and the ability to access confidential information. Security... ... Wikipedia
This article must be posted. Please, please format it correctly according to the rules for formatting articles.
Windows XP starts in the Internet phone machine. In the information, basic knowledge refers to the complex and time-consuming process of starting a computer. The sequence of actions that can be used to sign up a computer for ... Wikipedia is important.
The availability of terminal clients can safely take over the operating system. The main solutions for secure storage are checking the integrity and authenticity of operating system files that can be stored on a local hard drive, ... ... Wikipedia
The main one is the duplicate ROM chips of the Gigabyte motherboard, which replaces the BIOS of the AWARD company. BIOS (English: basic input/output system “Basic ... Wikipedia
Prefetcher is a component of the Microsoft Windows operating system that speeds up the process of downloading and also speeds up the launch time of programs. Prefetcher first appeared in the Windows XP operating system. Starting with Windows Vista,... Wikipedia
Have you ever wondered what comes with the operating system at that moment when it paints its logo and says “Starting Windows”? And I was infatuated, why is she so infatuated for so long? Even at the start of the system, there are definitely no problems that arise from the calculation point of view!
What then is important to the importance of the operating system? Much attention is paid to the solution of concatenated modules and the initialization of service data structures. The structures of these data live in memory, so operations with them may be fluid. It all comes down to the idea of those who are constantly involved in the process of attracting the mounted modules to the riddle.
Let's figure out what modules, in what quantity and in what order are installed when the OS starts. To be clear, you can, for example, remove the log of the system. My current OS is Windows 7 Enterprise x64. Log the process of downloading the additional kernel manager. There are many options for kernel managers, and I particularly prefer WinDbg. We also need a number of additional tools for the charming transformation of the light into a more acceptable way for the eye.
Mining and crafting
It’s good to google it, but I won’t describe this process in detail. So that we can collect everything that is expected from the moment the system starts, we need to select the Cycle Initial Break item, which will allow the controller to stop, as only in the system that is being developed, the kernel development subsystem will be involved. The file can be duplicated using the additional commands ".logopen" and ".logclose", which is simple. The other command is ".cls". Vaughn clears the command screen, and thus removes the command screen.The function for us is “MiCreateImageFileMap”. This is an internal function of the memory manager that projects the file that is saved into memory. Projection into memory is created when a section is created, for example, when starting a file that is being saved. However, keep in mind that the file that is being compiled and projected into memory is not a guarantee that your code will be compiled! This function simply creates a projection, most often in reserve, so that if you decide to launch the module on Wikonanny, you can protect the hour of your interest. We will put a logging point on this function.
If you have enough money, enter the following command:
bu nt!MiCreateImageFileMap "dt nt!_EPROCESS -d ImageFileName @$proc; dt nt!_FILE_OBJECT -d FileName @rcx; g"
The magic row literally means on the offensive:
- bu (Set Unresolved Breakpoint) - set an unresolved breakpoint. Not those that are not permitted, but for its installation it is necessary to indicate which address you are putting it at. On the right is that it is not known from behind what address you may be looking for. When any module is selected, the presence of a new necessary function is checked, and if such a function is found, the stop point is set automatically. This installation method is indispensable when ASLR is enabled - randomization of the address space, module fragments will be assigned to different addresses, and the anchor point, installed behind a fixed address, will most likely appear not on the right.
- nt!MiCreateImageFileMap is a symbol that needs to be taken into account. WinDbg has accepted the entry for the form "module_name!function_name". In this case, nt is the nickname for ntoskrnl.exe.
- The following is a part of the WinDbg script that will be completed immediately when this function is introduced. "dt nt!_EPROCESS -d ImageFileName @$proc" in Russian means "display the ImageFileName field of the _EPROCESS structure from the nt module at the same time as the address designated in the "threaded process" pseudo-registry." Comes after the separator ";" The command means approximately the same, only the structure addresses are taken from the rcx register, to which the first function parameter is passed in the Microsoft x64 ABI. "g" means "go" then. continue to live as a viconn.
A small recommendation for vikoristaniya logical points of the command: try not to vikoristovat extension of the controller (commands that begin with "!"), since in this case the login will end up much more.
Let's go! We squeeze the pin point and check it. I checked the docks and wandered around the work table, then. I'm logged in. After removing the “harvest”, the bits are edited, all crops are trimmed for ease of further processing and are harvested for the python. Please don’t bother me about parsing the log. It is also significant that the graph fits into the shape of the Archimedes spiral with further manual correction, since the nodes were superimposed one on one. In the selected column, the procedure for acquiring libraries is covered. It’s a pity that I had to donate to the doctor’s order for the collection of files to be saved in order to save the library for the ease of reading the graph.
Dawn sky map

Intellectually there is a small group of attraction.
The OS starts from the ntoskrnl.exe module, which is the OS kernel. And even more specifically, with the KiSystemStartup() function. Together with the required system components, it forms the foundation of the OS: a subsection of robot modes, basic services for customer add-ons, etc. This group includes drivers intended for installation at the time of system startup. In a nutshell, this turtle will be born with Windows OS.

Nastupnyi Vuzol – session manager. This represents the first system process that starts in Windows – smss.exe. The process is notable because it is a native Windows process, so it does not rely on the Win32 subsystem, which is not yet installed. This process uses the native services of the operating system with the help of ntdll.dll, which is the interface to the server mode for OS services. This process is also a trusted component of the operating system and is subject to security rights, for example, it can create security tokens. Another main purpose is the creation of sessions and the initialization of subsystems, both graphical and various types (Windows, POSIX). This turtle supplies everyone with their needs.

The logon group consists of several processes. The stink indicates the initialization of sessions. This includes displaying the mobile screen, creating desktops, launching auto-login processes and initializing the security subsystem, etc. This broom throws out all outsiders.

The most pressing was the group of services. That's a lot of what she does with the SuperFetch service. That's the same thing, as I can say, that at the end of the weekend she's going to use the office package, and at the beginning of her work day - Steam with games. Superfetch promotes a large number of modules at system startup, so that then everything works smoothly. In addition, the system contains service add-ons and drivers that start automatically. I think everyone was upgrading the “Services and Programs” equipment. The whole point of life is to provide the system with everything that is needed and no longer needed.

The last thing I love is explorer.exe. It is noteworthy that before the moment of its launch, all modules that are being tested are already stored in memory. The screenshot also shows that vcredist_x64.exe is missing, lying on the desktop under the virtual machine and asking the explorer to solve the riddle.

There are a lot of ways to get involved in the riddle of the module. For example, it is enough to supply information from resources to a file, including its icon. The application explorer itself has verified that this program will require increased privileges, then. Let's paint it up to the icon of the top baby with a yellow-bladed shield. Let me emphasize once again that focusing on a module for a riddle does not mean violating its code!
I especially rub the picture sideways. It’s good to quilt the deposits, for example, drivers. Also, when paired with the Sysinternals Autoruns utility, you can determine at which stage of installation these and other modules are pulled.
Graph of demand acquisition for Windows 7 Enterprise x64 installed on a VMware virtual machine. Below is a vector image of the graph and a file in gml format, which you can use in any graph editor.